LastPass says it patched one of two separate bugs that affected its Chrome and Firefox browser extensions, which if exploited, would have allowed a third-party to extract passwords from users visiting a malicious website.
Both bugs were discovered by Tavis Ormandy, a security researcher working for Google’s Project Zero.
Of the two bugs Ormandy discovered, LastPass engineers patched only the one affecting the Chrome extension, while the one affecting the Firefox version is under investigation.
Bug in LastPass Chrome extension
The vulnerability affecting the LastPass Chrome extension can be exploited by attacking an intermediary JS script that stands between the user’s browser and the LastPass cloud service, where the company stores user passwords.
“It’s possible to proxy untrusted messages to LastPass 4.1.42 due to a bug, allowing websites to access internal privileged RPCs (Remote Procedure Calls). ” Ormandy explained. “There are a lot of RPCs, allowing complete control of the LastPass extension, including stealing passwords. If you have the ‘Binary Component’ installed, this even allows arbitrary code execution.”
Ormandy put together proof-of-concept code that executes code on a user’s machine via this intermediary script and launches an instance of the Windows Calculator. All OS platforms are affected, not just Chrome on Windows.
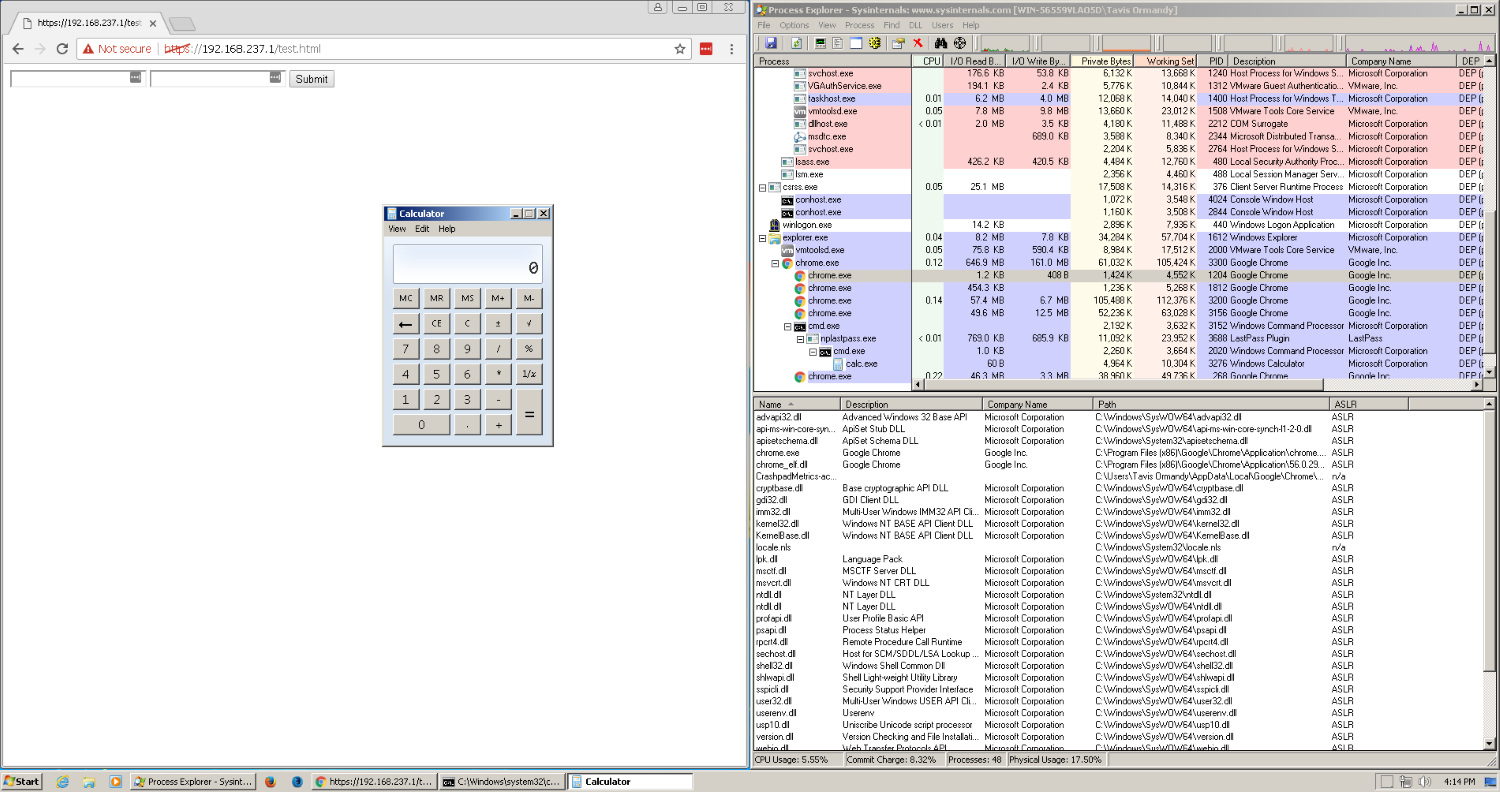
This PoC code can be altered to steal user passwords before they are copied and filled inside username and password fields.
