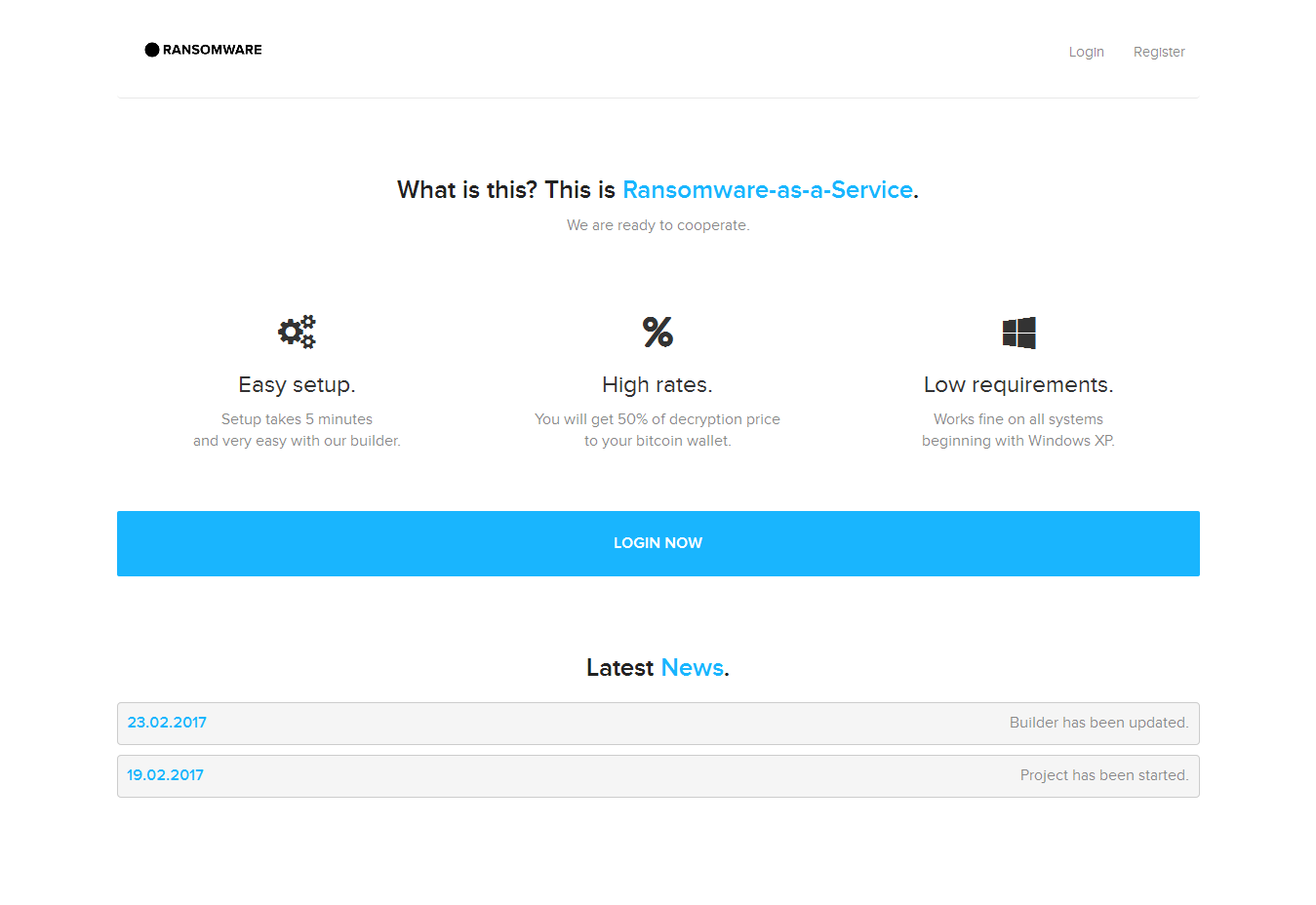
A new b -as-a-Service (RaaS) portal named Dot-Ransomware is behind the Unlock26 ransomware discovered this past week.
First spotted two days ago, this ransomware operation is quite unique as it features a very minimal and direct style, with little-to-no instructions and simple-designed ransom notes and ransom payment portal.
