Another wiper malware posing as a ransomware is targeting German businesses under the guise of fake job applicants inquiring about openings.
Ordinypt was discovered by ID-Ransomware coder Michael Gillespie when one of the malware’s ransom notes was uploaded to his firm’s site. Another sample was spotted targeting German users by G Data security researcher Karsten Hahn, according to Bleeping Computer.
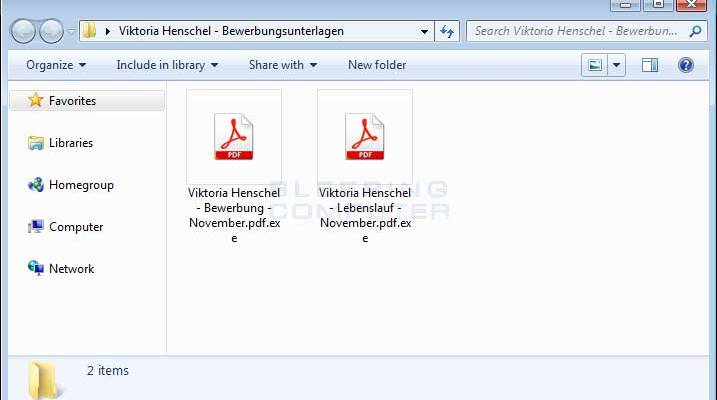
The malware is hidden in attachments named Viktoria Henschel – Bewerbungsfoto.jpg and Viktoria Henschel – Bewerbungsunterlagen.zip and which are supposedly a JPG image of the woman sending a resume, and a ZIP file containing the resume and a curriculum vitae.
The ZIP archive contains two EXE files that use the double-extension and custom icon tricks to fool users into thinking they’re instead two different files PDF files when they are in fact the same. Once installed, Ordinypt will replace the contents of files with random generated characters consisting of uppercase and lowercase letters and numbers Reverse Engineer Philipp Mackensen tweeted adding that the malware doesn’t encrypt PNG files.
Researchers have documented the method of infection for the last six months with previous versions of the campaign dating back to May with some earlier versions using Cerber as the ransomware payload, Lastline Director of Threat Intelligence Andy Norton told SC Media.
“This latest attack using the name Viktoria Henshel does not use Cerber, and has a very poor implementation of a payment method, suggesting that the threat actor does not want to get paid a ransom but merely wishes to destroy data of the targeted organisations,” Norton said. “We may speculate that this change in motivation may indicate a copycat threat actor; Someone who is copying the tools, tactics and procedures of one established threat group, but has a very different motive.”
The malware’s payment method uses a JavaScript function to select a random Bitcoin address from a list of 101 hardcoded wallet addresses and offers no way to contact the malware’s authors to verify a payment was received leading researchers to believe the sole purpose of the malware is to cause destruction.
Source:https://www.scmagazine.com/ordinypt-wiper-ransomware-poses-as-job-applicants/article/706774/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.