Loopix is a new anonymity network developed by a group of researchers from University College London (UCL) that comes with all the good parts of previous systems and new additions to improve security.
Both Loopix and Tor are based on the concept of mix networks and are meant to provide a way to send anonymous messages through a complex network.
The way Tor achieves this is through its circuit-based onion routing protocol. On the other hand, Loopix uses a classic message-based architecture combined with Poisson mixing — adding random time delays to each message.
The end result is an anonymity network that is very secure but also fixes the main disadvantage of classic message-based architectures, which is high-latency.
As the UCL team points out in their research paper, the Loopix system has a “message latency is on the order of seconds – which is relatively low for a mix-system.”
How Loopix works
The way Loopix works is very similar to Tor, both being based on the same principles of mix networks. A user connects to a provider (ingress provider), the same way Tor users connect to entry guards.
The Loopix provider server sends the user’s message through the network through random mix nodes, similar to how Tor sends messages through relays.
The message arrives at the intended user’s provider (egress provider), where it is stored inside a message box until the user comes online. This is where Loopix is different, allowing the storage of offline messages.
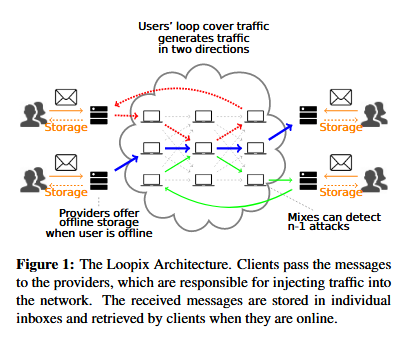
Similar to Tor, Loopix also uses encryption by encapsulating messages using Sphinx, a cryptographic message format.
In addition, it also uses cover traffic for both when data travels inside the network and when users send or receive messages from the providers.
Loopix looks good on paper, until now
Researchers say that Loopix’s trio of encryption, cover traffic, and randomly delayed messages can counter ISP and nation-state level passive surveillance.
Tests using a demo Loopix network showed that “mix nodes in Loopix can handle upwards of 300 messages per second, at a small delay overhead of less than 1.5 ms on top of the delays introduced into messages to provide security.”
Overall, researchers say the latency is low compared to similar message-based mix networks, making Loopix usable for real-time communications, just like Tor.
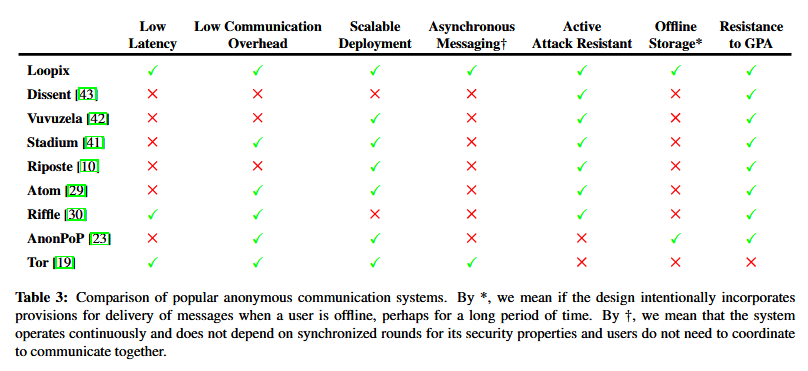
In fact, a comparison table put together by the research team shows that Loopix is not on par with Tor, but also much more suited for anonymous communications, even when compared to other systems such as HORNET, Dissent, Vuvuzela, Stadium, Riposte, Atom, Riffle, or AnonPoP.
Currently, the Loopix system is still in its infancy, and more research is needed. Nonetheless, researchers say Loopix is resistant to Sybil attacks, currently one of Tor’s biggest problems.
More technical details are available in a research paper published in March this year and named “The Loopix Anonymity System,” available online here.
Source:https://www.bleepingcomputer.com/news/technology/the-loopix-anonymity-system-wants-to-be-a-more-secure-alternative-to-tor/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











