I am trying something new where I will post in brief articles about new ransomware as they are released. Many of these ransomware infections do not warrant a full article, but I feel its important to quickly get the word out about new techniques or variants as we discover them.
In our first ransomware in brief article, we are taking a look at a new in-development ransomware called BitKangoroo that I discovered today. Yes, I know, skidz can’t spell. This particular ransomware is developed by a real scumbag who intends to delete a victims files if they do not pay fast enough.
In summary, this ransomware will encrypt a victim’s files using AES-256 encryption and append the .bitkangoroo extension to encrypted files. It will then display a 60 minute countdown that when reached will cause the ransomware to delete one encrypted file. Once it deletes a file, it will reset the timer back to 60 minutes. Most importantly, this ransomware can be decrypted for free using Michael Gillespie’s BitKangarooDecrypter.
You can see the lock screen for BitKangoroo below.
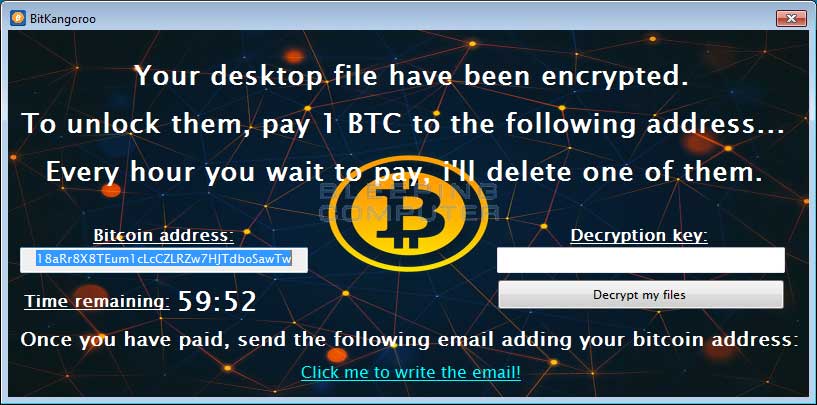
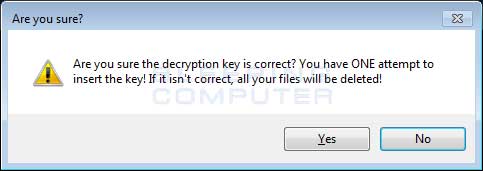
As this ransomware is currently in-development, the ransomware only encrypts files on the Desktop. It also contains non-working code that will cause ALL of the encrypted files to be deleted if the victim enters the wrong decryption key. You can see the warning message below that is displayed when you click on the Decrypt my files button.
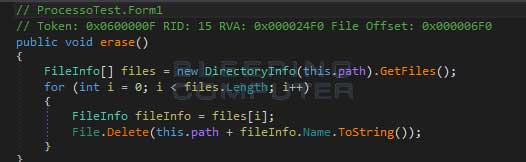
Here is the code that deletes all of the encrypted files:
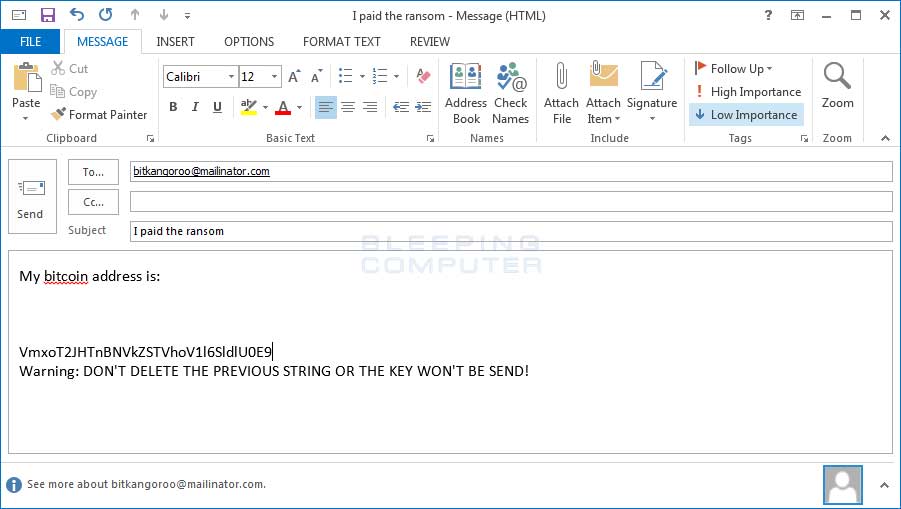
Finally, the ransomware screen contains a label that when clicked on opens a form to email the ransomware developer. The current email being used is bitkangoroo@mailinator.com and you can see an example of the email below.
If the status of this ransomware changes, I will update the article.
If you find these brief writeups useful, please let me know so I can decide if I should continue doing them.
IOCS:
Hashes:
SHA256: 810f9bff502d2c9a98164201590eed5ff2cc96cd42a5d6008af93ecfc8bf9c13Associated Files:
%UserProfile%\AppData\Roaming\IEAgent.exe
Associated Emails:
bitkangoroo@mailinator.comSource:https://www.bleepingcomputer.com/news/security/news-brief-bitkangoroo-ransomware-deletes-your-files-if-you-do-not-pay/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











