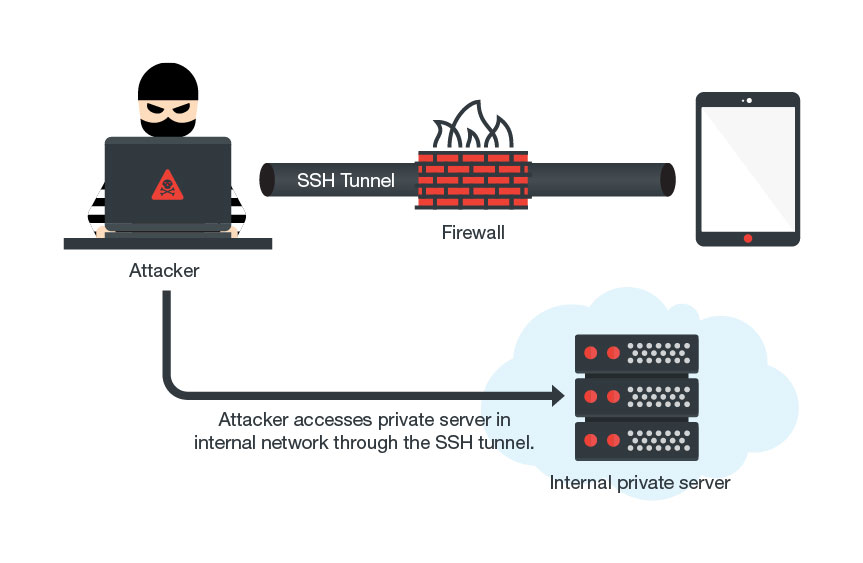
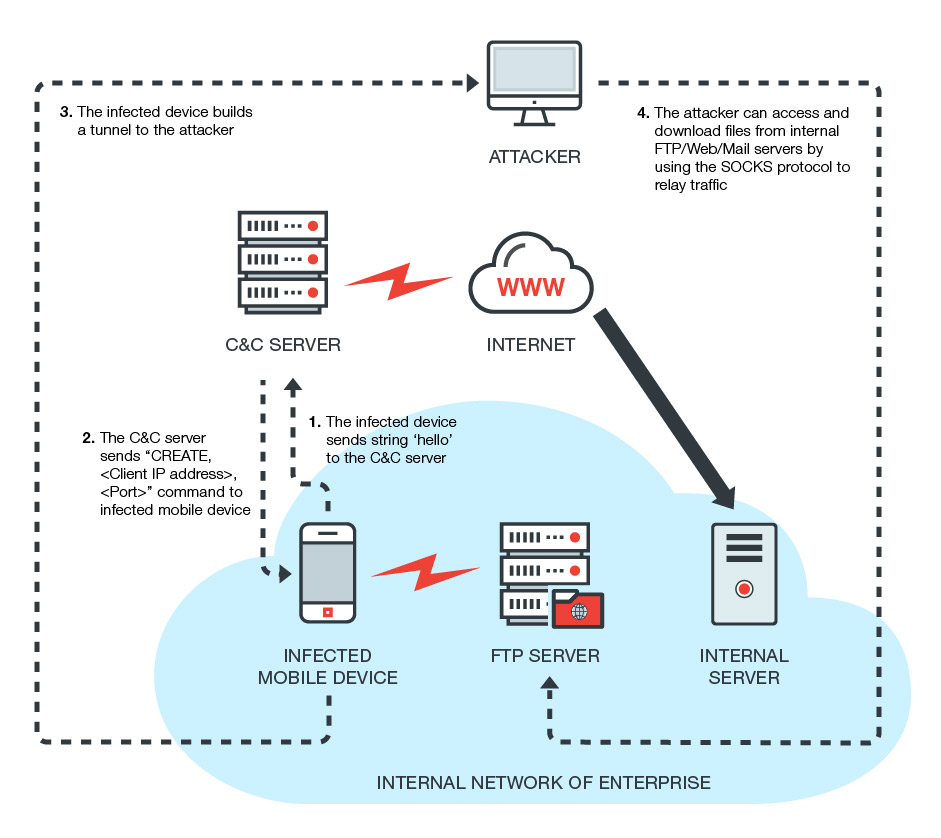
A new form of Android malware, named Milkydoor, uses remote port forwarding via Secure Shell (SSH) tunnels to hide malicious traffic and grant attackers access to firewall-protected networks.
The malware was recently found in over 200 Android applications available through the Play Store. Security researchers from Trend Micro, the ones who discovered MilkyDoor, say they reported the apps to Google, which promptly removed them from their official app store.
In total, researchers estimate the apps had between 500,000 and 1 million installs only through the Play Store alone.
MilkyDoor works just like DressCode
Following an analysis of MilkyDoor’s capabilities, Trend Micro says the malware appears to be a variation of an older Android threat known as DressCode.
Just like MilkyDoor, DressCode also has the ability to evade Google’s Play Store security scans, reaching the store on two different occasions, in August and September 2016.
Under the hood, both malware families are similar, according to researchers, with one main difference. While MilkyDoor creates an SSH tunnel to allow attackers access to internal company networks, DressCode relies on SOCKS proxy servers.
 |
 |
Smartphones used as relay points for other attacks
Despite this difference, both malware variants appear to have been developed to be used in the same manner. Crooks use the infected devices while the user is at his workplace to escalate access to internal company servers, launch attacks, and steal data.
With MilkyDoor, all this happens behind the safety of an encrypted SSH tunnel, where network monitoring solutions can’t reach. Furthermore, most firewalls whitelist SSH connections altogether, allowing crooks unfettered access to almost all targets.
Because of these actions, the only way of stopping MilkyDoor attacks is by detecting the malware on user devices before or during installation. For this, it is advised that users employ some sort of mobile security solution for their smartphones.
You can find a list of app names and package names for all the Android apps Trend Micro discovered infected with MilkyDoor. Most of these are repackaged versions of various games and children books.
Source:https://www.bleepingcomputer.com/news/security/milkydoor-android-malware-uses-ssh-tunnels-to-access-secure-corporate-networks/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