Based on two messages left on the Dot-Ransomware homepage, this entire operation launched on Tuesday, February 19, when the website was set up.
|
|
|
|
Anyone who registers on the service will be able to download two files. One is titled core.exe, which is the benign ransomware payload, while the second is builder.zip, an archive containing the builder and usage instructions (embedded in full at the end of the article).
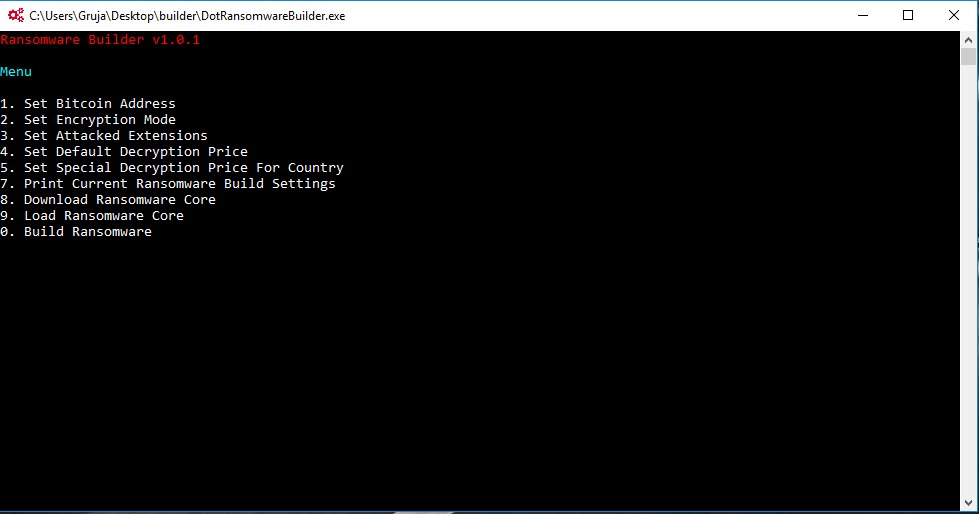
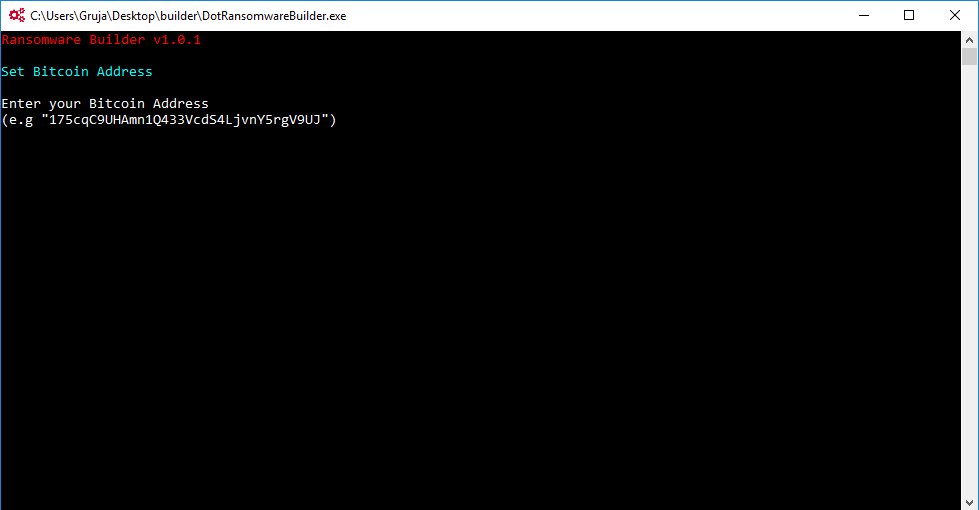
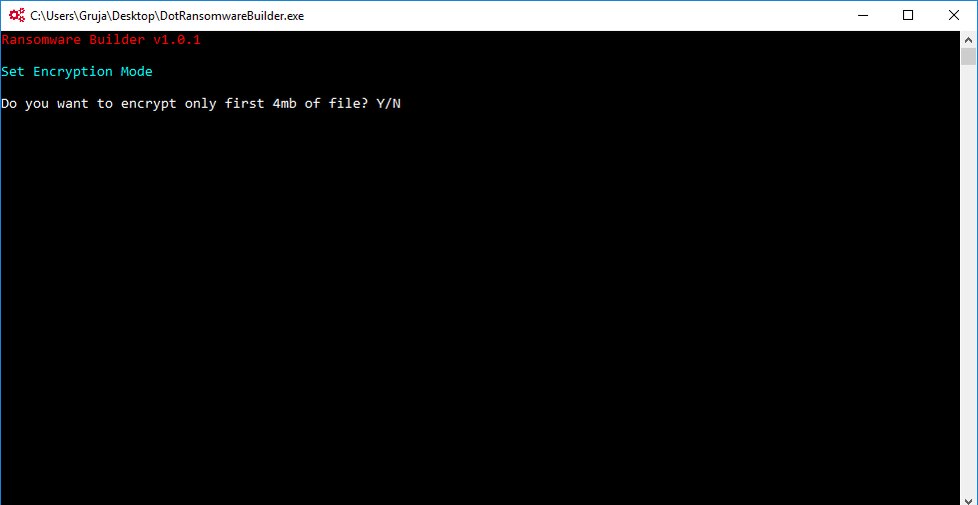
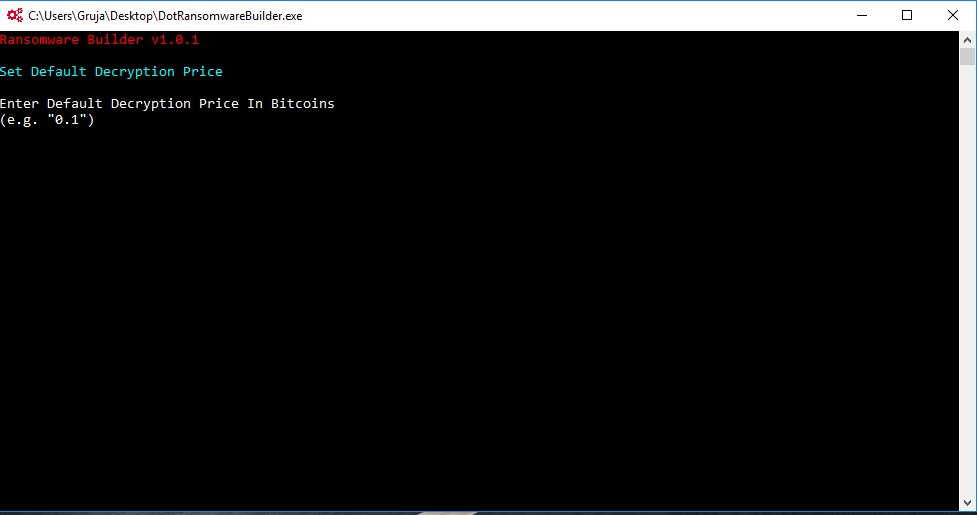
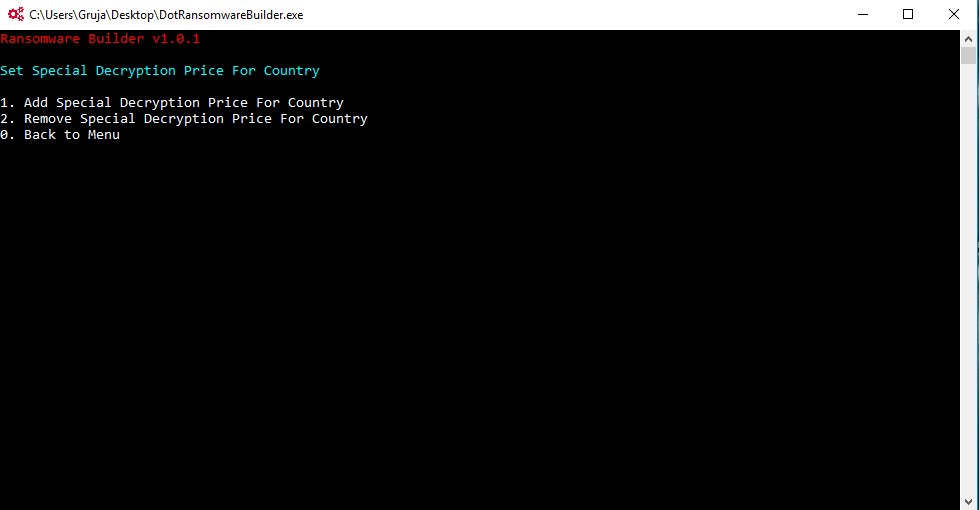
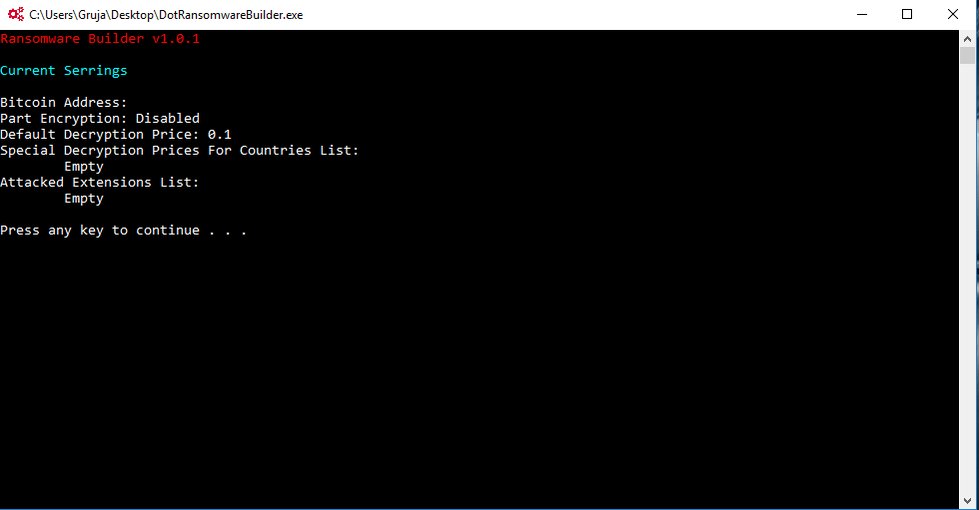
The builder is a minimal CLI tool that allows users to customize the following options:
- Ransomware decryption price
- Special decryption prices per country
- Extensions targeted for encryption
