We all know the media and information technologies play an important role in the political events of a country; therefore, it is important to think about their role on our society, especially in the middle of an election process.
The media condition our perception of the world; of course, its influence is also felt in our capability for political decisions making. Information security experts from the International Institute of Cyber Security affirm that, in an election, only 40% of the voters have decided for a candidate, 35% are undecided, and 25% of these people can be influenced by using statistical techniques and marketing during the political campaigns.
There are different ways in which media and technology convince us or make us change our political preferences; massive surveillance, Facebook and Twitter accounts monitoring, and marketing campaigns are some of the strategies used in order to exert influence over our political preferences. Information security experts point out that there are mainly four methods to influence an election using the media: by changing the vote; manipulating the information that can change the vote, obstructing the vote; and undermining confidence in the vote.
How influence over the election process is exerted
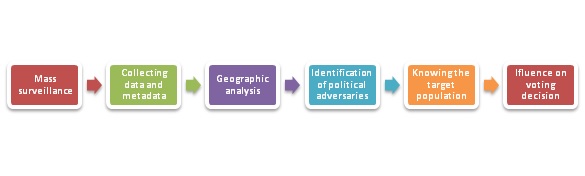
Influencing political decisions is a long process; the work begins about two years before the election. This task involves the use of:
1. Mass surveillance
2. Keywords data accumulation and metadata
3. Geographic analysis and segmentation of population
4. Identification of people or press reporters who may be against a political party
5. Geo-Marketing using digital media and traditional media focused on people identified.
Then comes the process of influencing the decision of the voters to vote for a candidate, where the collected data is used to know the target people to be attacked with different methods, to convince or change their minds on their political preferences.
As per cyber security experts from IICS, private companies help Governments and political parties, but this help is not free. A government or political party cannot legally allocate money to companies that help them reach power. Companies help Governments or political parties for a greater benefit than they could be paid at that moment, we all know that, Governments or political parties have different ways of paying for these “favors” when they reach power. Promised long-term business, privatization of markets, and even reforms that favor certain companies are some of the most common means of payment.
STEPS TO INFLUENCE THE ELECTORAL PROCESSES
MASS DIGITAL SURVEILLANCE AND KEYWORD ANALYSIS (NAME OF THE PARTY OR CANDIDATE OR OPPOSITION)
In simple words, mass surveillance happens when public or private actors control and compile lots of information about people’s behavior through their phones, computers and other devices. Information security experts claim that, as part of this vigilance task, companies and governments gain access to phone calls, emails, text messages and other conversations.
Mass surveillance includes spying on everything we do on the internet. The documents made public by Edward Snowden in 2013 revealed how intelligence agencies use mass surveillance to secretly collect, store, and analyze millions of private communications of people from all the world.
It is also known that the governments of the United States, United Kingdom, India, China, Japan, Mexico, Brazil and Russia have backend access to telecom providers, allowing them to spy on the voice and data of billions of mobile phones.