LastPass users are exposed to simple attack vectors, as attackers can host the weaponized code as a regular JS script on a website.
On Twitter, LastPass said they already fixed the issue reported by Ormandy in the Chrome extension and promised a blog post with more details in the following days.
Bug in LastPass Firefox extension
The second bug Ormandy discovered affects LastPass’s Firefox add-on version 3.3.2 only. LastPass told Ormandy that version 3.3.2 is their most popular version.
Despite this, two weeks ago, LastPass announced they were retiring the LastPass Firefox add-on v3.3.2 because of Firefox’s future plans to drop the old Add-ons API and move to a new system they call WebExtensions.
The LastPass Chrome and Firefox extensions don’t use the same version numbers, and the v3 on Firefox is the stable branch.
Ormandy didn’t provide details about how this bug works, but said that attackers can steal user credentials from LastPass password vaults using a similar Web-based exploit that relies on attackers luring users to a malicious website. The researcher also confirmed the issue was not resolved.
More details are expected to become available in this bug report after LastPass fixes the vulnerability.
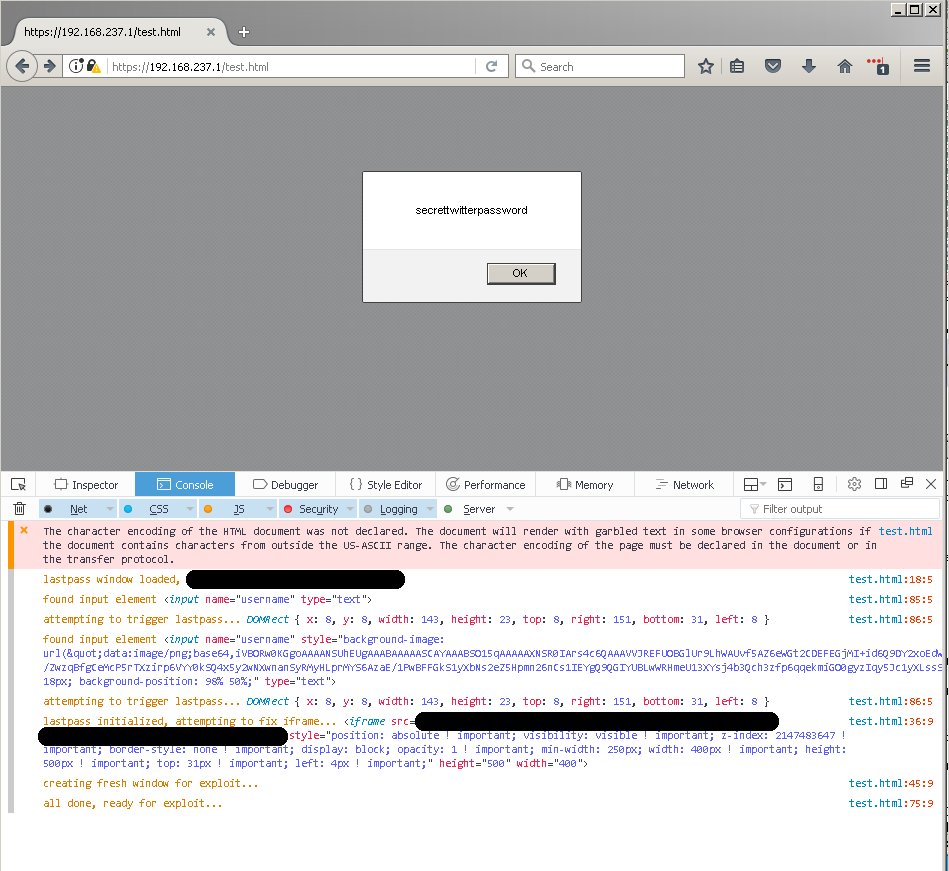
In July 2016, Ormandy found a similar bug that allowed attackers to extract passwords from LastPass. On the same day, Mathias Karlsson of Detectify found and disclosed a different issue, wich also led to a full password compromise.
In April 2016, Malwarebytes found a fake LastPass Chrome extension offered via the official Google Web Store.
In January 2016, security researcher Sean Cassidy developed a simple attack to collect LastPass master passwords.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











