An information security expert explains that, Archery is an open source vulnerability management and evaluation tool that helps developers and evaluators perform scans and manage vulnerabilities. Archery uses open source tools to perform a complete scan of the web application and the network. In the same way, this tool performs the dynamic authenticated scanning of the web application and covers the applications through the use of selenium. This tool can also be used for the implementation of a DevOps CI / CD environment.
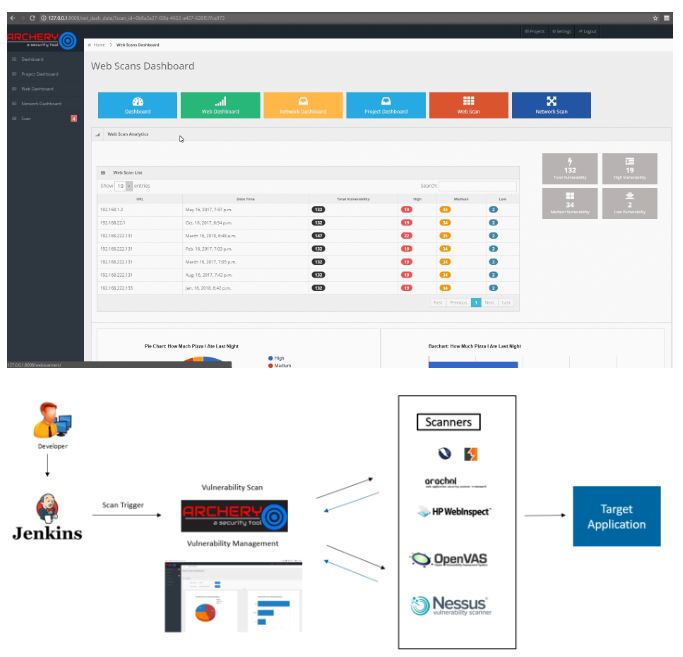
This is a small list of what the tool can do:
- Perform network and network vulnerability scans using open source tools.
- Correlates and collaborates all the data of scans without format, shows them in a consolidated way.
- Perform an authenticated web scan.
- Perform the exploration of the web application using selenium.
- Vulnerability Management.
- Enable the REST API for developers to perform vulnerability analysis and management.
- JIRA ticket sales system.
- Discovery and scanning of subdomains.
- Periodic scans
- Concurrent scans
- Useful for DevOps teams for vulnerability management.
The professional gave us a list of requirements:
- Python 2.7
- OpenVas 8
- OWASP ZAP 2.7.0
- Selenium Python Firefox Web driver
You must enable the REST API Burp. You can manage and trigger scans using Archery once the REST API is enabled.
Setup Setting
ZAP running daemon mode
For Windows: zap.bat -daemon -host 0.0.0.0 -port 8080 -config api.disablekey=true -config api.addrs.addr.name=.* -config api.addrs.addr.regex=true
For other: zap.sh -daemon -host 0.0.0.0 -port 8080 -config api.disablekey=true -config api.addrs.addr.name=.* -config api.addrs.addr.regex=true
The information security professional gives us directions for configuring Zap.
- Go to the configuration page
- Edit the ZAP settings or browse the URL: https: // host: port / setting_edit /
- Fill in the required information.
- Zap API key: leave it blank if you use ZAP as daemon api.disablekey = true
- Zap API Host: your host API zap IP or system IP ex. 127.0.0.1 or 192.168.0.2
- Zap API port: ZAP execution port
Now, for the OpenVAS configuration.
- Go to the configuration page
- Edit the OpenVAS configuration or browse the URL: https: // host: port / networkscanners / openvas_setting
- Fill in the required information and save.
Road Map
Scanners parser & Plugin
- Nessus
- Netsparker
Popular Tools plugin support.
- SSL Analysis
- Nikto
Reporting
API Automated vulnerability scanning.
Vulnerability POC pictures.
Cloud Security scanning.
Is important to notice that currently the project is in the development phase and there is still a lot of work going on.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











