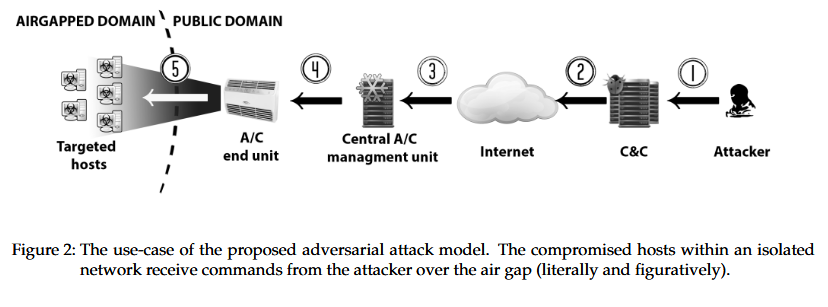
Heating, ventilation, and air conditioning (HVAC) systems can be used as a means to bridge air-gapped networks with the outside world, allowing remote attackers to send commands to malware placed inside a target’s isolated network.
This type of attack scenario — codenamed HVACKer by its creators — relies on custom-built malware that is capable of interacting with a computer’s thermal sensors to read temperature variations and convert these fluctuations into zeros and ones — binary code.
The malware, already installed on a computer on an isolated network with no Internet access, reads the temperature variations created by the HVAC system and converts the received thermal signals into malicious operations.
Researchers from the Cyber Security Research Center at the Ben-Gurion University of the Negev in Israel were the ones who came up with this attack scenario, and they created proof-of-concept malware that can be used to execute HVACKer attacks.
They also created a custom line-encoding protocol that allows a remote attacker to send commands using temperature fluctuations. This custom line-encoding protocol — the technique of breaking down binary data to voltage, thermal, or optical signals — was needed because classic line-encoding methods were too slow and inaccurate.
How a HVACKer attack works
In order to carry out a HVACKer intrusion, an attacker must first choose a target and identify an HVAC system left connected to the Internet or sitting on an Internet-connected internal network. Attackers don’t necessarily have to look for standalone HVAC systems, but they can also look for building automation software, which usually incorporates an HVAC component.
Once attackers identify such a system, they must find a way to breach and take control of it, either by using old bugs or by devising new exploits. They will need access to the HVAC system in order to have access to fiddle with its temperature setting operations.
The next stage in the attack relies on creating the custom HVACKer malware that can pick up thermal variations caused by the HVAC system based on the custom line-encoding protocol.
Attackers then need to infect computers inside a target’s isolated network. While this sounds hard, as these are highly secure networks, past attacks with malware such as Stuxnet, Gauss, and Flame, show that a mundane infected USB can sometimes do wonders.
Once the attacker knows his malware made it into the infected network, he can use his connection to the hacked HVAC to alter temperature settings in order to send the desired commands to the malware sitting on an infected computer inside the company’s secure network.
Malware ideal for sending commands, not for stealing data
Based on the HVAC system’s capabilities, the temperature variations can be broadcast over an entire building, or just in a room. If attackers infect multiple computers inside the same air-gapped network, researchers say the malware can also be altered to include a synchronization component that improves the reading of thermal fluctuations by aggregating data from multiple PCs.
HVACKer attacks are only useful for relaying commands into an air-gapped network, but not for stealing data. While malware can control a computer’s heat emissions, HVAC units are not equipped with enough accurate temperature sensors to pick up data from a computer’s almost indiscernible heat emissions.
Nonetheless, HVACKer-like malware is very useful. Previous attacks on air-gapped networks usually took weeks if not years to carry out, needing multiple interventions — sometimes with on-the-ground agents — for reconnaissance operations, data collection, sending new commands, and exfiltrating stolen information. HVACKer cuts down the time needed to update already existing malware, without the need for an attacker to be present on location.
For an HVACKer attack to be successful, temperature control operations used to relay malicious commands need to be carried out at night, when there are few if no human around to detect the unnatural heat variations.
HVACKer attacks are dangerous. Have been used in the past
Because HVAC systems are present in the buildings of all major enterprise, government, or military systems, HVACKer attacks present a clear danger to anyone running an air-gapped system.
According to tests carried out by the research team, they were able to send data inside an air-gapped network via HVAC systems at bit rates of 40 bits per second, a more than acceptable transmission speed.
Cyber-attacks involving HVAC systems have already taken place. For example, the source of the Target data breach was a provider of HVAC systems. Similarly, security researchers hacked Google Australia’s network using an HVAC system. In February 2016, Kaspersky researchers also theorized that a hacker could break into air conditioners across a city to turn them on and cause a power surge that cripple’s a town’s power grid.
The same team that came up with the HVACKer attack scenario has a long history of weird hacks and ingenious attacks on air-gapped systems.
SPEAKE(a)R – use headphones to record audio and spy on nearby users
9-1-1 DDoS – launch DDoS attacks that can cripple a US state’s 911 emergency systems
USBee – make a USB connector’s data bus give out electromagnetic emissions that can be used to exfiltrate data
AirHopper – use the local GPU card to emit electromagnetic signals to a nearby mobile phone, also used to steal data
Fansmitter – steal data from air-gapped PCs using sounds emanated by a computer’s GPU fan
DiskFiltration – use controlled read/write HDD operations to steal data via sound waves
BitWhisper – exfiltrate data from non-networked computers using heat emanations
Unnamed attack – uses flatbed scanners to relay commands to malware infested PCs or to exfiltrate data from compromised systems
xLED – use router or switch LEDs to exfiltrate data
Shattered Trust – using backdoored replacement parts to take over smartphones
aIR-Jumper – use security camera infrared capabilities to steal data from air-gapped networks
The technical details of the HVACKer attack are included in a research paper titled “HVACKer: Bridging the Air-Gap by Attacking the Air Conditioning System,” available for download here and here.
Source:https://www.bleepingcomputer.com/news/security/attackers-can-use-hvac-systems-to-control-malware-on-air-gapped-networks/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











