For almost four months, script kiddies ran amok in one of Stanford’s subdomains, installing web shells, mailers, and other types of web malware.
The infection was noticed last week by security researchers at Netcraft and was reported to Stanford admins, who recently cleaned their site.
The affected website belongs to the Paul F. Glenn Center for the Biology of Aging at Stanford University.
According to timestamps of the files surreptitiously uploaded to the hacked site, attackers appear to have compromised the site on January 31, 2017.
Multiple hackers broke in, used the site for phishing, spam
The hacker who initially breached the site uploaded a simplistic web shell. Once the website was compromised, other hackers seem to have flocked to the same server, like flies to a carcass.
The others that came afterward uploaded more complex web shells, and then started varying their portfolio.
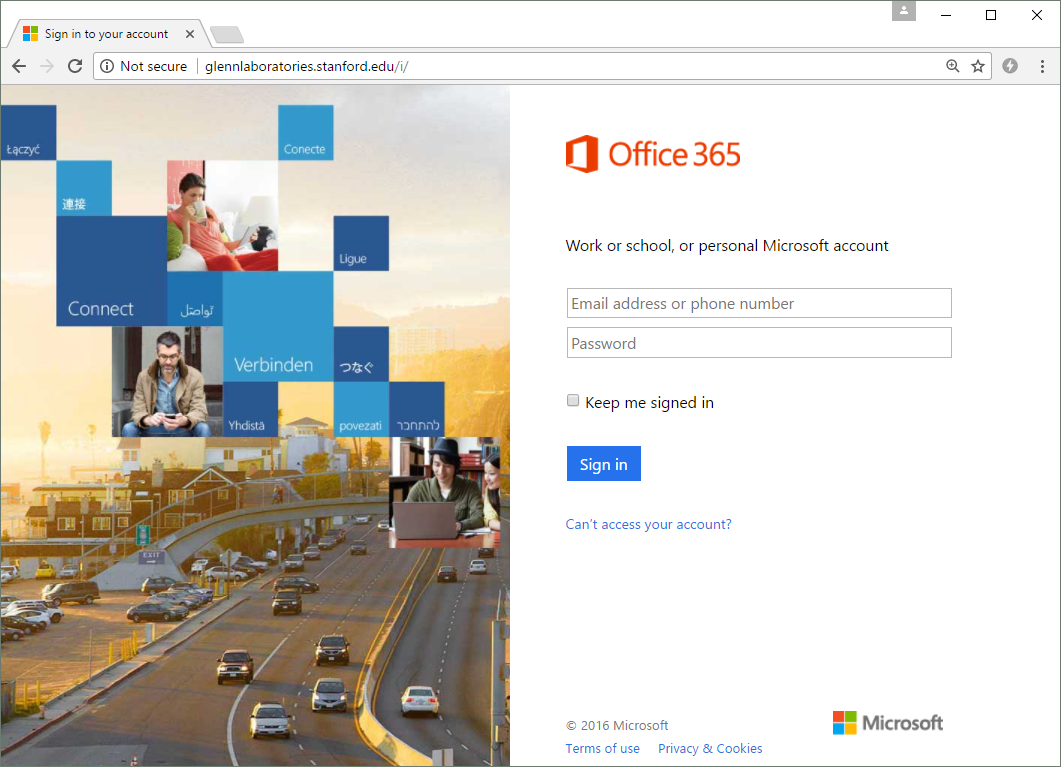
When Netcraft researchers found the compromised Stanford site, they say it was hosting numerous pages used for phishing Office 365, Gmail, and LinkedIn credentials. They also found a full-blown phishing kit, and a page that phishing e-banking credentials for the SunTrust Bank.
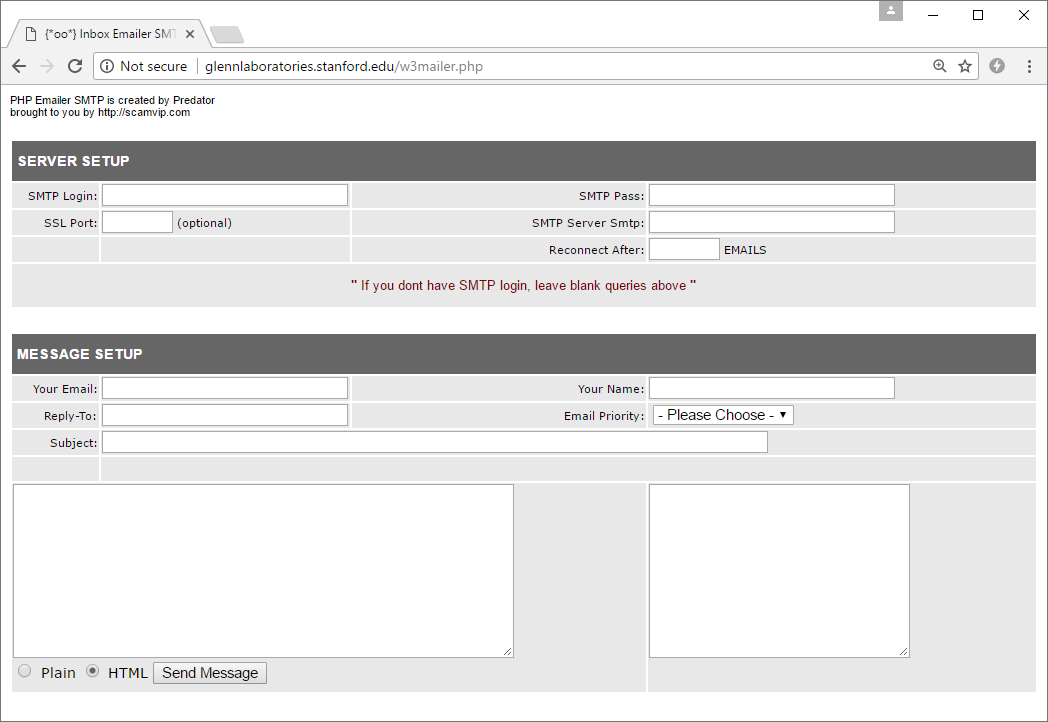
Besides this, they also found numerous mailer scripts, which means the server was used for sending large quantities of spam.
In addition, they also found lots of defacement pages. One of the defacement pages belonged to a hacker named Alarg53, a serial website defacer, who at the time of writing has plastered his name over 15,800 sites.
Despite their best efforts, Netcraft researchers couldn’t identify the original point of entry. Researchers noted that the compromised site was running the latest version of WordPress, version 4.7.5, which means hackers didn’t use a flaw in the website’s CMS. Most likely, the hackers used a vulnerability in the site’s theme or one of its plugins.
Source:https://www.bleepingcomputer.com/news/security/stanford-university-site-hosted-malware-for-months/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











