So far, researchers have uncovered how web trackers exfiltrate identifying information from web pages, browser password managers, and form inputs.
Now, the information security experts report yet another type of surreptitious data collection by third-party scripts that we discovered: the exfiltration of personal identifiers from websites through “login with Facebook” and other such social login APIs. Specifically, we found two types of vulnerabilities.
- seven third parties abuse websites’ access to Facebook user data
- one third party uses its own Facebook “application” to track users around the web.
Third parties piggyback on Facebook access granted to websites
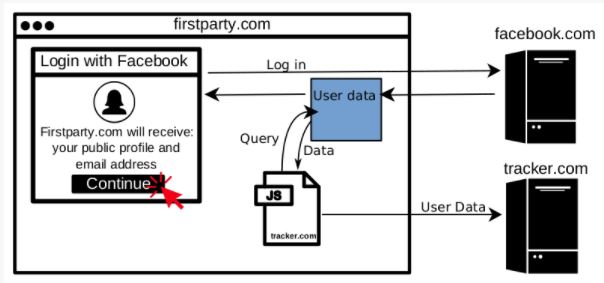
When a user clicks “Login with Facebook”, they will be prompted to allow the website they’re visiting to access some of their Facebook profile information. Even after Facebook’s recent moves to lock down the feature, websites can request the user’s email address and “public profile” (name, age range, gender, locale, and profile photo) without triggering a manual review by Facebook. Once the user allows access, any third-party Javascript embedded in the page, such as tracker.com in the figure above, can also retrieve the user’s Facebook information as if they were the first party.
Facebook Login and other social login systems simplify the account creation process for users by decreasing the number of passwords to remember. But social login brings risks: Cambridge Analytica was found misusing user data collected by a Facebook quiz app which used the Login with Facebook feature. Researchers have found an additional risk: when a user grants a website access to their social media profile, they do not only trust that website, but also third parties embedded on that site.
The information security professionals also found seven scripts collecting Facebook user data using the first party’s Facebook access. These scripts are embedded on a total of 434 of the top 1 million sites. The professionals detail how they found these scripts in Appendix 1 below. Most of them grab the user ID, and two grab additional profile information such as email and username.
The user ID collected through the Facebook API is specific to the website (or the “application” in Facebook’s terminology), which would limit the potential for cross-site tracking. But these app-scoped user IDs can be used to retrieve the global Facebook ID, user’s profile photo, and other public profile information, which can be used to identify and track users across websites and devices.
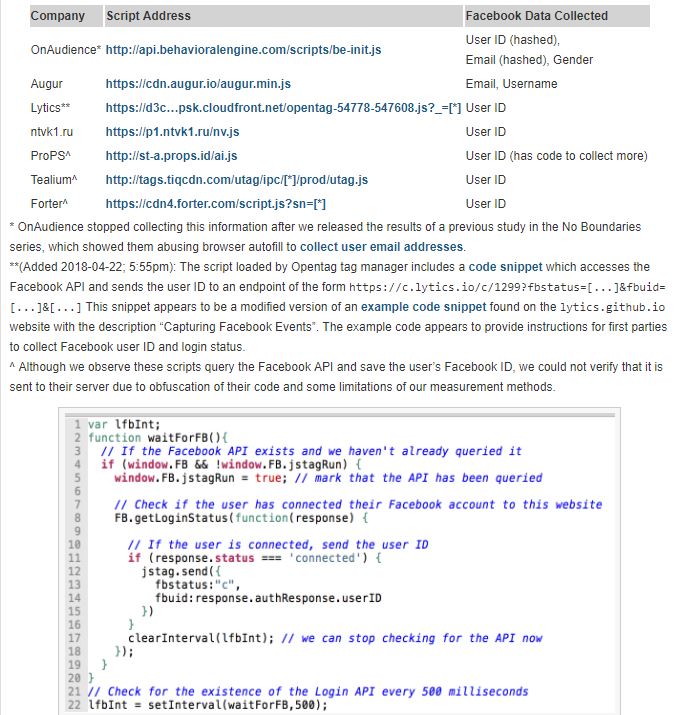
It is straightforward for a third party script to grab data from the Facebook API. The code is from the OpenTag script that exfiltrate the user’s Facebook ID to Lytics, a personalized Marketing and Customer Data Platform. The script continually checks for the existence of the Facebook API. Once the user logs in to Facebook, the tracking script can silently query the user’s login status. The response to the login status query contains the user’s Facebook ID, information security analysts say. The script then parses the ID out of the response and sends it back to a remote server.
While we can’t say how these trackers use the information they collect, we can examine their marketing material to understand how it may be used. OnAudience, Tealium AudienceStream, Lytics, and ProPS all offer some form of “customer data platform”, which collect data to help publishers to better monetize their users. Forter offers “identity-based fraud prevention” for e-commerce sites. Augur offers cross-device tracking and consumer recognition services.
Tracking users around the web with the Facebook Login service
Some third parties use the Facebook Login feature to authenticate users across many websites: Disqus, a commenting widget, is a popular example. However, hidden third-party trackers can also use Facebook Login to deanonymize users for targeted advertising. This is a privacy violation, as it is unexpected and users are unaware of it. But the information security professionals ask, how can a hidden tracker get the user to Login with Facebook? When the same tracker is also a first party that users visit directly. This is exactly what we found Bandsintown doing. Worse, they did so in a way that allowed any malicious site to embed Bandsintown’s iframe to identify its users.
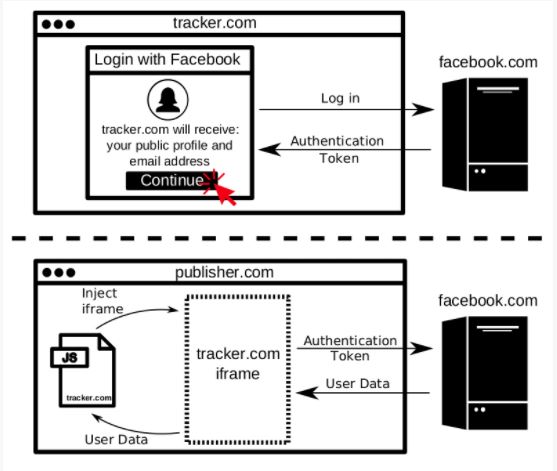
The information security experts also found that the iframe injected by Bandsintown would pass the user’s information to the embedding script indiscriminately. Thus, any malicious site could have used their iframe to identify visitors. We informed Bandsintown of this vulnerability and they confirmed that it is now fixed.
To conclude, the information security researchers say, that this unintended exposure of Facebook data to third parties is not due to a bug in Facebook’s Login feature. Rather, it is due to the lack of security boundaries between the first-party and third-party scripts in today’s web. Still, there are steps Facebook and other social login providers can take to prevent abuse: API use can be audited to review how, where, and which parties are accessing social login data. Facebook could also disallow the lookup of profile picture and global Facebook IDs by app-scoped user IDs. It might also be the right time to make Anonymous Login with Facebook available following its announcement four years ago.
Several companies stated that they do not use Facebook data for third-party tracking purposes.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











