If you have a Low privilege Shell on any machine and you found that a machine has an NFS share you might be able to use that to escalate privileges. Depending on how it is configured.
First, the information security experts explain that the Network File System (NFS) is a client/server application that lets a computer user view and optionally store and update files on a remote computer as though they were on the user’s own computer. The NFS protocol is one of several distributed file system standards for network-attached storage (NAS).

What is root_sqaush and no_root_sqaush?
Root Squashing(root_sqaush) parameter prevents having root access to remote root users connected to NFS volume. Remote root users are assigned a user “nfsnobody” when connected, which has the least local privileges. Alternatively “no_root_squash“ option turns off the “squashing of root user” and gives the remote user root access to the connected system. System administrators should always use “root_squash” parameter when configuring NFS drives to make sure remote root users are always “squashed”, information security researchers said. For exploiting this issue NFS must be configured with no_root_sqaush.
Required tools and program files. This list is very short u just need a showmount, mount with nfs support.
- showmount
- mount
- C Program FIle or ( optional )

Exploit NFS and Get Root Shell, now, that I had limited shell so take a look at “/etc/exports” file. /etc/exports file contains configurations and permissions of which folders/file systems are exported to remote users.
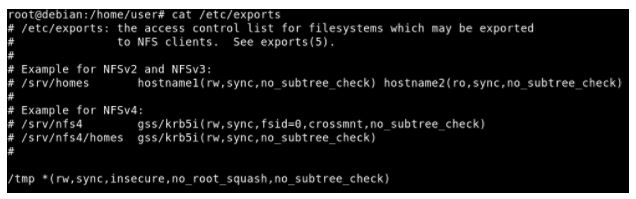
So, /tmp folder is shareable and remote user can mount it. let’s take a look on NFS configuration flags we have “rw” (Read, Write), “sync” and “no_root_squash” parameter which is not secure and we already talked about what is Root Squashing, information security researchers said.




Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











