Electronic messages traveling across the internet are under constant threat from data thieves, but new security standards created with the technical guidance of the National Institute of Standards and Technology (NIST) will reduce the risk of messages being intercepted or stolen. These standards address a security weakness that has been a part of the internet since its earliest days(link is external).
The set of standards, known as Secure Inter-Domain Routing(link is external) (SIDR), have been published by the Internet Engineering Task Force (IETF(link is external)) and represent the first comprehensive effort to defend the internet’s routing system from attack. The effort has been led by a collaboration between NIST and the Department of Homeland Security (DHS) Science and Technology Directorate, working closely with the internet industry. The new specifications provide the first standardized approach for global defense against sophisticated attacks on the internet’s routing system.
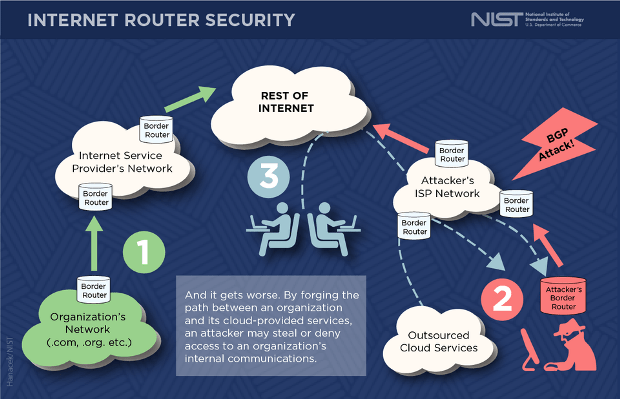
The overall strategy creates a defense mechanism for the Border Gateway Protocol (BGP(link is external)), the system that routers—the devices that direct information toward its destination—use to determine the path data takes as it travels across the collection of networks that comprise the internet. BGP forms the technical glue holding the internet together, but historically, its lack of security mechanisms makes it an easy target for hacking.
“BGP is a global scale system, where routing data for hundreds of thousands of destinations is exchanged between tens of thousands of networks. The informal trust mechanisms we’ve relied on in the past can’t be scaled up to protect a system of that size,” said Doug Montgomery, a NIST computer scientist and manager of the NIST project. “BGP as currently deployed has no built-in security mechanisms, so it is common to see examples of ‘route hijacks’ and ‘path detours’ by malicious parties meant to capture, eavesdrop upon or deny legitimate internet data exchanges.”
BGP was created in the late 1980s to allow routers to exchange information and calculate the best path among millions of possibilities for data to travel across the internet. BGP enables the modern commercial internet, but it evolved at a time when security was not a significant concern, and internet operators have been coping with security problems as a result.
Known BGP attacks since 2008 have resulted in stolen financial payments and network disruption, but so far, these have been relatively small-scale. In many ways, Montgomery said, we are simply lucky that there haven’t been more focused and malicious attacks that take advantage of BGP’s vulnerabilities.
“The fact that they haven’t been dramatically exploited yet shouldn’t make you feel better,” he said. “Think of how much of our critical infrastructure relies on internet technology—transportation, communication, financial systems, et cetera. Someday, someone will have the motivation.”
The overall defensive effort will use cryptographic methods to ensure routing data travels along an authorized path between networks. There are three essential components of the IETF SIDR effort: The first, Resource Public Key Infrastructure (RPKI), provides a way for a holder of a block of internet addresses—typically a company or cloud service provider—to stipulate which networks can announce a direct connection to their address block; the second, BGP Origin Validation, allows routers to use RPKI information to filter out unauthorized BGP route announcements, eliminating the ability of malicious parties to easily hijack routes to specific destinations.
The third component, BGP Path Validation (also known as “BGPsec”), is what is described in the suite of draft standards (RFCs 8205(link is external) through 8210) the IETF has just published. Its innovation is to use digital signatures by each router to ensure that the entire path across the internet crosses only authorized networks. Employing this idea of “path validation” together with origin validation could deter stealthy attacks intended to reroute data without the recipient realizing it. For example, a set of 2017 BGP incidents(link is external) detoured internet traffic from several financial institutions through networks in eastern Europe.
NIST’s technical expertise was crucial to the development of the standards, a process that has taken several years. Montgomery and his colleagues contributed modeling and analysis of how the standards would perform, and they also developed test and measurement tools the internet industry needs to have confidence in deploying the standards commercially. Throughout the effort, NIST collaborated closely with a DHS-sponsored research team and key members of the internet industry in the design, testing and evaluation of these new standards.
The new specifications for BGP Path Validation, along with the other components of the complete solution are available at the IETF Secure Inter-Domain Routing(link is external) Working Group’s website.
With their publication, Montgomery said, NIST’s efforts will shift to helping the industry with adoption, including developing technical deployment guidance as well as working on improving the performance and scalability of implementations. As part of this technology transition effort, NIST’s National Cybersecurity Center of Excellence (NCCoE) recently announced plans for a new projectfocused on Secure Inter-Domain Routing.
Source:https://www.nist.gov/news-events/news/2017/10/new-network-security-standards-will-protect-internets-routing

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.