Security researchers from Akamai, Cloudflare, Flashpoint, Google, Oracle Dyn, RiskIQ, Team Cymru, and a few other companies have worked together to take down a DDoS botnet made up of Android devices.
The botnet — which researchers named WireX — appeared at the start of the month and was built using malware-infected apps distributed via third-party app stores and even the official Google Play Store.
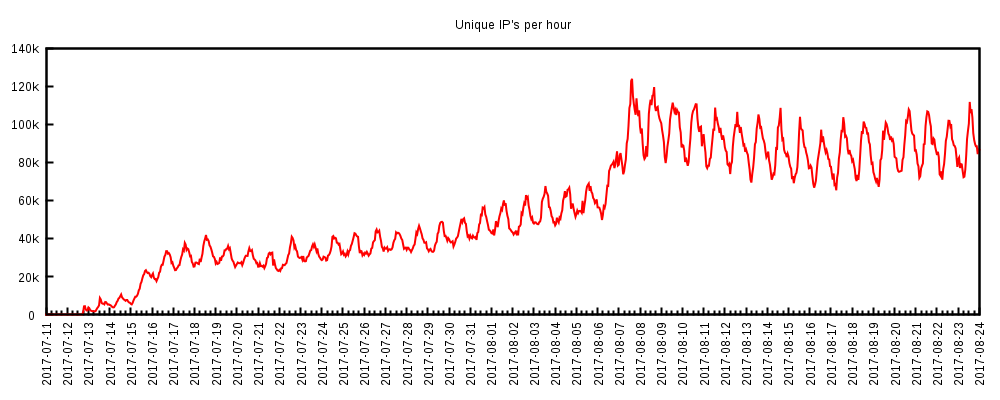
Botnet discovered after noisy DDoS attacks
Evidence suggests that crooks began assembling their botnet in mid-July, but WireX came to the attention of security researchers on August 17, after its authors decided to use it to launch DDoS attacks.
Researchers say the attacks were quite powerful and managed to bring down various services. Some attacks came to the attention of law enforcement as attackers also sent ransom demands to the targeted organizations.
Data collected by various companies and aggregated for the purpose of identifying the source of these attacks reveals that in mid-August, the botnet was capable of launching DDoS attacks using bots spread across over 120,000 unique IP addresses.
It was because of this unique collaboration between competing companies that investigators managed to bring down the botnet so shortly after its creation.
WireX used to launch Layer 7 DDoS attacks
According to identical technical reports published online by the participants of this investigation [1, 2, 3, 4], WireX was capable of launching powerful Layer 7 (application-level) DDoS attacks that while they didn’t jam server bandwidth, they did exhaust server memory resources, causing online services to go down.
Experts say WireX was capable of launching a wave of HTTP GET and POST requests at targeted servers using user-agent strings resembling traffic coming from web browsers.
These user agent strings were in the form of random lowercase English alphabet characters.
User-Agent: jigpuzbcomkenhvladtwysqfxr
User-Agent: yudjmikcvzoqwsbflghtxpanre
User-Agent: fdmjczoeyarnuqkbgtlivsxhwp
User-Agent: yczfxlrenuqtwmavhojpigkdsb
User-Agent: dnlseufokcgvmajqzpbtrwyxih
User-Agent: mckvhaflwzbderiysoguxnqtpj
User-Agent: deogjvtynmcxzwfsbahirukqplWireX botnet created via malicious Android apps
Because security firms collaborated and pooled their data, they quickly identified all bots and discovered how victims got infected, tracking down over 300 Android apps containing the WireX malware.
Google intervened and removed the apps from the Play Store, and then used the tools at its disposal to remove the malicious apps from all infected devices.
Researchers say that current mobile antivirus solutions detect apps infected with the WireX malware as “Android Clicker.” This is because the malware also had the ability to perform click-fraud, which it used in the beginning, and then switched to launching DDoS attacks.
The trojan looks very similar to the GhostClicker malware previously analyzed by Trend Micro before its authors decided to use it to launch DDoS attacks.
Lessons learned from Mirai, WannaCry, NotPetya
Previous efforts to take down large-scale botnets, either used for DDoS attacks or financial fraud, have lingered for years and botnets survived multiple takedown attempts. This time, they decided to work together.
“The researchers involved have worked together for quite a while now often on smaller events or just passing anonymized information back and forth informally to try and protect the internet and our respective customers,” Tim April, Senior Security Architect at Akamai told Bleeping Computer in an email.
“This event started in a similar way but as discoveries were made and shared the pieces started to come together faster than with similar events,” he added. “We elected this time to publish together to highlight the collaboration and to make sure that the whole story got out as one rather than each of us publishing on our own timelines with a small pieces of the story.”
“This trust group was formed immediately following the initial massive attacks that originated from Mirai,” Justin Paine, Head Of Trust & Safety at Cloudflare, told Bleeping Computer. “This group of researchers was also instrumental during the initial triage of WannaCry, NotPetya, and other events since Mirai.”
“These group efforts are almost never reported about but they are a key reason for why some of the larger botnets have quietly gone away,” Allison Nixon, Director of Security Research at Flashpoint, also added. “It’s spontaneous and based on trust relationships that go back years. Without this phenomenon I don’t think the Internet would be as functional as it currently is.”
“When people talk about “cybersecurity information sharing”, it is exactly this type of phenomenon which they wish to enable,” Nixon also added.
Source:https://www.bleepingcomputer.com/news/security/security-firms-unite-to-bring-down-wirex-android-ddos-botnet/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











