I was told by Emsisoft security researcher xXToffeeXx about a new ransomware called TeslaWare that is being promoted on a black hat criminal site. After a quick search, I was able to find a sample that was compiled yesterday and I began to dig into to it.
What did I find? That the marketing poster promoting TeslaWare was much more advanced than the ransomware itself.
TeslaWare being Marketed on Black Hat Sites
TeslaWare is currently being promoted and sold through black hat/criminal sites for 35 to 70 Euros depending on the customizations the buyer want in the ransomware. Posted in a black hat forum, the developer is marketing TeslaWare using a very nicely designed poster that combines the Tesla car logo, a network operations center, and specifications for the ransomware. Overall, the marketing poster is well done and provides most of the info a potential buyer would need.
 |
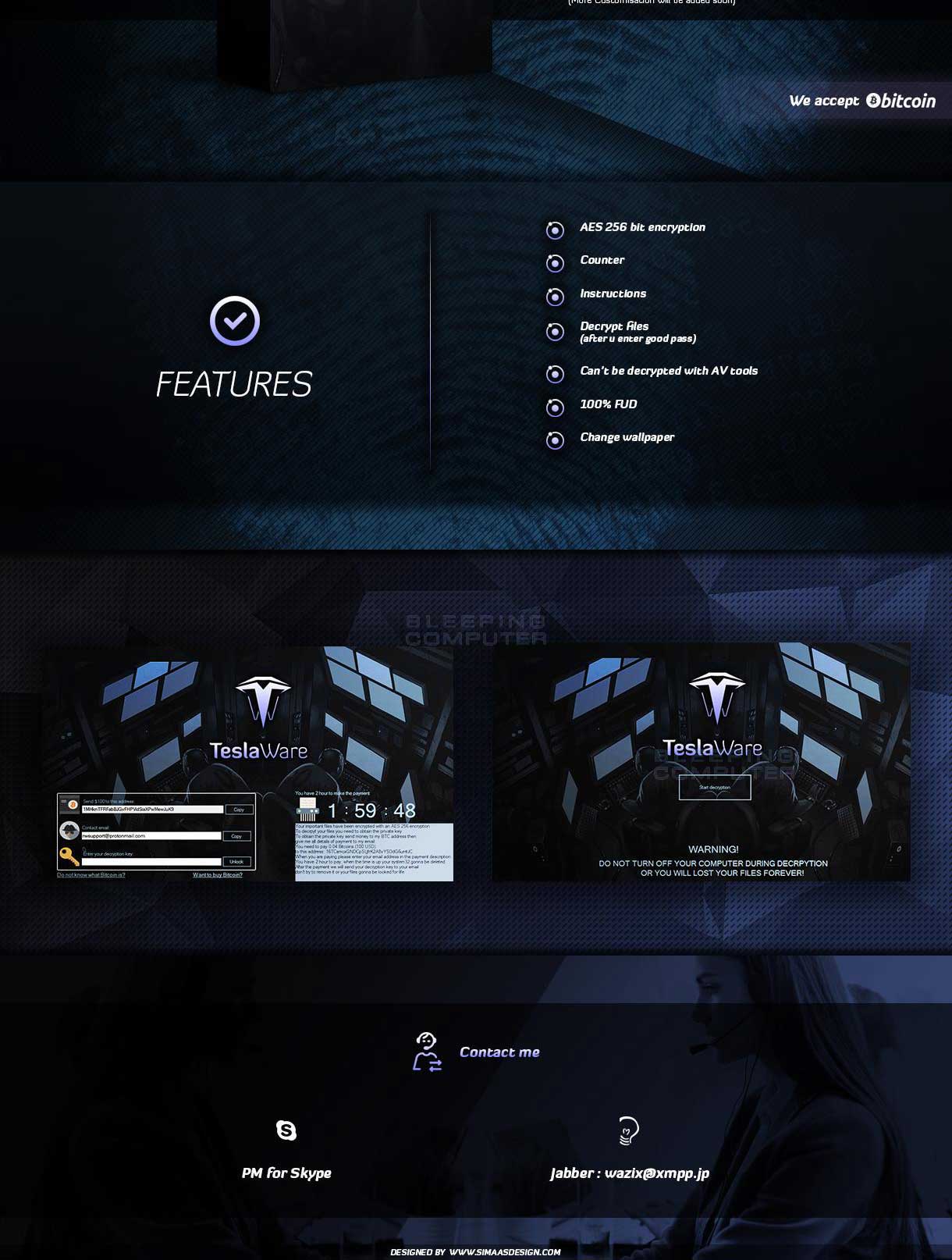 |
According to the poster, TeslaWare can be purchased at the following price points based on the features a buyer wants to customize:
- 35€ Custom BTC
- 40€ Custom BTC & Text
- 50€ Custom BTC, Text, Timer, & Pass
- 70€ All above with custom GUI
The poster also lists the following TeslaWare features:
- AES 256 Bit Encryption
- Counter
- Instructions
- Decrypt Files
- Can’t be Decrypted With AV Tools
- 100% FUD
- Change Wallpaper
While, most of the listed features are accurate, the ransomware is definitely not FUD and can be decrypted for free.