- The type of encryption (full or first 4MB of each file)
- The Bitcoin address where to send the crook’s 50% cut
|
|
|

|
|
|
|
|
|
According to the builder’s instructions file, users must load the core.exe file in the builder, which will then patch the file with the user’s custom settings, and generate a fully weaponized binary, ready for distribution.
The way each Dot-Ransomware user spreads this file is up to him. This may be malvertising, spam, or manual infections after brute-forcing RDP connections.
Unlock26 infection process
On the victim’s side, the newly-generated Unlock26 ransomware will encrypt the user’s files based on the internal configuration file, and append each locked file with a .locked-[XXX] extension, where XXX appear to be three random alpha-numeric characters unique for each victim.
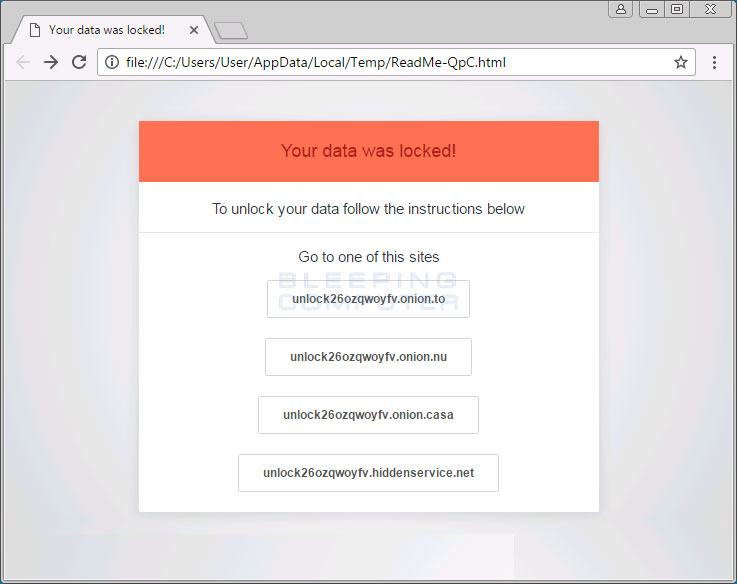