Information security companies and governments make use of different tools and techniques to do mass digital surveillance like:
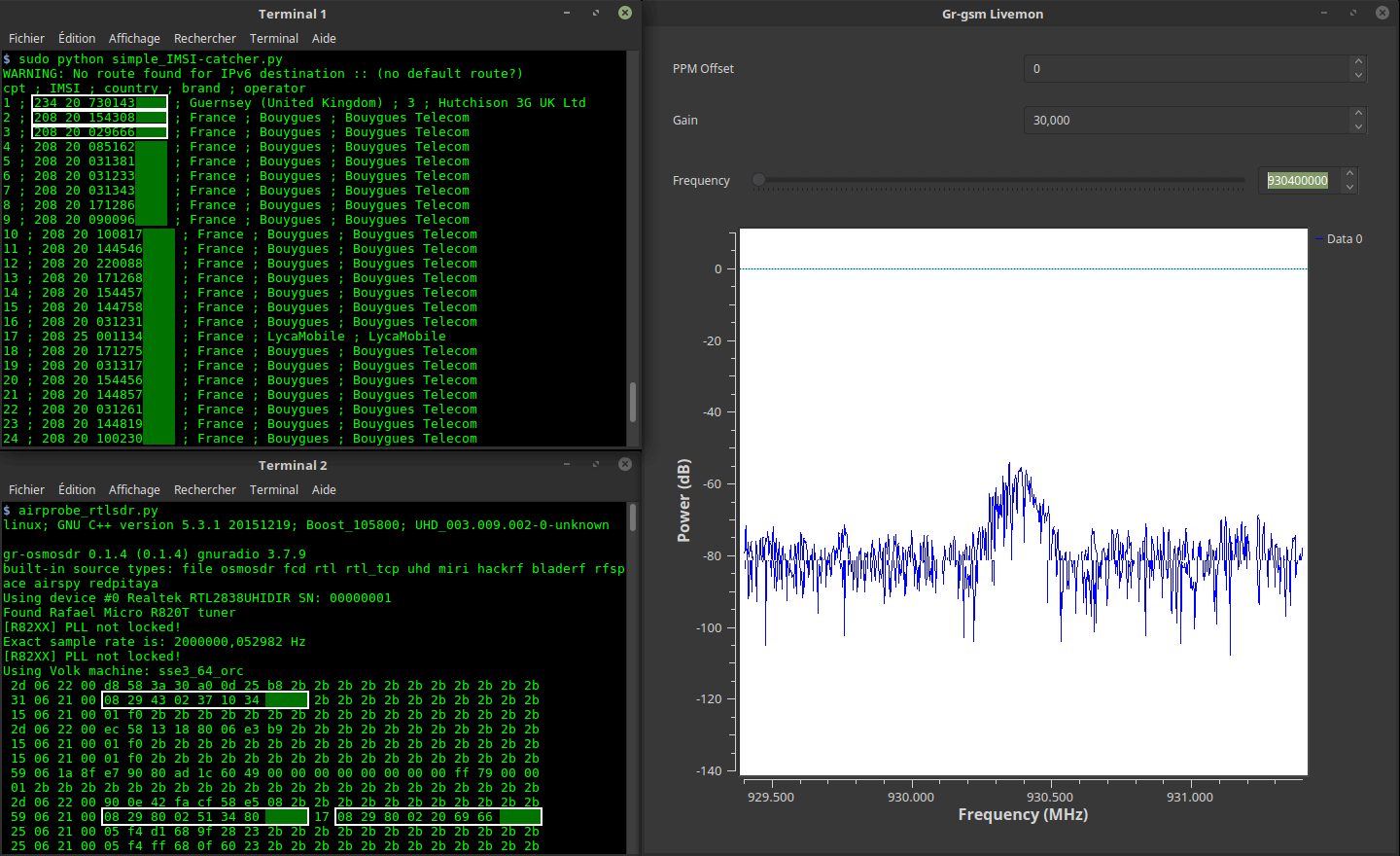
Intercepting mobile communications: In summary, vigilance of cell phones, calls, messages and emails using Stingray/Receiver IMSI Interceptor. Stingray is a device that can compile data from thousands of phones in specific areas and intercept conversations without hacking the mobile phones. There are several devices like these available on the market, like Gossamer, which is a small portable device equivalent to Stingray. According to information security analysts, the approximate cost of devices such as Gossamer on the black market in Mexico, Brazil and Argentina ranges between 10.000 and 20.000 dollars.


Collection of metadata via telecommunications companies: The massive collection of metadata via telecom providers is a sophisticated form of surveillance. All the people are under systematized surveillance, with this the operators that offer telecommunications services are forced to collect and to preserve, the metadata of the communications of their users. This type of metadata is a digital diary of a person’s daily life, you can see textually what they does, where political parties they support based on the keywords detected during their calls or messages and what their routines are and if they change places, what people are nearby and how a social circle is organized.
