TL;DR Following the wrong link could allow remote attackers to control your WiFi router, Google Home, Roku, Sonos speakers, home thermostats and more.
The home WiFi network is a sacred place; your own local neighborhood of cyberspace. There we connect our phones, laptops, and “smart” devices to each other and to the Internet and in turn we improve our lives, or so we are told. By the late twenty teens, our local networks have become populated by a growing number of devices. From ? smart TVs and media players to ? home assistants, ? security cameras, refrigerators, ? door locks and?thermostats, our home networks are a haven for trusted personal and domestic devices.
Many of these devices offer limited or non-existent authentication to access and control their services. They inherently trust other machines on the network in the same way that you would inherently trust someone you’ve allowed into your home. They use protocols like Universal Plug and Play (UPnP) and HTTP to communicate freely between one another but are inherently protected from inbound connections from the Internet by means of their router’s firewall ?. They operate in a sort of walled garden, safe from external threat. Or so their developers probably thought.
A few months ago, I began to follow a winding path of research into a 10 year-old network attack called DNS rebinding. Put simply, DNS rebinding allows a remote attacker to bypass a victim’s network firewall and use their web browser as a proxy to communicate directly with devices on their private home network. By following the wrong link, or being served a malicious banner advertisement, you could inadvertently provide an attacker with access to the thermostat that controls the temperature in your home.
NOTE: This research has been simultaneously released with a counterpart WIRED article on the subject by Lily Hay Newman.
What is DNS Rebinding?
To better understand how DNS rebinding works it’s helpful to first understand the security mechanism that it evades; the web browser’s same-origin policy. Many moons ago, browser vendors decided it probably wouldn’t be a good idea for web pages served from one domain to be able to make arbitrary requests to another domain without explicit permission from that second domain. If you follow a malicious link on the web, the web page you arrive at shouldn’t be able to make an HTTP request to your bank website and leverage your logged in-session there to empty your account. Browsers restrict this behavior by limiting HTTP requests originating from a domain to access only other resources that are also located on that domain (or another domain that explicitly enables cross-origin resource sharing).
DNS can be abused to trick web browsers into communicating with servers they don’t intend to.
The code at https://malicious.website can’t make a standard XMLHttpRequest to https://bank.com/transfer-fund because malicious.website and bank.com are different domains and therefor the browser treats them as separate origins. Browsers enforce this by requiring that the protocol, domain name, and port number of a URL being requested is identical to the URL of the page requesting it. Sounds good, right?
Not so fast. Behind every domain name lies an IP address. malicious.websitemay reside at 34.192.228.43 and bank.com may call 171.159.228.150 home. The Domain Name System (DNS) provides a useful mechanism of translating easy-to-remember domain names into the IP addresses that our computer’s actually use to talk to each other. The catch is that modern browsers use URLs to evaluate same-origin policy restrictions, not IP addresses. What would happen if the IP address of malicious.website were to quickly changed from 34.192.228.43 to the IP address of 171.159.228.150? According to the browser, nothing would have changed. But now, instead of communicating with the server that originally hosted the website files at malicious.website, your browser would actually be talking to bank.com. See the problem? DNS can be abused to trick web browsers into communicating with servers they don’t intend to.
DNS rebinding has received a few brief moments of attention over the past year when vulnerabilities were found in a few popular pieces of software. Most notably, Blizzard’s video games, the Transmission torrent client, and several Ethereum cryptocurrency wallets were vulnerable to DNS rebinding attacks until recently. In just the wrong circumstance, the Ethereum Geth vulnerability could have given a remote attacker full-control of the victim’s Ethereum account, and with it, all of their coin.
DNS rebinding allows a remote attacker to bypass a victim’s network firewall and use their web browser as a proxy to communicate directly with devices on their private home network.
How DNS Rebinding works
- An attacker controls a malicious DNS server that answers queries for a domain, say
rebind.network. - The attacker tricks a user into loading
https://rebind.networkin their browser. There are many ways they could do this, from phishing to persistent XSS or by buying an HTML banner ad. - Once the victim follows the link, their web browser makes a DNS request looking for the IP address of
rebind.network. When it receives the victim’s DNS request, the attacker controlled DNS server responds withrebind.network’s real IP address,34.192.228.43. It also sets the TTL value on the response the be 1 second so that the victim’s machine won’t cache it for long. - The victim loads the web page from
https://rebind.networkwhich contains malicious JavaScript code that begins executing on the victim’s web browser. The page begins repeatedly making some strange looking POST requests tohttps://rebind.network/thermostatwith a JSON payload like{“tmode”: 1, “a_heat”: 95}. - At first, these requests are sent to the attacker’s web server running on
34.192.228.43, but after a while (browser DNS caching is weird) the browser’s resolver observes that the DNS entry forrebind.networkis stale and so it makes another DNS lookup. - The attacker’s malicious DNS server receives the victim’s second DNS request, but this time it responds with the IP address
192.168.1.77, which happens to be an IP address of a smart thermostat on the victim’s local network. - The victim’s machine receives this malicious DNS response and begins to point to HTTP requests intended for
https://rebind.networkto192.168.1.77. As far as the browser is concerned nothing has changed and so it sends another POST tohttps://rebind.network/thermostat. - This time, that POST request gets sent to the small unprotected web server running on the victim’s WiFi-connected thermostat. The thermostat processes the request and the temperature in the victim’s home is set to 95 degrees ?.
