The developer of the AES-NI ransomware claims that the recent “success” he’s been enjoying is due to the NSA exploits leaked last week by the Shadow Brokers group.
In a series of tweets he posted online, the AES-NI author alleges he successfully used ETERNALBLUE, an exploit targeting the SMBv2 protocol, to infect Windows servers across the globe and then install his home-made ransomware.
The only evidence the AES-NI author provided was a screenshot that showed the ransomware dev scanning a server for three NSA exploits.
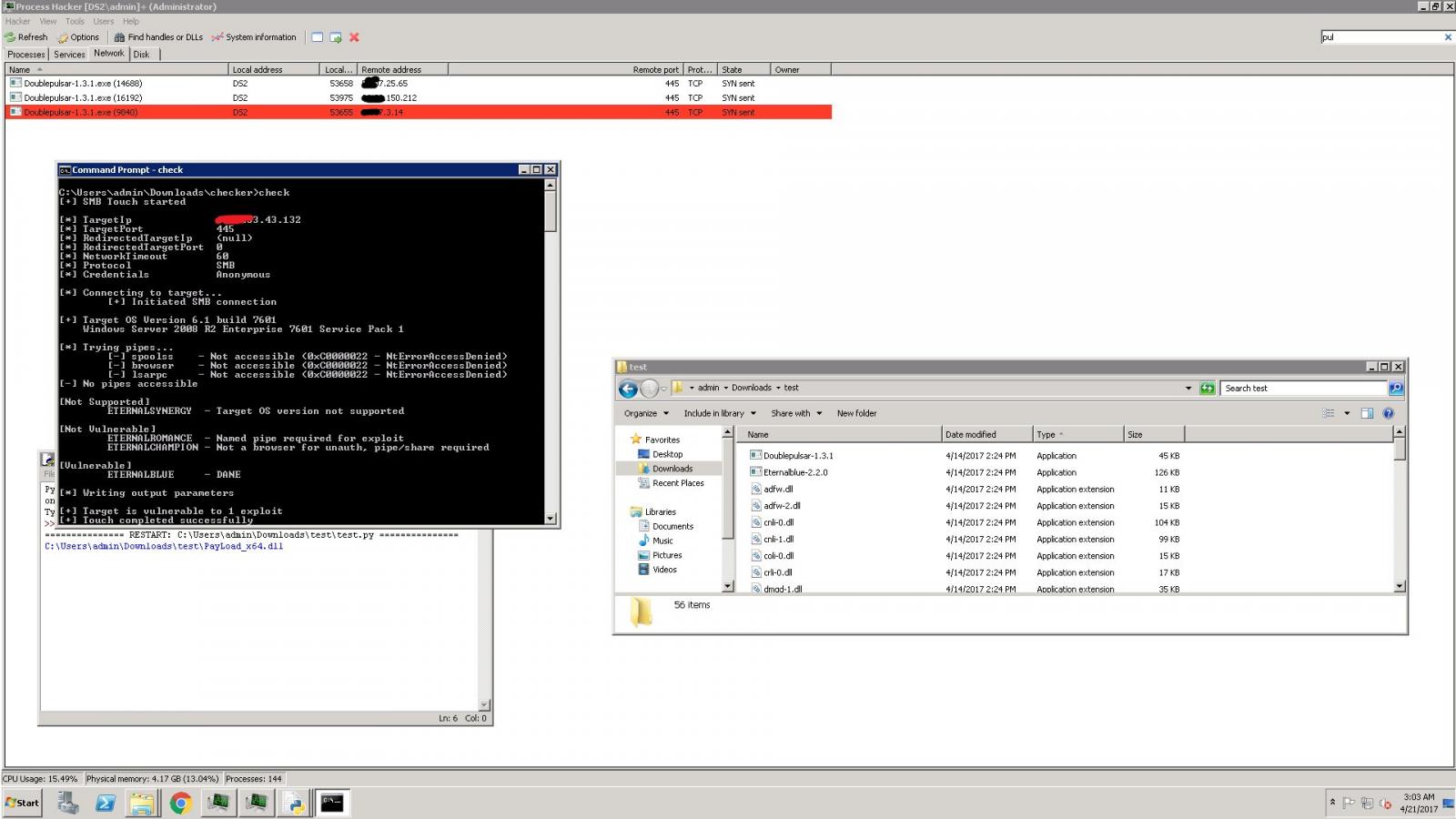
The author of this ransomware did not respond to a request for comment from Bleeping Computer. While the validity of his claims cannot be proven, one thing can, and that’s the trail of destruction this ransomware has left behind in the past week.
Below is a chart provided by the experts at ID-Ransomware, a service that helps users identify the type of ransomware that has infected their computers. These detections are logged for the purpose of keeping track of ransomware activity and detecting any new trends.
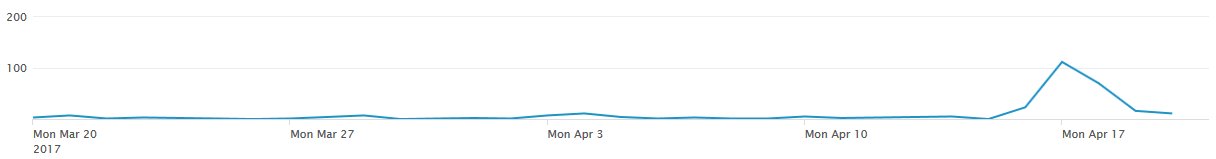
The chart above shows daily detections that varied between 0 and 5 infected hosts per day, and a huge spike over the weekend, culminating on Monday with over 100 victims.
