A new ransomware called Mole was found by security researcher Brad Duncan while he was analyzing a new SPAM campaign. After examining this sample, I feel that this is probably another variant of the CryptoMix family as it has many similarities to the Revenge and CryptoShield variants.
As a note, in this article I will be referring to this infection as the Mole Ransomware as that will most likely be how the victim’s refer to it. It is important to remember, though, that this ransomware is not a brand new infection, but rather a new version of the CryptoMix ransomware family.
How Victim’s Become Infected with the Mole Ransomware
Mole is currently being distributed through SPAM emails that pretend to be shipping notifications. These emails state that a package could not be delivered and then displays a link to a site where additional information. An example of one of these SPAM emails can be seen below. A full list of SPAM subjects that were compiled by Brad Duncan can be found below and a list of current download links is in Brad’s article.
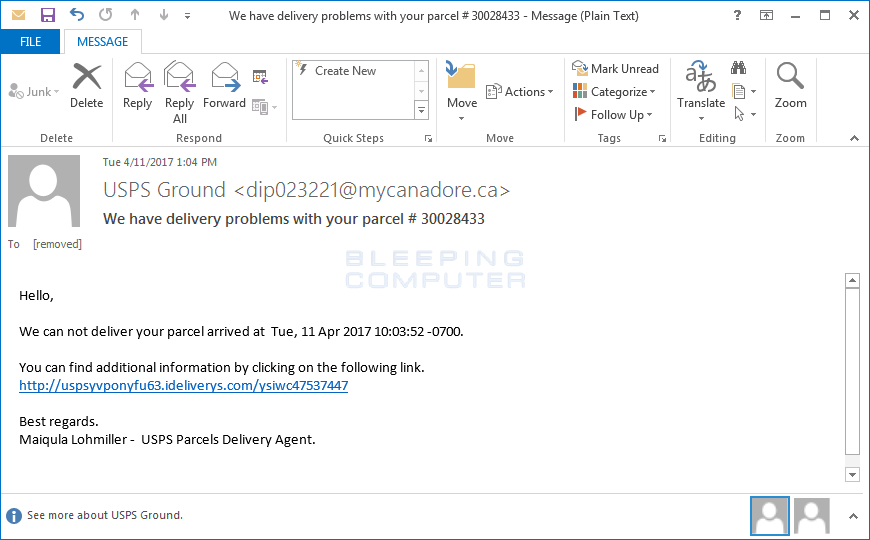
Source: BroadAnalysis.com
When a user clicks on the enclosed link, it will redirect to a fake Microsoft Word Online site that displays a supposedly unreadable document. This page then states that the document cannot be read in the browser and that the victim needs to download and install a plugin. You can see an example of the fake word online doc below.
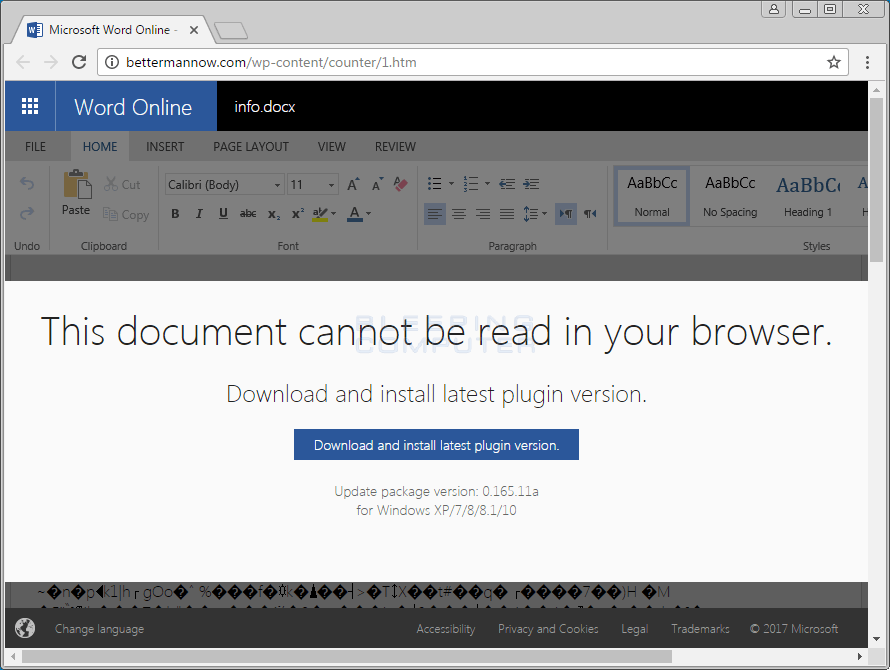
If the user clicks on the download button, it will download a file named plugin-office.exe or pluginoffice.exe. If these files are executed, the Mole Ransomware will be installed.
