Apple fixes flaw attackers used to trick uninformed users into paying a fine. Ransomware scammers have been exploiting a flaw in Apple’s Mobile Safari browser in a campaign to extort fees from uninformed users. The scammers particularly target those who viewed porn or other controversial content. Apple patched the vulnerability on Monday with the release of iOS version 10.3.
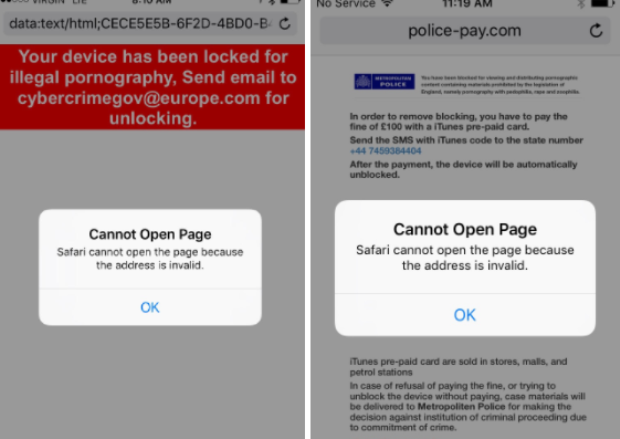
The flaw involved the way that Safari displayed JavaScript pop-up windows. In a blog post published Monday afternoon, researchers from mobile-security provider Lookout described how exploit code surreptitiously planted on multiple websites caused an endless loop of windows to be displayed in a way that prevented the browser from being used. The attacker websites posed as law-enforcement actions and falsely claimed that the only way users could regain use of their browser was to pay a fine in the form of an iTunes gift card code to be delivered by text message. In fact, recovering from the pop-up loop was as easy as going into the device settings and clearing the browser cache. This simple fix was possibly lost on some uninformed targets who were too uncomfortable to ask for outside help.
“The attackers effectively used fear as a factor to get what they wanted before the victim realized that there was little actual risk,” Lookout researchers Andrew Blaich and Jeremy Richards wrote in Monday’s post.
Blaich and Richards said they first learned of the attacks when someone using iOS version 10.2 reported losing control of Safari after visiting the website pay-police[.]com. The user provided the screenshot shown above, which attempts to instill fear with the claim the device was being locked “for illegal pornography.” Below those words was a pop-up Window that said “Cannot Open Page.” Each time the person clicked on the accompanying OK button, a new window would open again.
The JavaScript used in the attack shows signs of being used to exploit the same Safari flaw present in iOS version 8, which was released in 2014. The attackers, the Lookout researchers said, purchased a large number of domains in an attempt to “catch users that are seeking controversial content on the internet and coerce them into paying a ransom to them.” Sites tailored the messages they delivered based on country identifiers. iOS users who are hit by the scam can clear their browsing cache by going into settings > Safari > Clear History and Website Data.
The campaign in many respects resembles one that hit Android users in 2014. That one demanded a $300 ransom paid in the form of mechanisms such as Paysafecard or uKash.
Source:https://arstechnica.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.