Attacks aimed at delivering cryptocurrency mining tools on enterprise networks have gone up as much as six times, according to telemetry data collected by IBM’s X-Force team between January and August 2017.
A recent report by fellow cyber-security firm Kaspersky found that cryptocurrency mining malware also infected over 1.65 million machines running Kaspersky solutions in the first eight months of the year.
While Kaspersky collected data mainly from desktop endpoints, IBM’s telemetry gathered data from servers and other enterprise systems.
Attackers hid cryptocurrency miners inside fake image files
According to IBM, most of the infections the company saw during the first eight months of the year involved the same mining tool and similar infection techniques.
IBM’s Dave McMillen told Bleeping Computer via email that attackers used “a wide range of exploits […] to first compromise […] CMS platforms (WordPress and Joomla and JBoss server) prior to launching the subsequent CMDi [command injection] attack,” that installed the cryptocurrency mining tool.
“These [mining] tools were hidden within fake image files, a technique known as steganography, hosted on compromised web servers running Joomla or WordPress, or stored on compromised JBoss Application Servers,” McMillen says.
The expert says attackers usually downloaded a customized version of a legitimate mining tool named Minerd, or a Linux port named kworker.
“In most cases, the attackers attempted to mine CryptoNote-based currencies such as Monero (XMR), which employs the CryptoNight mining algorithm,” McMillen said.
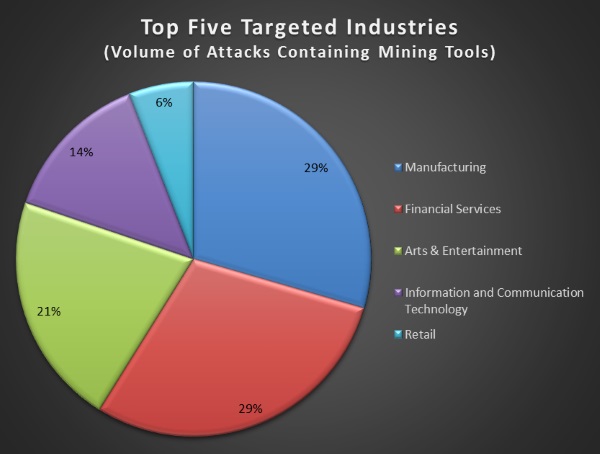
Attacks targeted companies in all industry verticals
“We are unable to determine the number of attacking groups or infected servers from our attack data,” McMillen added but said that attackers weren’t picky and infected any target they could get.
Infected servers spread across several industry verticals, such as manufacturing, finance, retail, IT & communications, and others.
No more Mirai versions with mining support
Back in April, the same IBM X-Force team discovered a version of the Mirai IoT malware that featured an experimental cryptocurrency mining feature.
As many experts predicted back then, today, McMillen confirmed that IBM had not seen any new Mirai malware strains deploying mining features.
“Exploiting IoT may be more of a proof of concept by attackers,” McMillen told Bleeping. The expert also added that he expects attackers to target both server and desktop endpoints in an equal manner, as both are very lucrative environments for mining operations.
The IBM and Kaspersky reports on the increase in cryptocurrency mining malware detections come after a string of incidents during the past few months that involved virtual currency miners.
⬗ Even some Mirai botnet variants tested a cryptocurrency mining function
⬗ Adylkuzz cryptocurrency miner deployed via EternalBlue NSA exploit
⬗ Bondnet botnet installed Monero miners on around 15,000 computers, mostly Windows Server instances
⬗ Linux.MulDrop.14 malware mines for cryptocurrency using Raspberry Pi devices exposed online
⬗ Crooks targeted Linux servers via SambaCry exploit to deploy EternalMiner malware.
⬗ Trojan.BtcMine.1259 miner uses NSA’s DobulePulsar to infect Windows computers
⬗ DevilRobber cryptocurrency miner became the second most popular Mac malware in July
⬗ Linux.BTCMine.26, a Monero miner that included references to Brian Krebs in its source code.
⬗ CoinMiner campaign that used EternalBlue and WMI to infect users
⬗ Zminer trojan found infecting Amazon S3 servers
⬗ CodeFork gang used fileless malware to push a Monero miner
⬗ Hiking Club malvertising campaign dropped Monero miners via Neptune Exploit Kit
⬗ A CS:GO cheat that delivered a Monero miner for MacOS users
⬗ Jimmy banking trojan adds support for a Monero miner
⬗ New Monero miner advertised via Telegram
⬗ Chrome extension that mines for Monero right inside the user’s browser
⬗ New Redatup malware variant that comes with a Monero mining feature
⬗ Malvertising campaign that mines cryptocurrency in your browser, via ads

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











