iTerm2, a popular Mac application that comes as a replacement for Apple’s official Terminal app, just received a security fix minutes ago for a severe security issue that leaked terminal content via DNS requests.
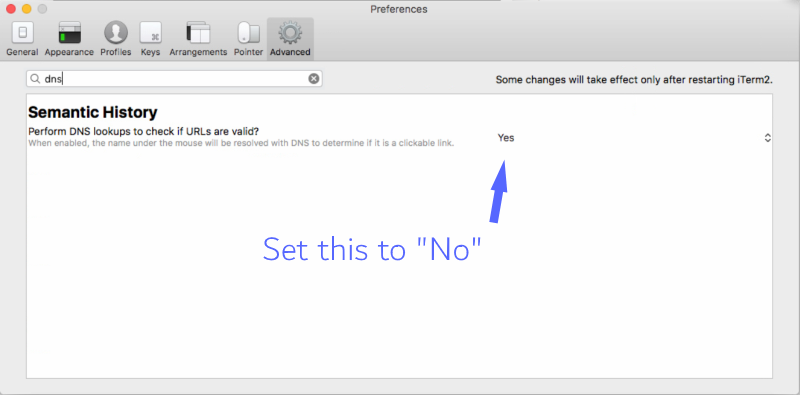
Version 3.1.1 disables a feature that was added in iTerm 3.0.0 and was turned on by default. This feature is found under iTerm2’s “Perform DNS lookups to check if URLs are valid?” setting.
Introduced in version 3.0.0, this feature would watch the user’s mouse when hovering any content inside iTerm2’s terminal. When the mouse would stop over a word, iTerm2 would attempt to determine if that word was a valid URL and highlight the term as a clickable link.
To avoid creating dead links by using inaccurate string pattern matching algorithms, the feature would make a DNS request instead, and determine if that domain actually existed.
iTerm accidentally sent passwords, API keys to DNS servers
This behavior is a huge privacy issue, as users hovering their mouse over passwords, API keys, usernames, or other sensitive content, would unknowingly leak this information via DNS requests.
DNS requests are cleartext communications, meaning anyone capable of intercepting these requests would have had access to data a user was hovering in his iTerm terminal.
According to the app’s official website, iTerm2 3.0.0 was released on July 4, 2016, indicating that scores of users leaked sensitive content to DNS servers without their knowledge for more than a year.
iTerm2 maintainer apologize
iTerm2’s leak issue was first discovered ten months ago. iTerm2’s creator initially reacted by adding an option to iTerm 3.0.13 that allowed users to disable DNS lookups. The feature remained turned on by default for new and existing installations.
Dutch developer Peter van Dijk, software engineer for PowerDNS, a supplier of open-source DNS software and DNS management service, re-reported this feature and this time around, he pointed out some of the severe privacy leaks not included in the first bug report.
“iTerm sent various things (including passwords) in plain text to my ISP’s DNS server,” van Dijk wrote flabbergasted in a bug report he filed earlier today.
This time around, George Nachman, iTerm2’s maintainer, understood the severity of the issue right away and released iTerm2 3.1.1 to fix the problem within hours. He also apologized for enabling this feature by default without analyzing possible consequences in more depth.
“I don’t have an excuse: I just didn’t give this issue enough thought. I apologize for the oversight and promise to be more careful in the future,” Nachman wrote. “Your privacy will always be my highest priority.”
Security investigations also affected
Besides possibly leaking sensitive content such as passwords and API keys, there’s also another negative side to this feature.
“Domains should not be queried through DNS to determine whether they are highlighted in iTerm,” said a user named ewaher, the user who first spotted this bug’s behavior.
“The current behavior can compromise a security analyst or incident responders investigation by querying a URL unintentionally while in iTerm,” he added. “Often hackers/attackers monitor their attacking infrastructure for such investigators and these types of queries coming from a target’s network.”
According to the iTerm2 changelog, version 3.1.1 “includes a security patch to disable undesirable DNS requests that could leak user data.”
Users using versions of iTerm between 3.0.0 and 3.0.12 are advised to update to at least version 3.0.13, where they can disable DNS lookups by going to Preferences ⋙ Advanced ⋙ Semantic Historyand flipping the “Perform DNS lookups to check if URLs are valid?” option to No.
Source:https://www.bleepingcomputer.com/news/security/iterm2-leaks-everything-you-hover-in-your-terminal-via-dns-requests/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