TeslaWare Easily Defeated
The good news about TeslaWare is that there are numerous flaws in the program that allow victims to get their files back for free. Therefore, if you become infected with TeslaWare, do not pay the ransom and instead contact us for information on how to decrypt your files.
As a personal policy, I do not discuss the flaws in a ransomware unless they are already publicly released. This is because ransomware developers commonly frequent BleepingComputer and I do not want to give them any tips on how to secure their ransomware.
For those who become infected with TeslaWare and need help decrypting their files, please post in our dedicated TeslaWare Help & Support Topic.
TeslaWare Plays Russian Roulette with Your Files
As TeslaWare is a .NET ransomware we can get a complete view as to how the ransomware works. I can tell you straight up that this ransomware is a complete mess, ineffecient, and horribly slow. These flaws, though, are to our benefit as it allows us to more time to detect the infection while it is running. Unfortunately, though, this ransomware threatens to delete your files if you do not pay the ransom and it carries through with that promise.
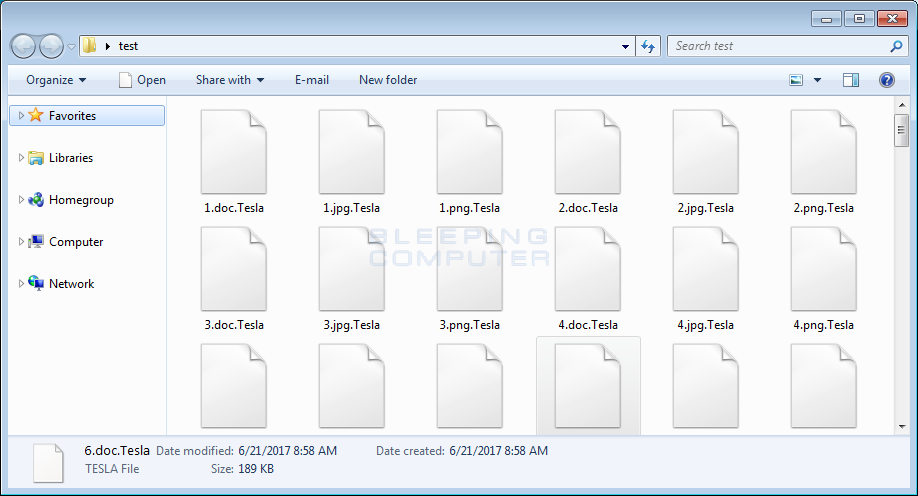
When started, TeslaWare will encrypt files using AES-256 encryption and target numerous drive letters and folders. Unlike most ransomware that target specific file extensions, TeslaWare will instead encrypt everything but those files that end with .Tesla, .lnk, .exe, .dll, and .sys.
When encrypting a file, TeslaCrypt will append the .Tesla extension to the encrypted files. This means that a unencrypted file called test.jpg would be encrypted and renamed as test.jpg.Tesla.