The spike in activity came after The Shadow Brokers leaked a trove of Windows exploits last Friday. Included in the leak was FuzzBunch, a Metasploit-like exploitation framework, and over 20 Windows exploits, mostly targeting the SMB protocol.
Researchers believe the ransomware dev is lying
While the AES-NI ransomware creator alludes he is using ETERNALBLUE to crack into Windows servers with SMB ports left open to the Internet, several security experts have doubted his claim.
“They’re getting inside networks using RDP,” infosec expert Kevin Beaumont told Bleeping Computer, “and then using RDP to move around.” Beaumont shared the same thoughts on Twitter.
An Emsisoft researcher that goes by the nickname of Polar Toffee also believes the victims were hacked via RDP (brute-force attack on weakly secured user accounts), and then the attacker installed the AES-NI ransomware on their computer or local server.
Security expert MalwareHunter also doubts the group used NSA exploits leaked by the Shadow Brokers to infect victims. “If you see the end of the graph, it is going back to an average number. So anything he used, it was only good for a few days,” MalwareHunter told Bleeping Computer.
Nonetheless, that dip in activity can also be explained. In a tweet, the AES-NI developer alluded that someone had reported and taken down one of the email addresses he used to handle ransom payments. This stopped him from servicing around 2,000 clients and might have hampered his operations, at least for the time being.
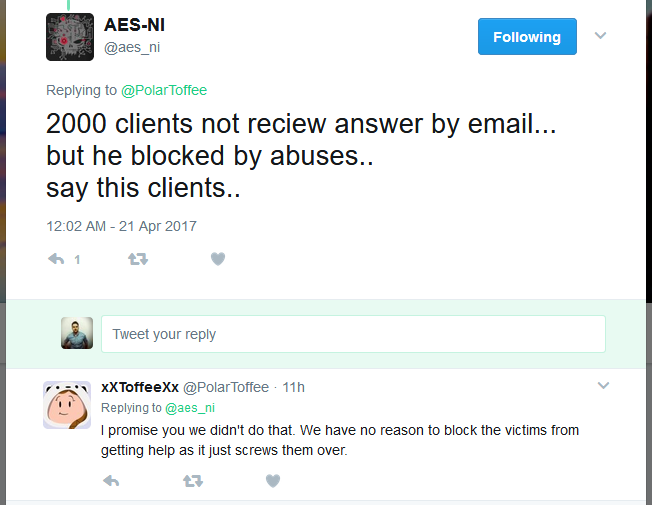
Based on current evidence, the AES-NI ransomware has caused a whole lot of damage over the weekend, NSA exploits or not. Other Internet discussion boards and the Bleeping Computer forum have come alive with new AES-NI victims asking for help.
Most victims came to the Bleeping Computer forums because the author gave out specific instructions in the AES-NI ransom note, promising to keep an eye on the forum and provide help, if needed.
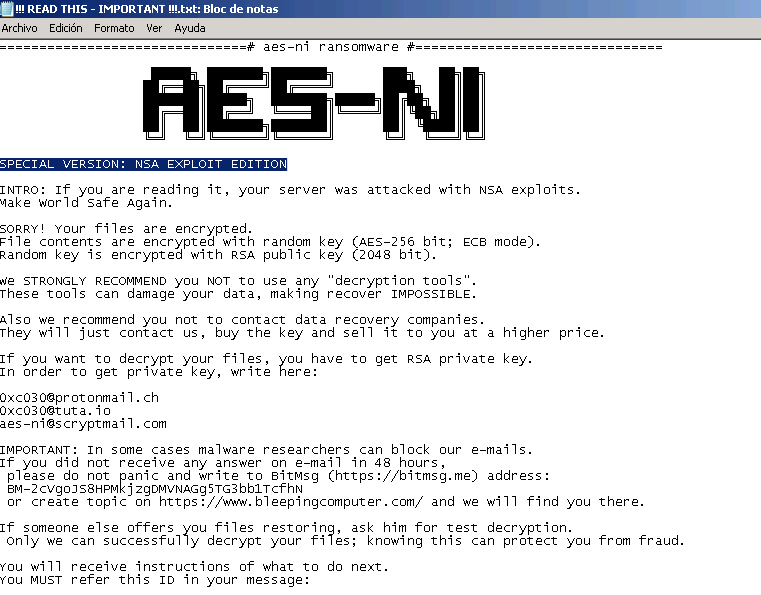
This particular ransomware has been around since December 2016 and has been known under two other names: AES Ransomware and AES256 Ransomware.
It only recently rebranded to AES-NI Ransomware, and starting last Friday, the ransom note has been advertising this as the “NSA EXPLOIT EDITION.” The current version asks for a ransom of 1.5 Bitcoin (~$1,800) and will decrypt files for free for any victims from former Soviet states, according to Russian security expert Andrew Ivanov. Unfortunately, there is no known way to decrypt files encrypted by AES-NI ransomware at the moment of writing, other than paying the ransom.
Microsoft patches for NSA exploits are already available
Right now, the simplest way to avoid falling victim to AES-NI attacks is to block external traffic to SMB and RDP ports and to apply MS17-010, the Microsoft security bulletin that patched EXTERNALBLUE, the exploit the AES-NI author claims to use.
Furthermore, to be on the safe side, just make sure you apply all the Microsoft patches that can block exploits from last week’s Shadow Brokers dump.
You should install these patches ASAP. A report from threat intelligence firm SenseCy released yesterday reveals that the cyber-crime underground is abuzz with talk on the various ways to use these exploits in mundane malware distribution. Furthermore, security researchers Dan Tentler an Rob Graham said they’ve spotted in-the-wild attacks with some of the leaked NSA exploits.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











