Webmasters can use so-called ZIP bombs to crash a hacker’s vulnerability and port scanner and prevent him from gaining access to their website.
The term “ZIP bomb” refers to nested ZIP archives that when unzipped are decompressed to huge files that the victim’s computer cannot process in its memory or cannot store on disk.
For example, a 4.5 petabyte file containing only zeroes can be easily compressed to 42 kilobytes because the ZIP compression system can handle repetitive data extremely well.
ZIP bombs used in the past to crash antiviruses
ZIP bombs have been used in the past decades as a way to crash antivirus software, which is configured to scan ZIP files by decompressing the file and looking at its content.
While antivirus clients have gained protection against ZIP bombs, other software has not, such as web browsers or vulnerability scanners like Nikto, SQLMap, or others.
Austrian tech expert Christian Haschek has put together two PHP scripts that will scan for particular user-agent strings and deliver ZIP bombs to vulnerability scanners or web browsers trying to access secure or private web pages (such as admin panels, backends, or pages with login forms).
These scripts will replace the normal page hackers would expect to find with a ZIP bomb. Once their clients receive the ZIP bomb, they’ll try to process the data and crash the attacker’s software.
Most browsers and scanners will crash
Here’s a table put together by Haschek that details how some clients will behave when encountering a ZIP bomb.
| Client | Result |
|---|---|
| IE 11 | Memory rises, IE crashes |
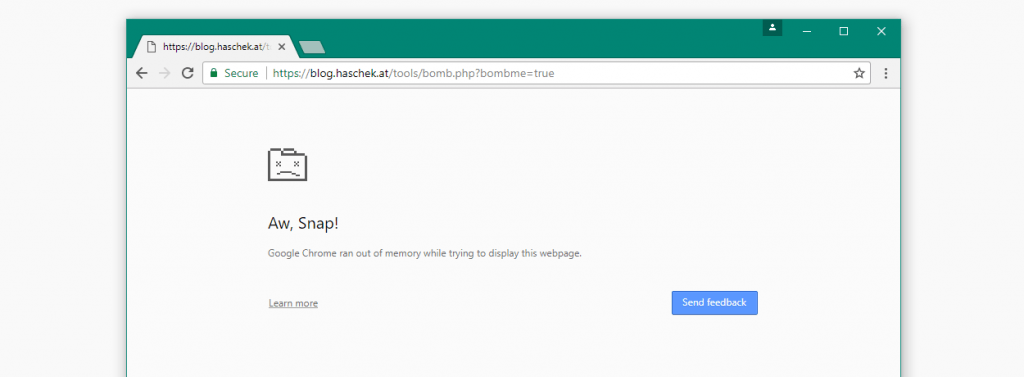
| Chrome | Memory rises, error shown |
| Edge | Memory rises, then dripps and loads forever |
| Nikto | Seems to scan fine but no output is reported |
| SQLmap | High memory usage until crash |
| Safari | Hight memory usage, then crashes and reloads, then memory rises again, etc.. |
| Chrome (Android) | Memory rises, error shown |
The two sample PHP files needed to set up a ZIP bomb for vulnerability scanners are available on Haschek’s blog. A demo that users can access in their browser is available here, but beware that it might crash your client and you may lose your current browsing session.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.