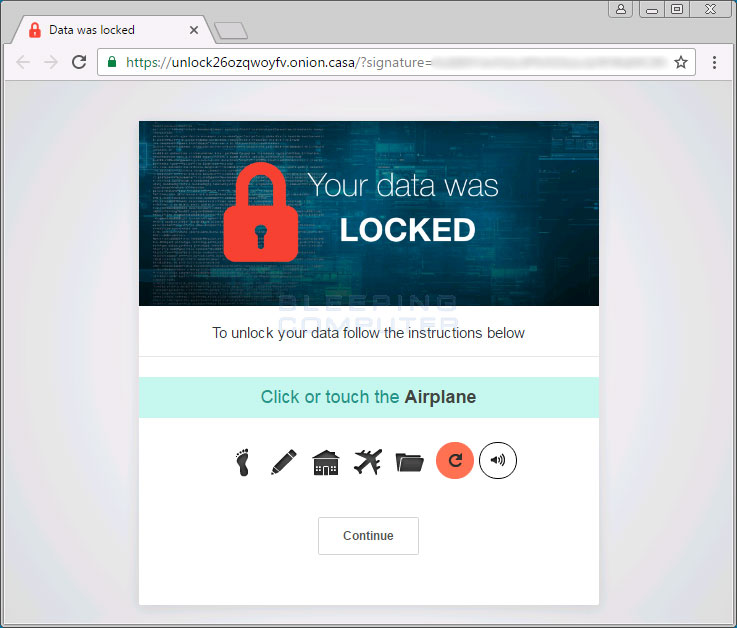
The last step in the infection process is to show the ransom note, which is simple and to the point, urging users to access one of four Tor-to-Web proxy URLs.
The first eight characters of the ransomware’s payment site is also from where the ransomware’s name came from, before researchers discovered and linked the ransomware with the Dot-Ransomware RaaS.
The links in the Unlock26 ransom note also hide a signature that allows crooks to distinguish between infected hosts.
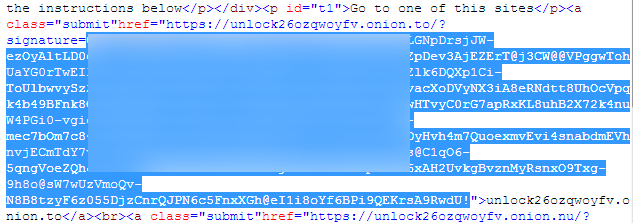
This means you have to click on the links from the ransom note itself. Typing the visible URLs manually in a browser won’t let you access the payment site, which checks for the presence of these signatures. We suspect the signatures are most likely used to display unique Bitcoin addresses for each user accessing the payment site.