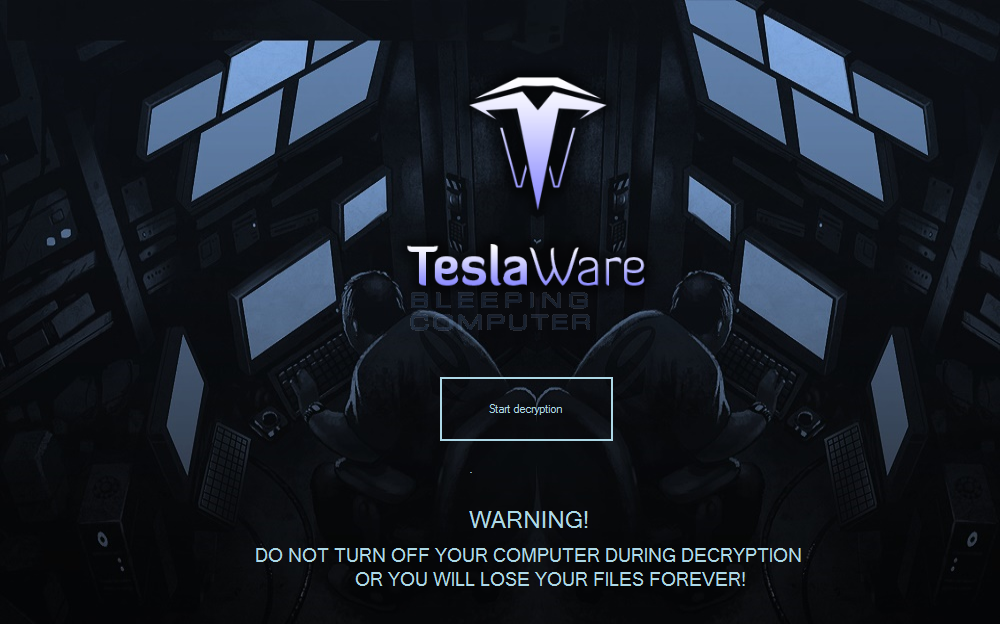
When it is done encrypting files, the TeslaWare ransom screen will be displayed as shown below.
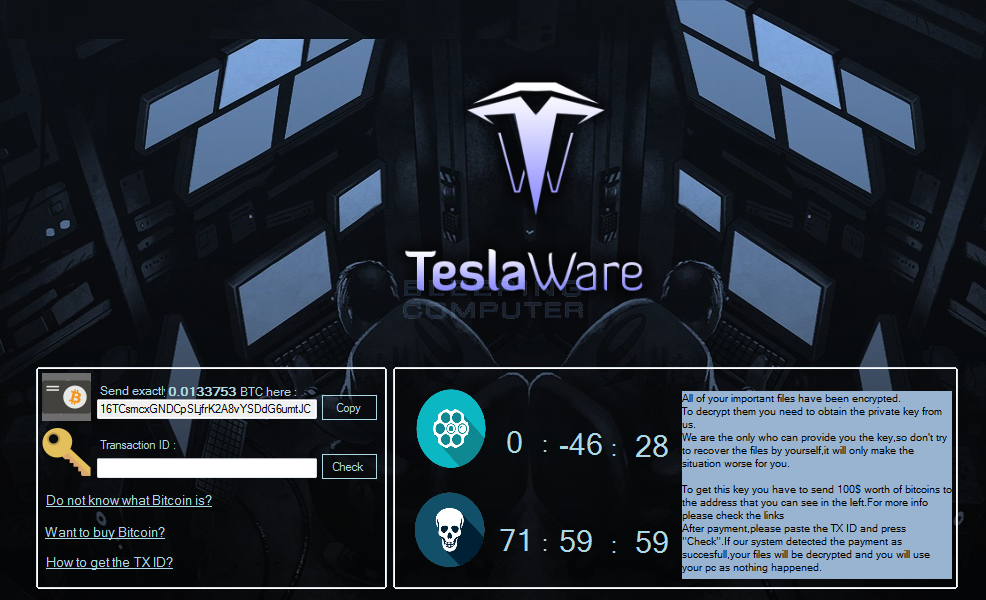
This lock screen will contain two timers. The first timer, which depicts revolver cylinder, is a 59 minute countdown for the Russian Roulette “feature” of TeslaWare. When this countdown hits 0, TeslaWare will delete 10 random files from the victim’s desktop or subfolders.
