Proof-of-concept malware created by a team of Israeli researchers uses the infrared capabilities of modern security cameras as a channel for data exfiltration, but also to receive new commands from its operators.
Named aIR-Jumper, the malware is meant to be installed on computers that interact with security surveillance cameras/software, or on a computer in the same network with the camera, so the attacker can have a way to hack his way into the device.
Camera’s infrared LEDs can be used for data theft, control
The malware works by taking data collected from an infected computer, breaking it down into binary ones and zeros, and leveraging the camera’s API make the device’s infrared LEDs blink, using this mechanism as a way to exfiltrate data from an infected network.
An attacker sitting in the range of the security camera’s infrared LED will be able to record the blinking and use special software that reconstructs the blinks and pauses into the ones and zeros of the stolen data.
Similarly, an attacker can use an infrared LED to send new commands to a security camera inside an infected network. The malware can watch the camera’s video feed, detect infrared LED transmissions at preset time intervals, and convert the incoming blinks into new commands it has to execute.
Surveillance and security cameras are equipped with infrared LEDs as a way to enable night vision. Because infrared light is imperceptible to the human eye, any communications to and from the compromised network are invisible to all bystanders.
aIR-Jumper created with air-gapped networks in mind
Malware like this was created for stealing data from air-gapped networks that are disconnected from the Internet for security purposes.
The aIR-Jumper malware provides a perfect medium that targets do not think as a potential data exfiltration channel.
In addition, the malware can also be deployed on Internet-connected networks but used as a covert exfiltration medium that bypasses any firewalls and antivirus solutions and leaves minimal traces in log files.
Because of today’s proliferation of CCTV and surveillance solutions, malware like aIR-Jumper could be used to steal data and control malware installed on a wide variety of networks, ranging from corporations to secure government institutions, and from police departments to advanced research labs.
Exfiltration speeds are low but aIR-Jumper is more reliable
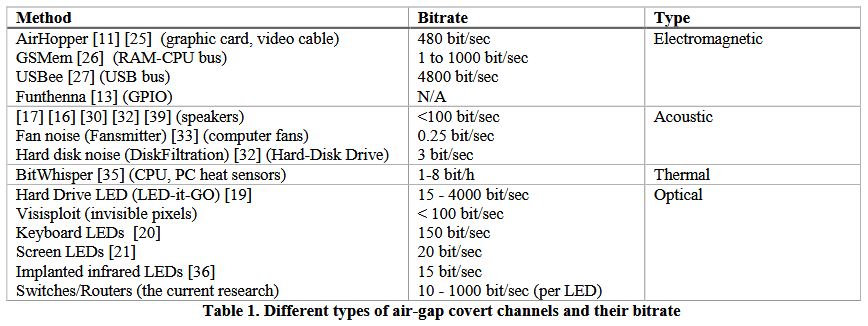
“Our evaluation shows that an attacker can use [infrared] and surveillance cameras to communicate over the air-gap to a distance of tens to hundreds of meters away,” researchers say.
“Data can be leaked from [a] network at a bit rate of 20 bit/sec (per camera) and be delivered to the network at bit rate of more than 100 bit/sec (per camera),” researchers added.
The exfiltration speed is low compared to similar experiments carried out by the same group of researchers. Previous findings show that router LEDs are the best data exfiltration medium from air-gapped networks.
Nonetheless, routers and switches are usually encased in data centers or special boxes across a company’s headquarters, while security cameras sit outside in the open, where attackers can easily interact with the devices.
In addition, researchers argue that infrared signals are better than router LEDs because infrared signals bounce of nearby surfaces with a higher reflection rate, and attackers don’t necessarily need a line of sight to the security camera itself.
Furthermore, researchers say that aIR-Jumper could be modified to work with other devices that use infrared LEDs, such as smart doorbells.
In their research paper titled “aIR-Jumper: Covert Air-Gap Exfiltration/Infiltration via Security Cameras & Infrared (IR),” researchers propose a series of mitigations, both software and hardware related, such as window shielding, firmware controls for disabling IR support, IR LED activity monitoring, iregular access to camera API functions, and others.
Researchers also published two videos showing how they send commands to the aIR-Jumper malware via the security camera, and how they exfiltrate data from the affected network.
The aIR-Jumper malware was created by a team of talented researchers from the Cyber Security Research Center at the Ben-Gurion University of the Negev in Israel. The same team is also behind various other kooky data exfiltration experiments that combine malware and the physical world.
SPEAKE(a)R – use headphones to record audio and spy on nearby users
9-1-1 DDoS – launch DDoS attacks that can cripple a US state’s 911 emergency systems
USBee – make a USB connector’s data bus give out electromagnetic emissions that can be used to exfiltrate data
AirHopper – use the local GPU card to emit electromagnetic signals to a nearby mobile phone, also used to steal data
Fansmitter – steal data from air-gapped PCs using sounds emanated by a computer’s GPU fan
DiskFiltration – use controlled read/write HDD operations to steal data via sound waves
BitWhisper – exfiltrate data from non-networked computers using heat emanations
Unnamed attack – uses flatbed scanners to relay commands to malware infested PCs or to exfiltrate data from compromised systems
xLED – use router or switch LEDs to exfiltrate data
Shattered Trust – using backdoored replacement parts to take over smartphones

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