Accessing the Unlock26 payment site we find the same simplistic style, lacking any kind of meaningful instructions.
From our analysis of this entire operation, it’s like the ransomware author is expecting everyone to know what to do, as if everyone gets infected with ransomware on a daily basis, and all users are tech-savvy PC veterans that know exactly what should happen next.
|
|
Dot-Ransomware, Unlock26 appear to be under development
But user instructions are not the only things missing from Dot-Ransomware and Unlock26.
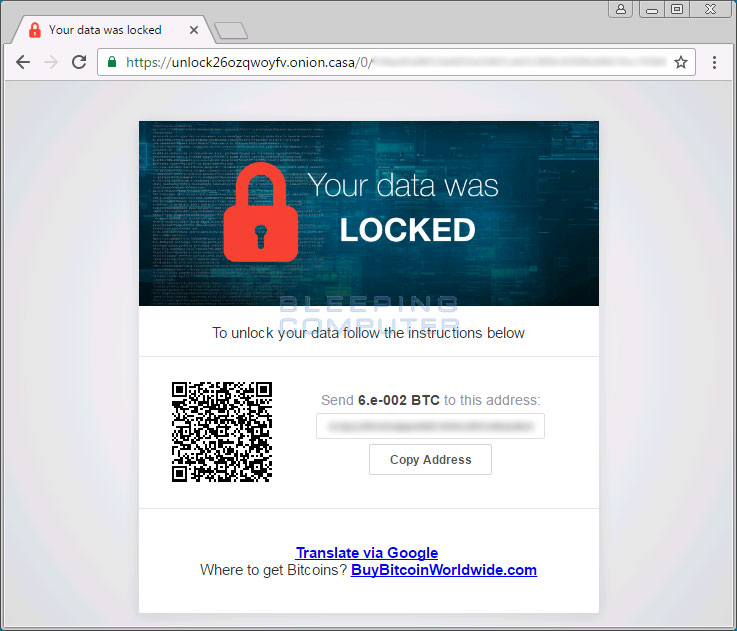
For example, if users wanted to pay, they wouldn’t even know the amount of Bitcoin they’d need to send, since the Unlock26 payment site doesn’t list the decryption price, but shows a math function instead: 6.e-002 BTC. This is weird, to say the least, unless you really want people not to pay the ransom.
