Sensitive data for around 14 million Verizon customers was exposed online because a third-party contractor forgot to limit external access to an Amazon S3 server.
UpGuard, a cyber-security company that discovered the leak, says the server belongs to NICE Systems, an Israeli tech company involved in supplying mass surveillance capabilities to oppressive regimes [1, 2], but also software for back-office and call center operations.
Exposed server contained Verizon call center logs
The server and its data were accessible by typing a URL in the browser. The URL used the “verizon-sftp” subdomain.
The server root contained various files, along with folders in a log-like format. Folders were titled from “Jan-2017” through “June-2017,” and each folder contained folders for each day of the month.
In each of these daily folders, there were ZIP files containing text files. Each text file held information on Verizon customers. For some days, the ZIP files decompressed to as much as 23GB of data.
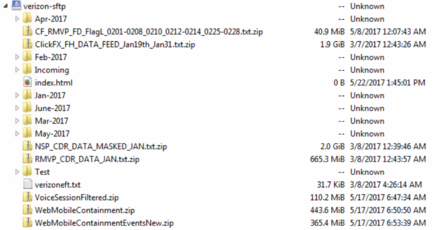
These text files held details such as Verizon customer names, addresses, account details, and for some account PINs.
Exposure of Verizon PIN numbers is a problem
If the data from this leak was ever exposed to the public, hackers could use these PINs to pass as legitimate account owners. The dangers of exposing someone’s Verizon PIN account are well known.
In the past, hackers have social engineered mobile telco call centers to attach a new SIM for a user’s phone number, which they used to sign into 2FA-protected accounts and steal money from bank accounts, cryptocurrency wallets, or PayPal.
Besides text files holding data on Verizon customers, the same server also housed recordings of calls to Verizon customer support lines. UpGuard believes this data came from the voiceportalfh.verizon.com service.
Data from French mobile operator Orange also exposed
Furthermore, the same NICE Systems server also contained data from French mobile telco Orange S.A., but unlike the Verizon data, the Orange folder contained what appeared to be internal files, not as sensitive as the data stored in the Verizon directory.
Experts say they contacted Verizon and NICE on June 13, when they discovered the server, but the leak was fixed nine days later on June 22.
“Third-party vendor risk is business risk; sharing access to sensitive business data does not offload this risk, but merely extends it to the contracted partner,” says UpGuard spokesperson Dan O’Sullivan.
“This breach once […] demonstrates the fact that cloud services like AWS can be secure, but it is up to organizations using them to ensure that services are configured in a secure fashion,” said Bitglass CEO Rich Campagna, who wanted to point out this incident was caused by human error and not the underlying technology.
Source:https://www.bleepingcomputer.com/news/security/data-of-14-million-verizon-customers-exposed-in-server-snafu/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