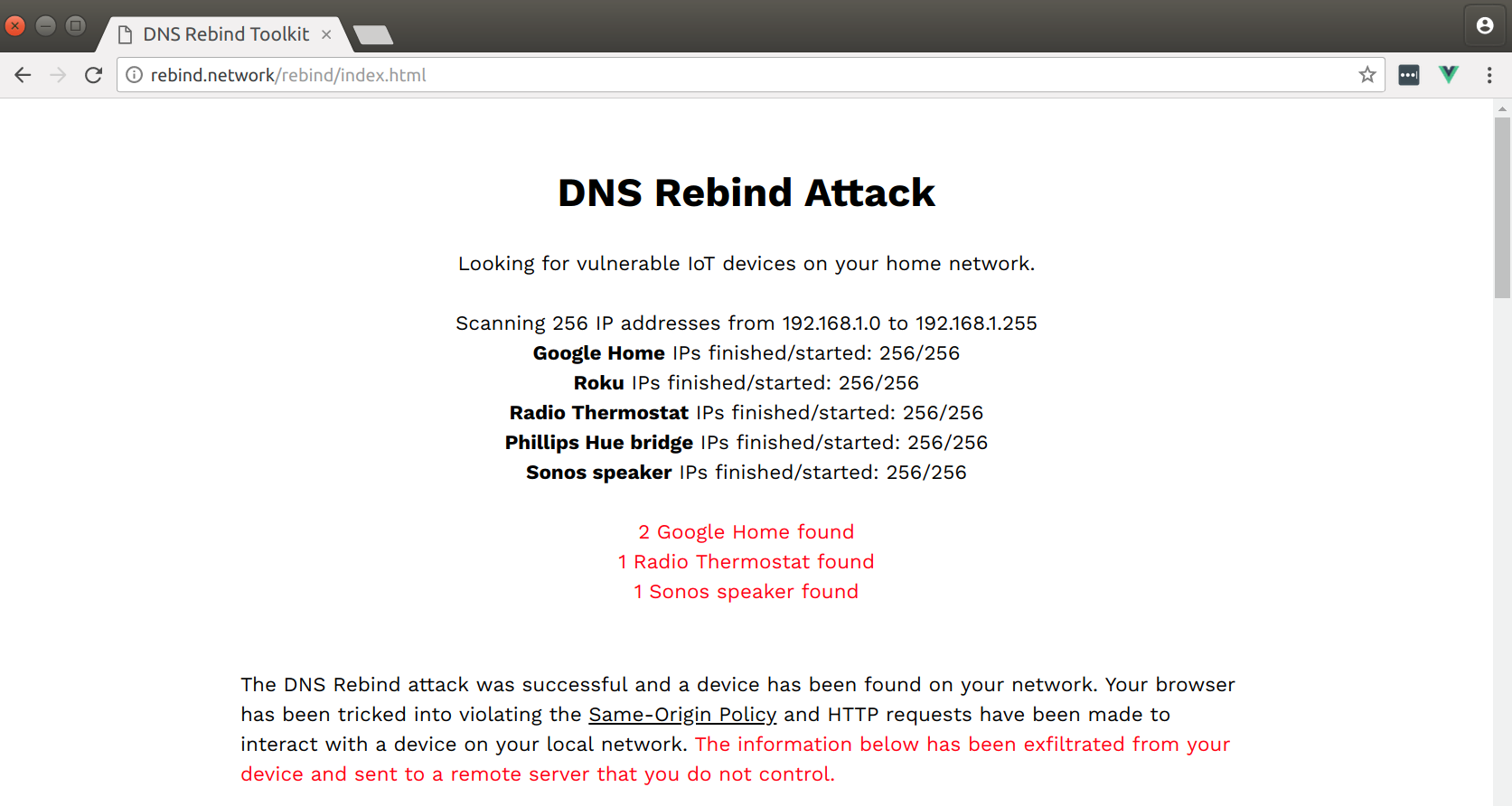
This scenario is an actual exploit (CVE-2018–11315) that I’ve found and used against my Radio Thermostat CT50 “smart” thermostat. The implications and impact of an attack like this can have far reaching and devastating effects on devices or services running on a private network. By using a victim’s web browser as a sort of HTTP proxy, DNS rebinding attacks can bypass network firewalls and make every device on your protected intranet available to a remote attacker on the Internet.
What’s Vulnerable?
After finding and exploiting this vulnerability in the very first device that I poked around with, I feared that there were likely many other IoT devices that could also be targeted. I began to collect and borrow some of the more popular smart home devices on the market today. Over the next few weeks every device that I got my hands on fell victim to DNS rebinding in one way or another, leading to information being leaked, or in some cases, full device control. Google Home, Chromecast, Roku, Sonos WiFi speakers, and certain smart thermostats could all be interfaced with in some way by an unauthorized remote attacker. Seems like a big problem huh?
The idea that the local network is a safe haven is a fallacy. If we continue to believe it people are going to get hurt.
I’ve been in contact with the vendors of these products and all of them are working on or have already released security patches (more on that disclosure in this essay). Those are just the companies whose devices I’ve personally tested in my spare time. If companies with such high profiles are failing to prevent against DNS rebinding attacks there must be countless other vendors that are as well.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.