Back doors on smart devices: Information security experts say that there are back doors that affect millions of mobile devices. These backdoors can be pre-installed on the devices or can be generated by hackers. In cases where the vulnerabilities are pre-installed, these security holes in the code cause personal information to be sent to the device manufacturer, this information contains data such as the location of the phone, SMS or calls. Manufacturers collect this information; in addition, if the government has a relationship with manufacturers it can collect that information. Information security experts from WebImprints affirm that many Chinese phones like ZTE have backdoors that Chinese government use to collect data.
According to Information security specialist from International Institute of Cyber Security suggest that U.S. agencies collect 5 billion of mobile phone location records each day and share about 200 million text messages each day with agencies from different governments. Companies and governments also collect 42 billion Internet records, such as browsing histories, searches, emails and online chats, in a single month.
HOW DATA COLLECTED IN MASS SURVEILLANCE IS USED IN DIGITAL MEDIA TO INFLUENCE ELECTORAL PROCESS?
With the data collected in the mass surveillance can be sold to the government or to private companies. We all know how metadata (data about political preferences and likes, dislikes) of 50 million users was sold Cambridge Analytica and Nix. Russian operators used this data via Twitter and Facebook to spread messages against Hilary Clinton and promote the fake news.
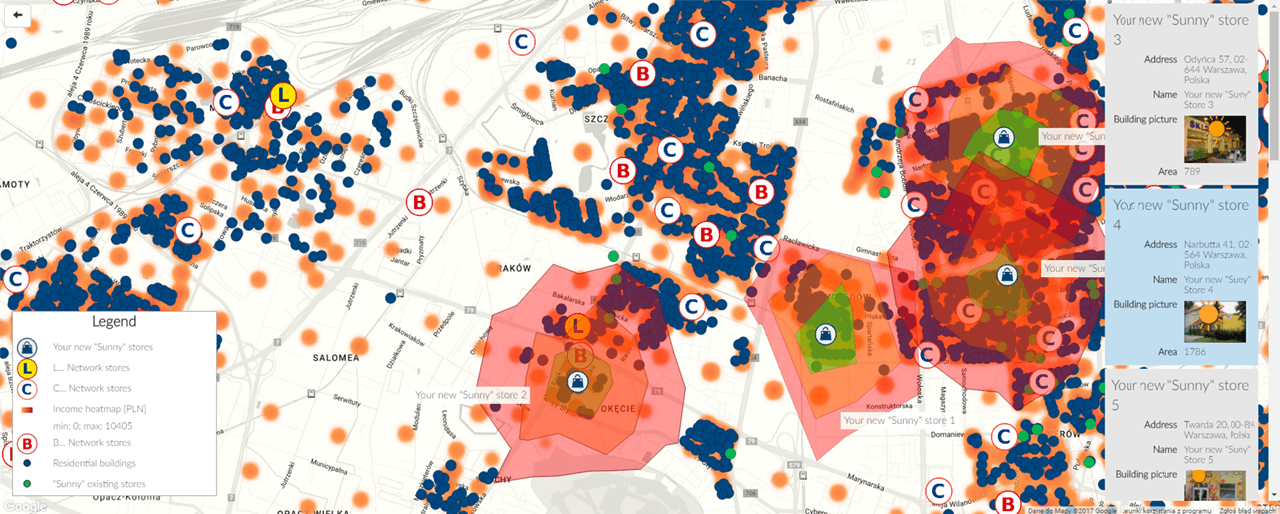
All the metadata collected can help a political party know which zones/states/zip codes they need to focus based on the age group of the population and political preferences. . Thanks to the information security tracking tools, the candidates know the people who are not sympathizers, the areas in which they are located and their daily activities; Based on this we identify the geographical areas in which the candidates should do marketing in order to reach the largest number of people in the opposition.