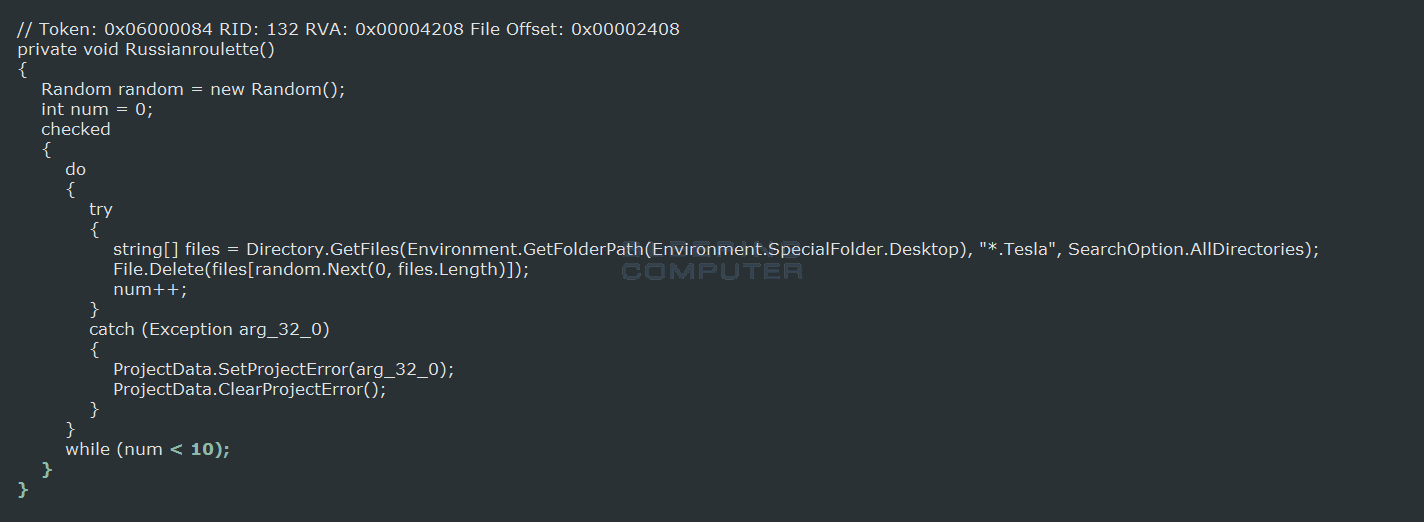
The second timer, showing the the skull, is for 72 hours and when it reaches 0, TeslaWare will delete all of the files on the C: drive.
Finally, TeslaWare will attempt to download and set the victim’s desktop wallpaper to a picture of Nikola Tesla as seen below.

TeslaWare has Unused Code to Create Shares and act like a Worm
Included in TeslaWare are two unused functions that could increase the damage potential of the ransomware. The first function allows the developer to create a new network share on the victim’s computer. While, this does not have any readily apparent usefulness, it could be used to gain further access to a victim’s computer if they are connected directly to the Internet without a firewall protecting them.
The other function is to have TeslaWare spread to open network shares on other computer. This function, called NSpread, will copy the executable to network shares and then create .pif files called runme.pif or start.pif in these shares. If a user on the remote computer executes these files, then TeslaWare would be installed on those computers as well.
As previously stated, these functions are currently not in use at this time.
IOCs
Hashes:
SHA256: b1475898b803b336d1ca6fb26677e5c8fd6c1e5251c0d8b766a7da6a14380259Files associated with TeslaWare:
%LocalAppData%\Tempimage.jpg
WindowsDrivers.exe
Registry Keys associated with TeslaWare:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WindowsDrivers WindowsDrivers.exeNetwork Traffic:
https://deos.esy.es
https://btc.blockr.io
https://free-stuff-here.netne.net/RW
Ransom Note Text:
All of your important files have been encrypted.
To decrypt them you need to obtain the private key from us.
We are the only who can provide you the key,so don't try to recover the files by yourself,it will only make the situation worse for you.
To get this key you have to send 100$ worth of bitcoins to the address that you can see in the left.For more info please check the links
After payment,please paste the TX ID and press "Check".If our system detected the payment as succesfull,your files will be decrypted and you will use your pc as nothing happened.Source:https://www.bleepingcomputer.com/news/security/teslaware-plays-russian-roulette-with-your-files/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











