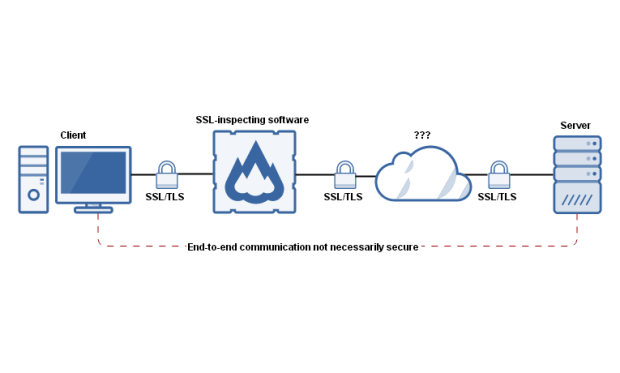
In an advisory sent to enterprises across the US, the Department of Homeland Security’s US-CERT group is warning that security products which perform HTTPS interception might weaken a company’s overall security.
HTTPS inspection is a method where security products set up a man-in-the-middle proxy for HTTPS traffic. The proxy stands between the client and the remote server and intercepts HTTPS traffic, inspecting it for malware, and rebuilding the connection.
The issue comes from the fact that many security products, such as firewalls or antivirus products, fail to reconstruct the SSL connections to the same standards clients and servers negotiated.
“Many HTTPS inspection products do not properly verify the certificate chain of the server before re-encrypting and forwarding client data, allowing the possibility of a MiTM attack,” US-CERT wrote in its advisory. “Furthermore, certificate-chain verification errors are infrequently forwarded to the client, leading a client to believe that operations were performed as intended with the correct server.”
Research paper triggered CERT warning
The CERT advisory came after a group of security experts published a research paper at the start of the month titled “The Security Impact of HTTPS Interception.”
The research team, made up of experts from Google, Mozilla, Cloudflare, and the University of Michigan, showed that around 62% of the HTTPS connections they’ve studied featured “reduced security,” while 58% contained “severe vulnerabilities.”
“We investigated popular antivirus and corporate proxies, finding that nearly all reduce connection security and that many introduce
vulnerabilities (e.g., fail to validate certificates),” the researchers concluded in their paper.
“While the security community has long known that security products intercept connections, we have largely ignored the issue, believing that only a small fraction of connections are affected. However, we find that interception has become startlingly widespread and with worrying consequences.”
Will Dormann, a vulnerability analyst for US-CERT has also published a blog post detailing the dangers of improper HTTPS interception, and highlighted possible issues such as:
Incomplete validation of upstream certificate validity
Not conveying validation of upstream certificate to the client
Overloading of certificate Canonical Name (CN) field
Use of the application layer to convey certificate validity
Use of a User-Agent HTTP header to determine when to validate a certificate
Communication before warning
Same root CA certificate
Companies that want to test if their HTTPS inspection tools weaken HTTPS security can do so by using the BadSSL service.
Dormann also published a list of security products that perform HTTPS interception and may be possibly affected.
A10 vThunder
Arbor Networks Pravail
Baracuda Web Filter
BASCOM School Web Filter
Bloxx Web Filter
Blue Coat SSL Visibility Appliance
Check Point Data Loss Prevention (DLP), Anti Virus, Anti-Bot, Application Control, URL Filtering, Threat Emulation and IPS.
Cisco ScanCenter
Citrix NetScaler AppFirewall
Clearswift SECURE Web Gateway
ContentKeeper
Cymphonix Internet Management Suite
Dell SonicWALL
EdgeWave iPrism Web Security
ESET Smart Security
F5 BIG-IP
Fortinet FortiGate
Fidelis Security XPS
Finjan Vital Security
GFI WebMonitor
GigaMon GigaSmart
IBM Security Network Protection
iboss Web Security
iSHERIFF Cloud Security
Juniper IDP devices
Kaspersky Anti-Virus
Komodia SSL Decoder
M86 Secure Web Gatewayr
McAfee Web Gateway and Firewall Enterpriser
Microsoft Forefront TMG
NetNanny
NextGig Netronome
Optenet WebFilter
Palo Alto PAN-OS
Panda Cloud Internet Protection
PrivDog
Radware AppXcel
SafeNet eSafe Web Security Gateway
Sangfor IAM
Smoothwall Secure Web Gateway
Sophos Cyberoam
Sourcefire SSL Appliance
Squid
Symantec Web Gateway
Thomason Technologies Next Gen IPS
Trend Micro Deep Security
Trustwave WebMarshal, Secure Web Gateway
Untangle NG Firewall
Venafi TrustAuthority
VSS Monitoring vInspector
WatchGuard HTTPS Proxy
Wavecrest CyBlock
WebSense Content Gateway
WebTitan
Qbik WinGate
WolfSSL SSL Inspection
Zscaler
ZyXel Firewall

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.