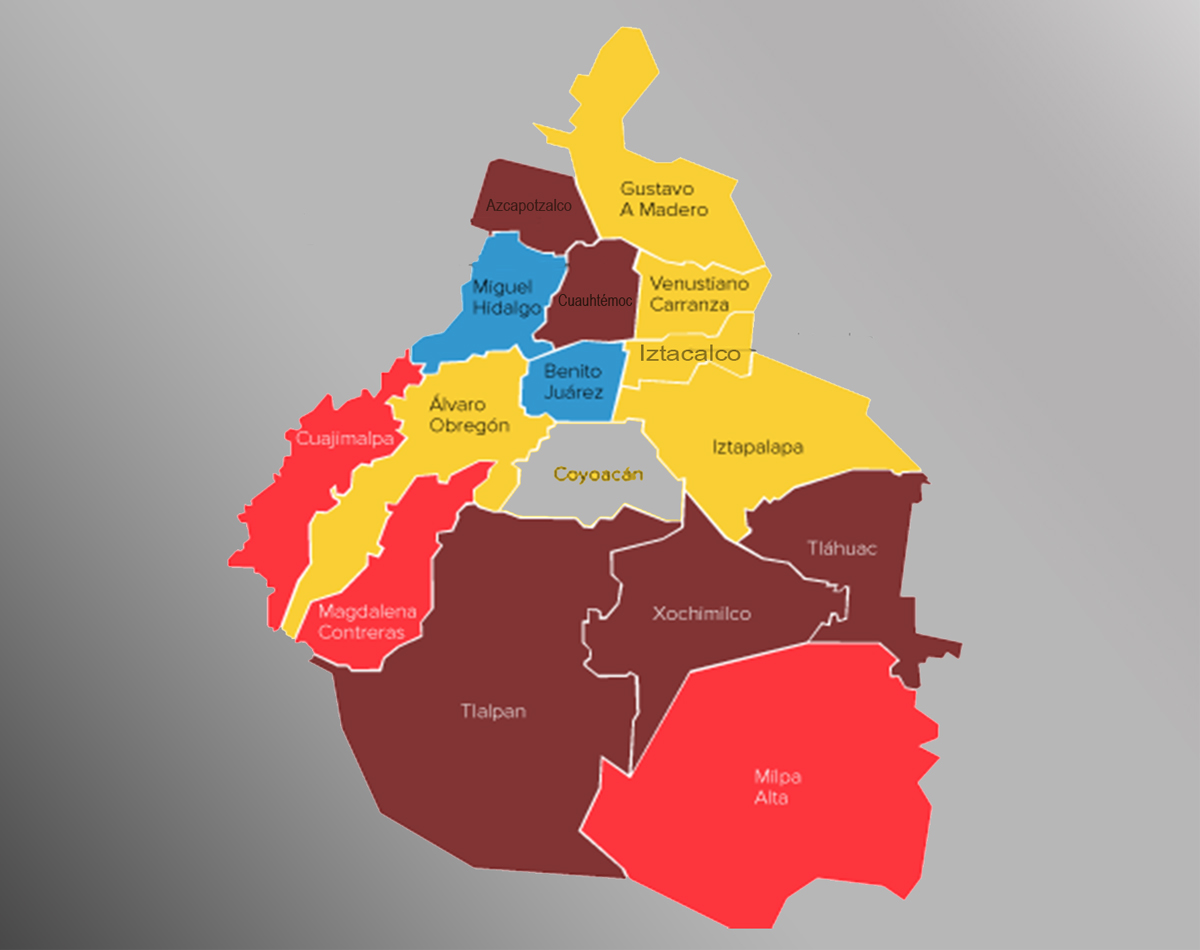
Here are some examples of the use of this data:
Political Geo-marketing: It is a marketing methodology that allows analyzing the situation of a political party; based on a mass surveillance study, shows which geographic areas have preference for a certain candidate and what is the profile of people with that preference, locating them on a digital map through personalized emblems and colors. As per information security experts from IICS, all this information is used to market a particular candidate or party in an area using digital advertisement or fake news in areas/county/state/zip code where he or she has less people supporting his party.
