Dutch Police are aggressively going after Dark Web vendors using data they collected from the recently seized Hansa Market.
Currently, the infosec community and former Hansa vendors themselves have spotted two ways in which Dutch authorities are going after former Hansa vendors.
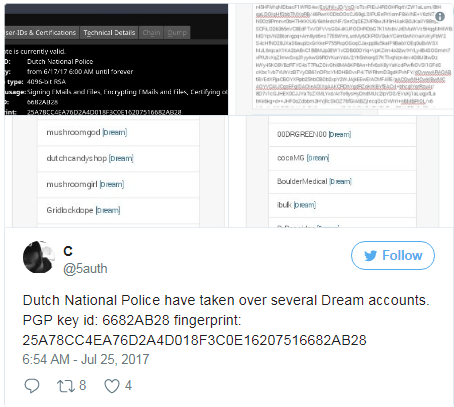
Police gain access to Dream accounts via password reuse
In the first, Dutch investigators have taken the passwords of vendors who have the same usernames on both the old Hansa Market and the Dream Market — today’s top Dark Web marketplace after the seizure of the Hansa and AlphaBay marketplaces.
If vendors reused passwords and they didn’t activate 2FA for their Dream Market accounts, authorities take over the profiles, change passwords, and lock the vendors out of their shops.
Dream Market and the Dark Web community have tracked down 14 vendor accounts who have changed their PGP keys with one belonging to Dutch Police.
One of the above listed vendors confirmed on Reddit that he lost access to his Dream Market account because he reused passwords on Hansa and Dream.
Another crook’s name also appears on a list of vendors Dutch authorities have been keeping an eye since last year, according to a Dark Web portal managed by Dutch Police.
Police spreading Excel files laced with phone-home beacons
The second method of operation spotted by the Dark Web community involves so-called “locktime” files that were downloaded from the Hansa Market before Dutch authorities shut it down on July 20.
Under normal circumstances a locktime file is a simple log of a vendor’s market transaction, containing details about the sold product, the buyer, the time of the sale, the price, and Hansa’s signature. The files are used as authentication by vendors to request the release of Bitcoin funds after a sale’s conclusion, or if the market was down due to technical reasons.
According to people familiar with Hansa’s inner workings who shared their knowledge with Bleeping Computer, Hansa locktime files were usually just a simple text file.
Before the market went down, these locktime files were replaced with Excel files that contained a hidden image. When the vendor opened the file to view transaction details, the image would load on the vendor’s computer.
This image was hosted on the Hansa Market, and once loaded, the server would log the user’s IP address. If the user didn’t use a VPN, proxy, or funneled all OS-level traffic through Tor, the Hansa server would log his real IP address.
Even if the Hansa Market went down, some vendors might still have the files laying around their computers. After Hansa went down, vendors most certainly opened the files looking into ways to retrieve any funds still locked in Hansa’s accounts.
It was all part of the plan
Dutch Police has seized the Hansa Market servers on June 20, and have secretly collecting data from vendors up until July 20, when they officially announced their operation, shutting down the market for good.
When Europol announced the seizure of Hansa Market servers, an Europol provided the following soundbite, which now makes more sense than ever.
In the past few weeks, the Dutch Police collected valuable information on high value targets and delivery addresses for a large number of orders. Some 10 000 foreign addresses of Hansa market buyers were passed on to Europol.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.