Android bootloader components from five major chipset vendors are affected by vulnerabilities that break the CoT (Chain of Trust) during the boot-up sequence, opening devices to attacks.
The vulnerabilities came to light during research carried out by a team of nine computer scientists from the University of California, Santa Barbara.
Researchers developed BootStomp to analyze bootloaders
The research team looked into the shadowy world of Android bootloaders, components that are hard to analyze because they are closed-source and tend to lack typical metadata (such as program headers or debugging symbols) that are usually found in normal programs and help reverse engineering and security audits.
Most of the team’s work focused on developing a new tool named BootStomp specialized in helping test and analyze bootloaders.
Experts found six new flaws
By using BootStomp to find problematic areas of the previously obscure bootloader code, and then having the research team look over the findings, experts said they identified seven security flaws, six new and one previously known (CVE-2014-9798). Of the six new flaws, bootloader vendors already acknowledged and confirmed five.
“Some of these vulnerabilities would allow an attacker to execute arbitrary code as part of the bootloader (thus compromising the entire chain of trust), or to perform permanent denial-of-service attacks,” the research team said. “Our tool also identified two bootloader vulnerabilities that can be leveraged by an attacker with root privileges on the OS to unlock the device and break the CoT.”
For their work, researchers considered five different bootloaders from four different vendors.
– NVIDIA Tegra chipset [Nexus 9]
– MediaTek chipset [Sony Xperia XA]
– Qualcomm’s new LK bootloader
– Qualcomm’s old LK bootloader
Researchers knew that the old Qualcomm LK bootloader was affected by CVE-2014-9798, and when BootStomp re-identified the old security bug, the team knew their tool was working properly. They also found a vulnerability in the NVIDIA chipset, and five in HiSilicon bootloaders. The full results are below.
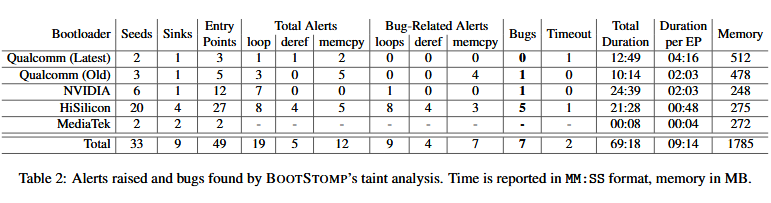
More details, along with proposed mitigations, are included in a research paper entitled “BootStomp: On the Security of Bootloaders in Mobile Devices.” Researchers presented their work earlier this month at the USENIX conference in Vancouver, Canada.
Source:https://www.bleepingcomputer.com/news/security/vulnerabilities-discovered-in-mobile-bootloaders-of-major-vendors/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.