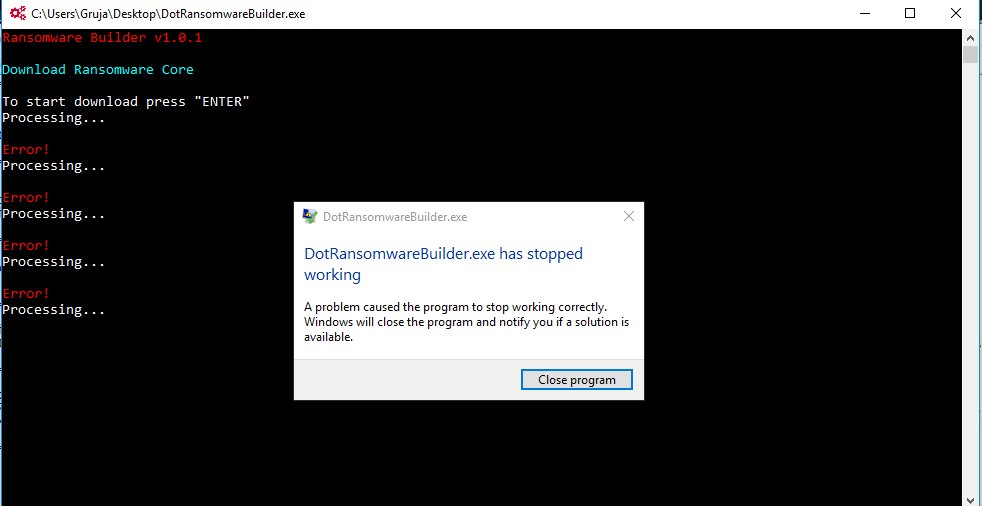
Putting this detail together with the error seen in one section of the builder (screenshot above), and with the fact that no users have reported Unlock26 infections as of now, we can say safely say this ransomware and its RaaS are still under development, and not yet ready to be deployed. Let’s hope its author gets bored in a few days and drops the service entirely, but we doubt it will happen after working so hard to reach this advanced stage of development.
Special thanks to MalwareHunter, who discovered the Unlock26 ransomware, David Montenegro, who discovered the Dot-Ransomware RaaS, Bleeping Computer’s Lawrence Abrams and GrujaRS, who helped with the analysis and info gathering.
IOCs
core.exe SHA256 hash:
db43d7c41da0223ada39d4f9e883611e733652194c347c78efcc439fde6dde1c
builder.zip SHA256 hash:
dd03307aa51cfb1c5a3c3fafc65729ad5b50a764354ef3919b7f9d0b4c6142a5
Ransom note:
Your data was locked!
To unlock your data follow the instructions below
Go to one of this sites
unlock26ozqwoyfv.onion.to
unlock26ozqwoyfv.onion.nu
unlock26ozqwoyfv.onion.casa
unlock26ozqwoyfv.hiddenservice.netBuilder ‘Setup Guide.txt’ file
================================================================================
====================================================
DotRansomware Setup Guide
====================================================
================================================================================
Attention!!!
We recommend you to build your ransomware inside virtual machine!
(But it is safe to use builder on your PC, just don't run builded exe file on your PC!)
================================================================================
Recommendation:
If you have got possibility to run ransomware on victim's computer with
administrator privileges then do it. Because it will provide better conversion.