How the Mole Ransomware Encrypts a Victim’s Files
Once the ransomware executable is downloaded and executed on the victim’s computer, it will display a fake alert that states: This fake alert is designed to coerce a victim into clicking Yes at a UAC prompt so the ransomware runs with administrative privileges. The text of this alert is:
Display Color Calibration can't turn off Windows calibration management.
Access is denied.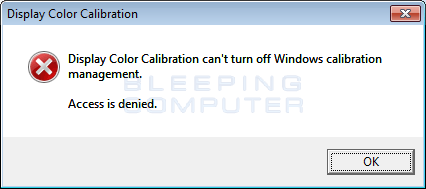
Once you press OK button in the above prompt, you will be presented with a User Account Control prompt, which asks if you wish to allow the command “C:\Windows\SysWOW64\wbem\WMIC.exe” process call create “%UserProfile%\pluginoffice.exe” to execute.
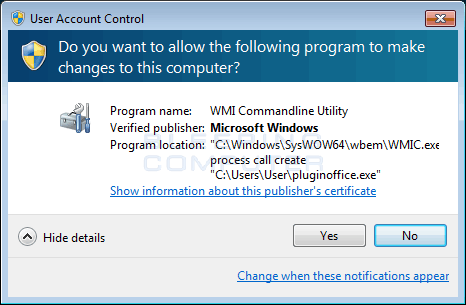
Once the victim clicks on Yes, the ransomware will launch again with administrative privileges and generate a unique hexadecimal ID for the victim. This ID will then be submitted to a Command & Control server, which will respond with a RSA-1024 public encryption key. This key will be used by the ransomware to encrypt the AES encryption key used to encrypt the files. This RSA key will be saved in the file %UserProfile%\AppData\Roaming\26E14BA00B70A5D0AE4EBAD33D3416B0.MOLE.
Below is the current RSA public key.
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCE5+kCm02LQPVKdMT8OyzAKsagRFk3KL4UXuBb7OGYzinEX7y3LQEbWc/49jbnSaFZAm1ucIXK2CPrgC0g4FolRSH7IZ5TJuC3cgJZYN4uCP8z44zVk3wWloX9suVaRmvqxtkCm4nMR0JsR+3YbcB8ABMs
pUOBAHv+DlbcagmMbQIDAQAB
-----END PUBLIC KEY-----Mole will then stop the following services:
sc stop wscsvc
sc stop WinDefend
sc stop wuauserv
sc stop BITS
sc stop ERSvc
sc stop WerSvcThen it will issue the following commands to disable the Windows startup recovery and to clear the Windows Shadow Volume Copies.
vssadmin.exe Delete Shadows /All /Quiet
bcdedit /set {default} recoveryenabled No
bcdedit /set {default} bootstatuspolicy ignoreallfailuresFinally, the infection will scan the computer for targeted files and encrypt them. When Mole encounters a targeted file it will encrypt it using AES-256 encryption, rename the file, and then append the .Mole extension to the encrypted file. The format for a renamed file is [36_hex_chars].Mole. For example, a file called test.jpg would be encrypted and renamed as something like 4E47636C1F31519446A78F711F4A1670.MOLE.
In each folder that Mole encrypts a file, it will also create a ransom note named INSTRUCTION_FOR_HELPING_FILE_RECOVERY.TXT. Unlike most other ransomware infections, Mole does not create a HTML variant of the ransom note.

When the encryption process is finished, Mole Ransomware will display the ransom note .
