Someone has created a new Remote Access Trojan (RAT) that uses the Telegram protocol to steal user data from infected devices.
The RAT is written in Python and is currently available as a free download on a public code sharing portal.
The RAT’s author, whose name we won’t be sharing, claims to have embarked into creating this tool as a way to improve how most of today’s RATs work.
The author highlights that the biggest problem with most RATs is that they don’t use encryption and require that the attacker enable port forwarding on the victim’s machine to control infected hosts.
The developer proposes his own tool, named RATAtack, which uses the Telegram protocol to support an encrypted channel between victims and their master, and does not need port forwarding, as the Telegram protocol also provides a simple method to communicate to the target without configuring port forward beforehand on the target.
RAT is powered via Telegram bots
Before deploying RATAttack, the RAT owner must create a Telegram bot, take the bot’s Telegram token, and embed it into the RAT’s config file. After infecting victims with RATAttack payloads, all hosts will connect to this bot’s Telegram channel.
The RATAttack owner can come later, connect to the same channel, and use simple instructions to manage RATAttack clients on the infected hosts. According to the current RATAttack version, the following commands are supported:
/pc_info - PC information
/msg_box - display message box with text
/snapshot - take picture with webcam
/ip_info - via ipinfo.io
/download_file - download file from target
/list_dir - list contents of directory
/run_file - run a file on target
/capture_pc - screenshot PC
/keylogs - get keylogs
/self_destruct - destroy all traces from target PC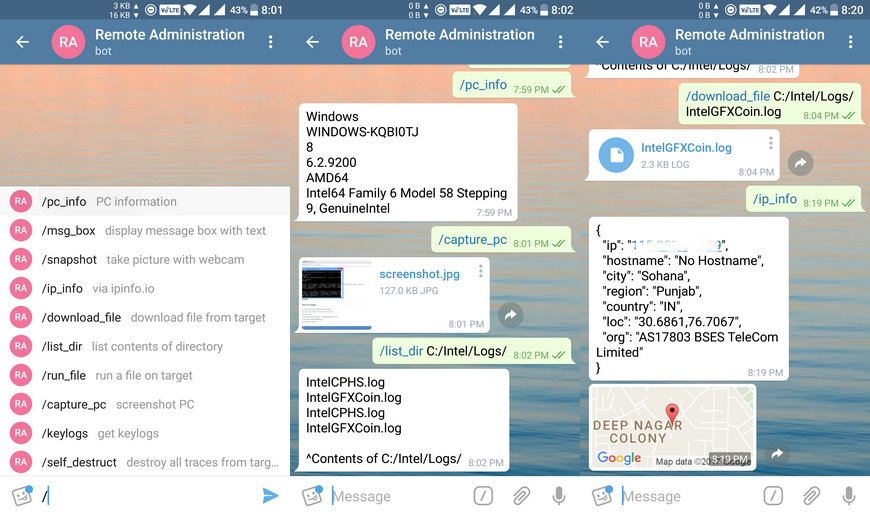
Below are some of RATAttack’s current and work-in-progress [WIP] features.
Get target PC’s Windows version, processor and more.
Get target PC’s IP address information and approximate location on map.
Show message box with custom text on target PC (Thanks mvrozanti!)
List any directories on the target.
Download any file locally from the target PC in the background.
Upload local files on to the target PC. Send your image, pdf, exe or anything as file to the Telegram bot.
Screenshots of the target PC.
Execute any file on the target PC.
[WIP] Self-Destruct RAT on the target PC.
[WIP] Take snapshots from the webcam (if attached).
[WIP] Copy and Move files on the target PC.
[WIP] Delete files on the target PC.
RATAttack was coded in Python 2.x, but its author promised a version for Python 3.x as well.
The mythical “disclaimer” will keep the bad guys away
Just like most misguided developers who create dual-use RATs, the developer calls his creation a Remote Administration Tool, even if some of the features he’s currently working on are usually found in malicious trojans, and not legitimate remote admin tools such as Teamviewer and others.
The dev also didn’t forget to slap the classic and now obligatory “disclaimer” at the end of RATAttack’s description, hoping to absolve himself of any wrong-doing others will do when they take his open-sourced code and use it to spy on their spouses, hack companies, or keep dissidents under surveillance.
This tool is supposed to be used only on authorized systems. Any unauthorized use of this tool without explicit permission is illegal.
The case of dual-use software, used for legitimate and malicious purposes, has been recently debated in the news. A point of view that supports RAT coders is expressed in an article called “FBI Arrests Hacker Who Hacked No One,” while infosec journalist Brian Krebs provided a counterpoint in an article called “Dual-Use Software Criminal Case Not So Novel.”
Both are must-read articles in understanding why you can’t fool authorities by calling your software a Remote Administration Tool if you include malware-specific features and also advertise your RAT on underground hacking forums.
Based on Bleeping Computer’s scans, RATAttack wasn’t advertised on any hacking forums, and its author only appears to have dumped the code on GitHub (for now). Based on our experience, it’s only a matter of time until we’ll see it in live malware campaigns.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