Google, Facebook Advertisements and Fake news campaigns on social networks: The population study made with the collected data allows the operation of the geographic segmentation, where it approves which political party advertisements appear in the geographical locations depending upon the previous searches of people or zones within a country or based on their metadata. As per information security experts, all this metadata is used to display ads of a political party or spread fake news against an political party in social networks like Facebook, WhatsApp or twitter based on geographic segmentation.
HOW DATA COLLECTED IN MASS SURVEILLANCE IS USED IN TRADITIONAL MEDIA TO INFLUENCE ELECTORAL PROCESS?
Information security specialists from the IICS mention that traditional media like physical ads, newspapers, radio and television are distinguished from the digital media as it reaches large audiences.
In the United States, Mexico, India, Brazil, among others, traditional media is more relevant and can change opinion of old generation easily. In terms of credibility and the ability to generate opinions, traditional media has more relevance. Traditional media has a better reputation than new digital media.
Using the data from mass surveillance about political preferences and geographic segmentation the political parties work with traditional media companies like newspaper, radio, television news channel and cable operators. The population analysis is carried out based on the geographical segmentation, to identify the people with certain inclinations in particular areas. The opposition is attacked with publicity. If a certain area is red, there will be no publicity for the red party, a yellow party advertising strategy will be created and vice versa, if a zone is in favor of the yellow party, a strategy for the red party is created. Below are strategies used for traditional media:
Advertisements in radio, newspapers or television channels: It is more common to see newspapers or magazines explicitly supporting a candidate or political party. Newspapers receive their revenues, making it easier for political parties and candidates to pay for a positive opinion in the publication. As read above, these media can be local and specialized, so candidates use once again the tools of tracking, mass surveillance and population analysis to meet the objectives and pay for publications focused on areas where they must reinforce the presence of a certain candidate or political party. Also a political parties or candidates can pay to promote an investigation to disqualify other candidates or political parties.

Pay Cable operators: As per Information security experts, with the help of cable operator parties can ask for change the channel number or remove of particular news channel that opposes a particular political party or the present government. Governments monetarily compensate cable companies and news channel for their “good behavior” by issuing official advertising contracts to companies or by providing bonuses to journalists.
Threat journalists: As per information security experts, parties can use surveillance and spy on journalists who oppose the government and are not easy to bribe so that these journalists can be threaten to change there reports.
Physical Announcements (brochures, billboards, etc.): This is another media that is commonly found in the hands of private companies, this is the media that has the greatest advantage in terms of visibility, as a billboard is placed in a suitable location based on data from mass surveillance and geo segmentation it can attract the gaze of millions of people daily.
How an authoritarian government can misuse this information?
Using the above powers governments/companies/political parties that misuse mass surveillance, to exercise an almost authoritarian regime or controlled democracy. According to information security specialist from International Institute of Cyber Security with this governments can limit freedoms of speech with media control and have a controlled democracy, that only benefits the people in power, as we can see in the following examples:
Controlled Democracy: A government that has a controlled democracy, where the ruler is not always the same person but the power is with a business group/ an elite group. This eliminates the possibility of discussing other development options, new paths or other forms of organization that could meet social needs.
Eliminate opposition parties: Governments can use mass surveillance made by information security companies to intervene their employee’s conversations and know who disagree with the government’s actions. Thus government eliminates people within the same Government who disagree with the regime. With this they get little opposition, which leads to the leaders can manage the nation to pleasure, an easy approval of reforms and new laws to help them stay in power
False opposition parties: LGovernments that eliminate all kinds of opposition and create a false opposition, where the same supporters serve as opposition to give a sense of democracy.
Complete control over law enforcement institutions: Using mass surveillance governments can locate and arrest people who represent a political threat to the government.
As we have seen, technology and media have their advantages and disadvantages, it depends on the people, governments, and companies how to use them and how much these can influence our political decisions. To know about the complete research behind this information security article please contact sarah.hogan@iicybersecurity.com.
Source:https://www.iicybersecurity.com/hack-government-elections-democracy.html

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.