EXCLUSIVE — The author of the BrickerBot malware has claimed a cyber-attack that took place in various Indian states and has caused over 60,000 modems and routers to lose Internet connectivity.
The incident affected modems and routers belonging to Bharat Sanchar Nigam Limited (BSNL) and Mahanagar Telephone Nigam Limited (MTNL), two Indian state-owned telecommunications service providers.
From Tuesday, July 25 and up to Saturday, July 29, users reported losing Internet connectivity as routers and modems became stuck with their red LED remaining always on.
Internet downtime blamed on “malware attack”
BSNL told local press that malware caused the downtime. Besides customers routers, the malware also affected routers part of BSNL’s National Internet Backbone (NIB), but these were immediately recovered.
An employee of BSNL’s technical team told Deccan Chronicle that the incident caused modems in northeast, north and south Indian states to lose connectivity. According to The Hindu, the downtime was prolonged until Saturday because BSNL employees were also on strike.
BSNL estimated that 60,000 modems lost connectivity, affecting 45% of all their broadband connections. MTNL did not provide any numbers.
Customers asked to change default credentials
On Friday, BSNL said the malware attacked modems where users hadn’t changed the default password (admin/admin), and later asked over 2,000 users to change their device’s default credentials.
On Sunday, BSNL principal general manager K. Ramachand said the malware affected 90% of all newly installed modems but declined to give out a precise number. He also confirmed the malware had attacked only modems that still used their default password.
BSNL technical support has been busy all last week helping users reset modem and router passwords, either via telephone, with the help of on-premise staff, or by redirecting customers to online tutorials. BSNL also asked customers to visit field offices and have modems reset by employees if they needed to have an immediate functional Internet connection.
The Hindu reports that BSNL engineers “were perturbed by the fact that the modems that were reset developed problem again once they were put into action on customers’ premises.” More on this below.
BrickerBot author claims downtime
Over the weekend, the author of the BrickerBot malware approached Bleeping Computer and claimed he was behind the downtime. BrickerBot is a malware strain that affects Linux-based IoT and networking devices. Unlike other malware that hoards devices into botnets for DDoS attacks and other purposes, BrickerBot “bricks” the equipment by rewriting its flash storage. In most cases this bricking effect can be reversed, but in some cases this is permanent.
In a previous interview with Bleeping Computer, the BrickerBot dev said he created and proliferated the malware only to raise awareness among ISPs that they are running unsecured devices. He also wanted to brick IoT devices so they wouldn’t become part of IoT DDoS botnets, hoping that in the future, owners and ISPs will take greater care to safeguard devices against bricking and indirectly secure devices against Mirai, Hajime, Imeij, Amnesia, and other DDoS malware.
“BSNL’s devices are generally insecure and BSNL isn’t being honest about the situation by blaming its customers for negligence,” the BrickerBot author wrote in an email.
“They have hundreds of thousands of modems with unprotected TR069 (TR064) interfaces which allow anybody to reconfigure the devices for MITM attacks or DNS hijacking. There isn’t much that an affected customer can do to prevent such attacks since the BSNL network and its devices are insecure by design,” he also added, revealing why forcing customers to change default passwords didn’t help.
The BrickerBot author also provided technical details about other hard-coded logins in BSNL devices that the BrickerBot malware used — outside of the default admin/admin credentials — to connect to vulnerable equipment.
ISPs exposed port 7547 to external Internet connections
The BrickerBot author — who also likes to go by the name The Doctor — also pinned the cause of the cyber-attack on BSNL and MTNL allowing external connections into their network via port 7547.
This port is used by TR069, a management protocol that ISPs use to send commands and manage routers at customer’s homes.
BSNL and MTNL allowed anyone from the Internet to connect via port 7547 to routers and modems on their internal network. The TR069 is vulnerable to various security flaws that allow an attacker to execute code on the device.
The open TR069 ports and the hard-coded logins in some devices allowed BrickerBot to wreak havoc among the two Indian ISPs during the past week.
Attacks stopped after ISPs filtered port 7547
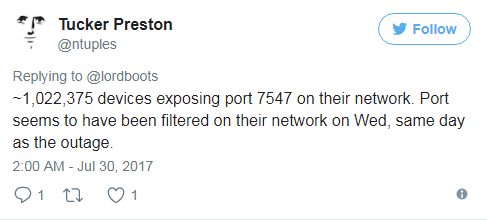
Attacks quieted down towards the weekend, as the two providers filtered access to port 7547. A security researcher that goes on Twitter by the nickname of @ntuples saw this sharp decline in exposed devices following the mid-week cyber-incident.
“This ‘attack’ on India telco modems has nothing to do with politics or nationality,” the BrickerBot dev told Bleeping Computer, fearing Indian authorities might blame it on neighboring Pakistan. “It’s simply a side-effect of an ongoing cleanup operation against vulnerable netblocks around the world.”
“ISPs: Please filter your customer device control ports. Your customers deserve to be secure and I deserve a break from having to clean up your IoT garbage!,” he also added.
The BrickerBot author also raised the alarm about similar exposed devices on the network of Pakistan Telecommunication Company Limited (PTCL).
“Their [REDACTED] routers are even more dangerous than BSNL’s,” the BrickerBot dev said.
BrickerBot author to continue his IoT security crusade
Nonetheless, there is also good news. “Mass-scanning behavior by IoT botnets has been in constant decline and it’s becoming less feasible to detect insecure netblocks purely through passive listening,” the malware dev said.
“The continued high availability of insecure TR069 interfaces on ISP devices is also a concern. I carried out an initial large-scale attempt to mitigate TR069 interfaces around the end of April and have recently resumed the effort with a few new experimental payloads. My goal for now is to keep the ‘dirtiest’ 1-2% of routed IP space under pressure in the hopes that ISPs such as BSNL will hear the message and improve their edge/core router filtering.”
In the end, BSNL and MTNL customers were lucky because their devices could be recovered without suffering permanent damage. In previous months, BrickerBot has been linked to infections where the device could not be recovered, and the “bricking” action was permanent.
BSNL did not want to comment for our story. An MTNL spokesperson authorized to comment could not be reached.
Source:https://www.bleepingcomputer.com/news/security/brickerbot-dev-claims-cyber-attack-that-affected-over-60-000-indian-modems/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.