This article, it’s an insight into the ransomware business and how it operates, with data gathered over a period of two years. Moreover, since ransomware largely transacts using Bitcoin, the methods used by the information security research team to uncover and trace ransomware activity are also of interest in their own right.
In this paper, we create a measurement framework that we use to perform a large-scale two-year, end-to-end measurement of ransomware payments, victims, and operators. In total we are able to track over $16 million in likely ransom payments made by 19,750 potential victims during a two-year period.

In a brief explain, ransomware is a type of malware that encrypts a victim’s files and then demands a ransom in order to decrypt them. Bitcoin is the payment medium of choice for ransomware: it’s decentralized, largely unregulated, and parties in transactions are hidden behind pseudo-anonymous identities. It’s also widely available for victims to purchase, and transactions are irreversible.
However, Bitcoin has a property that is undesirable to cybercriminals: all transactions are public by design. This enables information security researchers, through transaction clustering and tracing, to glean the financial inner workings of entire cybercriminal operations.
Ransomware basics
First malware is delivered to a victim’s machine using any of the available methods. When it executes, the ransomware silently encrypts files on the victim’s machine, and then displays a ransom note informing the user that their files have been encrypted and the contents will be lost forever unless they pay a ransom.
The ransom note either includes a ransom address to which payment much be made, or a link to a payment website displaying this address. For the convenience of the victim, the note also often includes information on how to purchase the required Bitcoins from exchanges.
When payment is confirmed, the ransomware either automatically decrypts the files, or instructs the user on how to download and execute a decryption binary. The operator doesn’t need to decrypt the user’s files at all of course, but in general I guess it’s bad for business if word gets out on the Internet that even if you pay the ransom you still won’t regain access to your files.
Finding ransomware addresses
To discern transactions attributable to ransom campaigns, we design a methodology to trace known-victim payments, cluster them with previously unknown victims, estimate potentially missing payments, and filter transactions to discard the ones that are likely not attributable to ransom payments.
Real victim ransom addresses can be found by scraping reports of ransomware infection from public forums, and from proprietary sources such as ID Ransomware which maintain a record of ransomware victims and associated addresses. The number of deposit addresses that can be recovered this way is still fairly minimal though.
In total, the authors gathered 25 seed random addresses from actual victims, across eight ransomware families: CoinVault, CryptXXX, CryptoDefense, CryptoLocker, CryptoWall, Dharma, Spora, and WannaCry. Using the sandbox environments, a further 32 ransom addresses are obtained for Cerber, and 28 for Locky.
Following the money
Starting with the seed addresses above, we can look for addresses that co-spent with them, and hence are highly likely to also be under the control of the ransomware operator. This is a refinement of the techniques described in ‘A fistful of Bitcoins’:
…this method is now prone to incorrectly linking flows that use anonymization techniques, such as CoinJoin and CoinSwap. Moser and Bohme developed methods of detecting likely anonymized transactions. The information security experts use Chainalysis’s platform, which uses all these methods and additional proprietary techniques to detect and remove anonymized transactions, to trace flows of Bitcoins.
The technique only works if the ransomware operator actually spends the Bitcoins. For the ransom addresses obtained via self-infection, that’s not going to happen unless the ransom is paid! Instead of paying the full ransom, the authors make micropayments of 0.001 Bitcoins to these addresses.
All 28 micropayments made to Locky addresses were later co-spent by the operator in conjunction with other wallet addresses, “presumably in an attempt to aggregate ransom payments.” These lead to the discovery of a cluster of 7,093 addresses.
All 32 micropayments made to Cerber addresses were moved into a unique aggregation address. This address is then used to move the funds on, co-spending with other addresses. This ultimately leads to the discovery of a cluster of 8,526 addresses.

As a cross-check to see if there are potentially missed clusters, the information security analysts compare the timing of bitcoin inflow to the ransom addresses, Google Trends for ransomware family search terms, and the number of ransomware binaries on VirusTotal.

How much money are ransomware operators collecting?
Payments are checked to see if it’s likely they come from real victims. Two filters are applied. The first filter checks to see if the payment amounts match known ransom amounts. The second filter checks that the movement of bitcoin in the transaction graph matches the expected pattern for the ransomware in question.
Based on this analysis, it’s possible to estimate each ransomware family’s revenue.

In total the researchers are able to trace $16,322,006 US Dollars in 19,750 likely victim ransom payments for 5 ransomware families over 22 months. For Cerber and Locky, which generate unique addresses for each victim, it’s possible to estimate the number of paying victims over time.
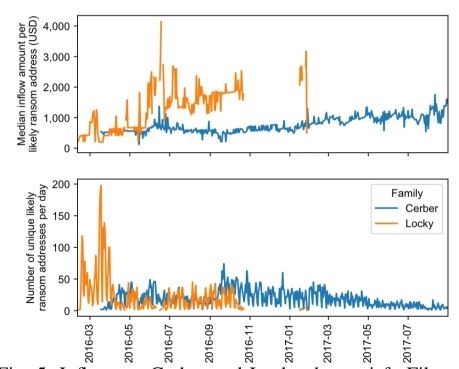
Looking at the outflows from ransomware addresses, we can trace movement to bitcoin exchanges. The Chainalysis API is used to obtain real-world identities of destination clusters. The top entities are BTC-e, CoinOne, and LocalBitcoins, along with BitMixer and Bitcoin Fog.

…BTC-e is the biggest known exchange responsible for the outflows of Locky and CryptoDefense; $3,223,015 of Locky’s outflows entered BTC-e’s cluster.
The paper also includes the result of reverse engineering the Cerber protocol and monitoring its UDP packets in the wild.
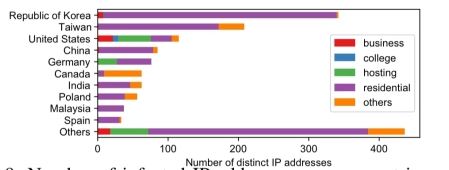
Prevention, detection, and intervention
Sometimes possible to trace ransomware payments to the point where ransomware operators cash out. It is also possible to disrupt the process by which victims pay the ransom, thus depriving operators of their profits.
This introduces a unique ethical issue. We must consider the impact on victims before taking down ransomware infrastructure. Whereas disrupting conventional malware reduces the damage to victims, the effect could be the opposite for ransomware, information security professionals said. If every victim did not pay or was prevented from paying, the scale of the problem would likely decrease; however this would mean that some individuals would incur additional harm by not being able to recover their files.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