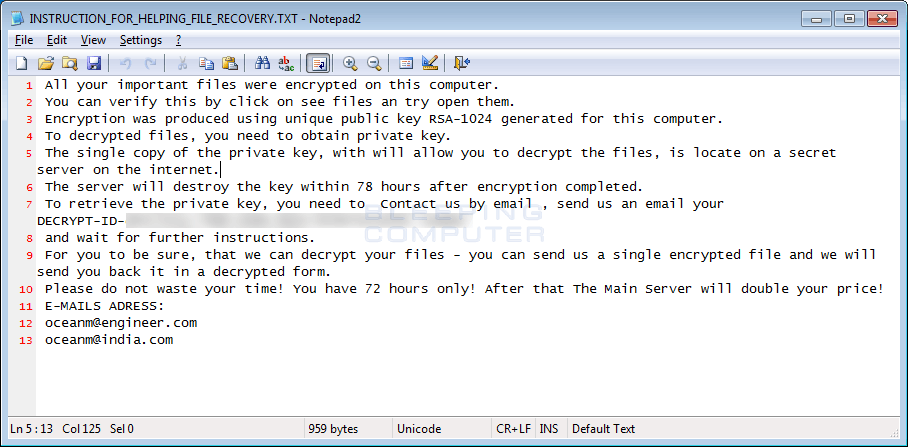
This ransom note contains information regarding what happened to your files, a personal identification ID, and two email addresses that can be used to contact the ransom developer for payment instructions. The current email addresses are oceanm@engineer.com and oceanm@india.com. Of interest is that Revenge ransomware had a contact email of Mole00@writeme.com. Coincidence?
Unfortunately, at this time there is no way to currently decrypt files encrypted by Mole for free. For those who wish to discuss this ransomware or receive support, you can always use our CryptoMix or CrypMix Ransomware Help Topic.
File Associated with the Mole Ransomware Variant:
plugin-office.exe
pluginoffice.exe
%UserProfile%\AppData\Roaming\0ABCF2F2.exe
%UserProfile%\AppData\Roaming\26E14BA00B70A5D0AE4EBAD33D3416B0.MOLE
INSTRUCTION_FOR_HELPING_FILE_RECOVERY.TXT
Mole Ransomware Hashes:
SHA256: 5ca18c9f5ec26a30de429accf60fc08b0ef785810db173dd65c981a550010dde - pluginoffice.exe
SHA256: e6591a9389c7b82d59949b8c5660e773b86dff1fa3909f780cb8c88bbc85646c - plugin-office.exe
Samples from: https://isc.sans.edu/forums/diary/Malspam+on+20170411+pushes+yet+another+ransomware+variant/22290/Mole Ransomware Network Communication:
212.47.254.187/scripts/superfish/js/supersubs.phpExample Mole Ransom Note Text:
All your important files were encrypted on this computer.
You can verify this by click on see files an try open them.
Encryption was produced using unique public key RSA-1024 generated for this computer.
To decrypted files, you need to obtain private key.
The single copy of the private key, with will allow you to decrypt the files, is locate on a secret server on the internet.
The server will destroy the key within 78 hours after encryption completed.
To retrieve the private key, you need to Contact us by email , send us an email your DECRYPT-ID-11111111-1111-1111-1111-111111111111 number
and wait for further instructions.
For you to be sure, that we can decrypt your files - you can send us a single encrypted file and we will send you back it in a decrypted form.
Please do not waste your time! You have 72 hours only! After that The Main Server will double your price!
E-MAILS ADRESS:
oceanm@engineer.com
oceanm@india.comMole Ransomware Associated Emails:
oceanm@engineer.com
oceanm@india.comSPAM Email Subjects:
Delivery problem, parcel USPS #07681136
Delivery problem, parcel USPS #766268001
Delivery problem, parcel USPS #886315525
New status of your USPS delivery code: 74206300
New status of your USPS delivery code: 573677337
New status of your USPS delivery code: 615510620
Our USPS courier can not contact you parcel # 754277860
Please recheck your delivery address USPS parcel 67537460
Please recheck your delivery address USPS parcel 045078181
Re:
Status of your USPS delivery ID: 45841802
We have delivery problems with your parcel # 30028433
We have delivery problems with your parcel # 48853542
We have delivery problems with your parcel # 460730503
Compiled by Brad Duncan at: https://isc.sans.edu/forums/diary/Malspam+on+20170411+pushes+yet+another+ransomware+variant/22290/Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











