A team of three scientists from Columbia University has discovered that by attacking the combo of hardware and software management utilities embedded with modern chipsets, threat actors can take over systems via an attack surface found in almost all modern electronic devices.
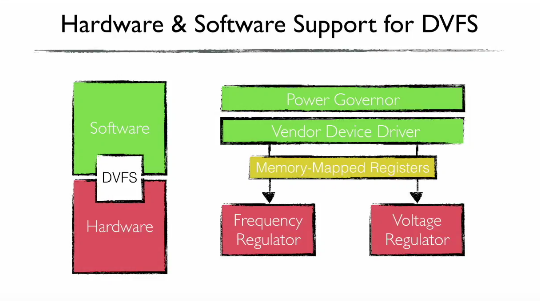
The issue at the heart of this attack is energy management solutions. CPU or SoC chipset vendors embed energy management systems with their products to allow device manufacturers a way to control energy consumption and improve battery life. In today’s day and age, energy management features are found in almost all chipsets.
CLKSCREW targets energy management systems like DVFS
The focus of the Columbia team’s research was an energy management system called Dynamic Voltage and Frequency Scaling (DVFS), which as its name suggests, allows a devicevendor to control the CPU’s voltage and frequency.
Introduced in 1994, DVFS is everywhere these days, as it’s also the system that vendors use to keep CPU temperature down and avoid the CPU from overheating and burning a hole through the chip itself.
Researchers say that despite becoming a pervasive system, DVFS and other energy management systems have not gone through thorough security audits.
CLKSCREW attack is a remote DFA
The CLKSCREW (read as “clock screw”) attack they devised is a classic Differential Fault Attack (DFA). These are attacks that stress hardware to its physical limits to record and compare results while at normal operation. A single byte modification in DFA-collected data is often enough to unravel security systems.
In past years, carrying out DFA attacks usually implied having physical access to devices in order to break down the device and use special rigs to modify the normal mode of operation to stress-like conditions.
Things have changed since then, and DVFS and other energy management solutions embedded with current chipsets are to blame.
The software part of energy management solutions allows for remote attacks when the device reads malicious content off the Internet. The code can interact with device drivers and alter the settings for voltage and frequency regulators, putting devices into a stress condition necessary for a DFA attack.
CLKSCREW attack foils ARM TrustZone component
In a research paper, the Columbia team explains how it used CLKSCREW to attack ARM TrustZone, a separate chip included with mobile CPUs on Android devices, and which handles secure and cryptographic operations on behalf of the main operating system.
Researchers used a CLKSCREW attack by serving code to the main CPU that caused the DVFS system to enter in a high-stress mode, overclocking the CPU.
Because the TrustZone chip and the main CPU use the same energy management solution, and there’s no DVFS for TrustZone, and another DVFS for the main CPU, the TrustZone chipset also entered a high-stress mode of operation.
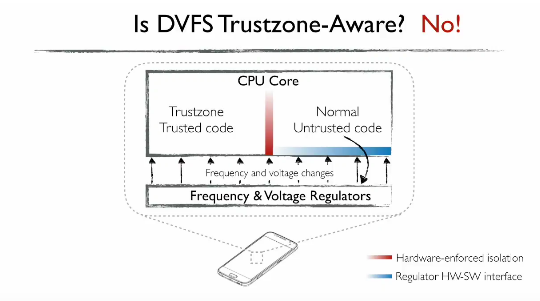
The design flaw allowed the research team to record how TrustZone would work in a normal state and a high-stress state. Their research was fruitful and they managed to induce and detect single byte errors that they later used to extract the TrustZone secret encryption key, the main key used to encrypt and protect all data computations taking place in the TrustZone chipset.
With this key in hand, they were able to load self-signed code into the TrustZone component of a Nexus 6 smartphone, used for their tests.
How CLKSCREW actually works
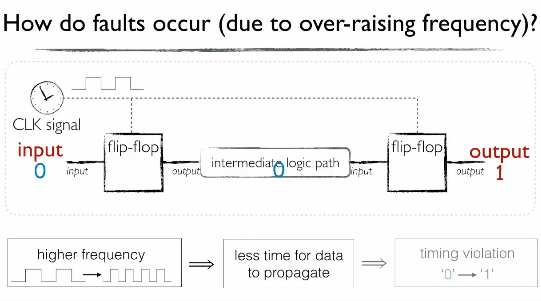
The reason why the attack worked is in its name — clock screw. CPUs are nothing more than a large collection transistors that hold a state of “1” or “0.” When the CPU processes data, they compute binary code – aka zeros and ones. As data is being processed, these transistors, called flip-flops, keep their state or change it from one to zero, or vice versa.
In order to synchronize data processing, these changes occur based on a CPU internal “base” clock, which also gives the CPU’s frequency, hence the reason why a higher CPU frequency means you can process more data.
By putting the CPU in a high-stress state, such as overclocking it by adjusting the DVFS frequency regulator, attackers reduce the time flip-flops have to change their state. Basically, the attack “screws” with the CPU’s clock, causing single byte errors as one or more flip-flops are still processing data from the previous CPU cycle.
Intel SGX and other systems possibly affected
While the experimental part of their research focused on the ARM TrustZone component, the Columbia University team believes the attack can be easily ported against Intel’s Secure Enclave SGX.
In addition, researchers also noted a trend from chipset vendors that are now providing more fine-grained energy management controls to users, but without considering the security of these tools.
“The industry is definitely trending towards finer-grained and increasingly heterogenous designs. So as a result, we’re gonna see designs which give software more control over the energy management,” said Andrew Tang, one of the researchers, during his USENIX presentation.
“We’ve obviously seen this on 64-bit ARMv8 architecture and the newer Intel processors, or even on cloud computing providers that are increasingly giving VM guests more control over the power management,” he also added.
CLKSCREW attack will be hard to mitigate
The research team says it contacted chipset vendors about their findings, and the vendors “were really responsive and really really receptive” and are currently “working towards mitigations.”
Nonetheless, mitigating CLKSCREW attacks seems like a “generation” vulnerability, a type of security flaw that is never fully mitigated until a new generation of chipsets hits the market.
“It’s the deepest, widest impact, hardest to fix security issue I’ve seen in a long time,” said Adrian Colyer, Venture Partner with Accel Partners, and former CTO at SpringSource.
“CLKSCREW isn’t just the latest in a known exploit genre, CLKSCREW opens the door to a whole new class of energy-management based attacks,” Colyer said.
The full research paper on CLKSCREW attacks is entitled “CLKSCREW: Exposing the Perils of Security-Oblivious Energy Management,” and can be downloaded from here, here, or here.
The paper was presented at the USENIX security conference held in Vancouver, Canada, where it won the Distinguished Paper Award. USENIX organizers published a video of the CLKSCREW presentation on YouTube, also embedded below.
Source:https://www.bleepingcomputer.com/news/security/clkscrew-attack-can-hack-modern-chipsets-via-their-power-management-features/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