================================================================================
Recommended decryption price:
0.1
================================================================================
Recommended special decryption prices:
FR|0.15|FI|0.15|IE|0.15|IS|0.15|AU|0.15|BE|0.15|CA|0.15|AT|0.15|DK|0.15|SE|0.15|DE|0.15|NL|0.15|SA|0.2|US|0.2|HK|0.2|LU|0.2|CH|0.2|NO|0.2|AE|0.2|SG|0.2|KW|0.2|MO|0.2|QA|0.2
================================================================================
Recommended attacked extensions:
001|1dc|3ds|3fr|7z|a3s|acb|acbl|accdb|act|ai|ai3|ai4|ai5|ai6|ai7|ai8|aia|aif|aiff|aip|ait|anim|apk|arch00|ari|art|arw|asc|ase|asef|asp|aspx|asset|avi|bar|bak|bay|bc6|bc7|bgeo|big|bik|bkf|bkp|blob|bmp|bsa|c|c4d|cap|cas|catpart|catproduct|cdr|cef|cer|cfr|cgm|cha|chr|cld|clx|cpp|cr2|crt|crw|cs|css|csv|cxx|d3dbsp|das|dayzprofile|dazip|db|db0|dbf|dbfv|dcr|dcs|der|desc|dib|dlc|dle|dlv|dlv3|dlv4|dmp|dng|doc|docm|docx|drf|dvi|dvr|dwf|dwg|dxf|dxg|eip|emf|emz|epf|epk|eps|eps2|eps3|epsf|epsp|erf|esm|fbx|ff|fff|fh10|fh11|fh7|fh8|fh9|fig|flt|flv|fmod|forge|fos|fpk|fsh|ft8|fxg|gdb|ge2|geo|gho|h|hip|hipnc|hkdb|hkx|hplg|hpp|hvpl|hxx|iam|ibank|icb|icxs|idea|iff|iiq|indd|ipt|iros|irs|itdb|itl|itm|iwd|iwi|j2k|java|jp2|jpe|jpeg|jpf|jpg|jpx|js|k25|kdb|kdc|kf|kys|layout|lbf|lex|litemod|lrf|ltx|lvl|m|m2|m2t|m2ts|m3u|m4a|m4v|ma|map|mat|mb|mcfi|mcfp|mcgame|mcmeta|mdb|mdbackup|mdc|mddata|mdf|mdl|mdlp|mef|mel|menu|mkv|mll|mlx|mn|model|mos|mp|mp4|mpqge|mrw|mrwref|mts|mu|mxf|nb|ncf|nef|nrw|ntl|obm|ocdc|odb|odc|odm|odp|ods|odt|omeg|orf|ott|p12|p7b|p7c|pak|pct|pcx|pdd|pdf|pef|pem|pfx|php|php4|php5|pic|picnc|pkpass|png|ppd|ppt|pptm|pptx|prj|prt|prtl|ps|psb|psd|psf|psid|psk|psq|pst|ptl|ptx|pwl|pxn|pxr|py|qdf|qic|r3d|raa|raf|rar|raw|rb|re4|rgss3a|rim|rofl|rtf|rtg|rvt|rw2|rwl|rwz|sav|sb|sbx|sc2save|shp|sid|sidd|sidn|sie|sis|skl|skp|sldasm|sldprt|slm|slx|slxp|snx|soft|sqlite|sqlite3|sr2|srf|srw|step|stl|stp|sum|svg|svgz|swatch|syncdb|t12|t13|tax|tex|tga|tif|tiff|tor|txt|unity3d|uof|uos|upk|vda|vdf|vfl|vfs0|vpk|vpp_pc|vst|vtf|w3x|wb2|wdx|wma|wmo|wmv|wallet|ycbcra|wotreplay|wpd|wps|x3f|xf|xl|xlk|xls|xlsb|xlsm|xlsx|xvc|xvz|xxx|zdct|zip|ztmp|py|rb|tar|gz|sdf|yuv|max|wav|dat
================================================================================
Recommendation:
You need to test builded exe file inside virtual machine, because operability can be broken after crypt/pack of core!
================================================================================
Links to website:
dot2cgpiwzpmwtuh.onion.to
dot2cgpiwzpmwtuh.onion.nu
dot2cgpiwzpmwtuh.hiddenservice.net
dot2cgpiwzpmwtuh.onion.casa
dot2cgpiwzpmwtuh.onionSource:https://www.bleepingcomputer.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











