Malware researchers always test their android users by introducing mobile banking Trojans into the Google Play store. There are lot of apps you can found in official Google play store like-Horoscope, Battery Managers, Torch, Customizing the screens, RAM boosters. Sometimes these apps tend to ask unnecessary permissions. Nowdays you can see Hackers always try to infect Mobile Banking apps to steal Banking accounts credentials to get their username and passwords. And these Trojans work on remotely basis. Yes, apps which users have installed in their smartphones can also work on remote execution if these apps are infected. These apps can also be used on remotely basis that the hacker can control over your smartphone. Hence, Android is an open platform.
Android structures have designed on open source tools which are easily available in the market. There are lot of android developers, some developers are in their initial phases of developing an app. Some are experienced. The main thing with new developers always happen that if they try to learn some new technology they don’t care much about the security. Might be this happen because of the growing of competition in this sector. Some developers want to make something innovative some are just for making money.
As in screen shot we can see some of the infected apps that can infect your smartphone and steal all the important information that you don’t want to share Most common apps which I have mentioned are on their app categories. If you look at Google play store stats of these apps you will see that these apps are actually installed by 30,000 users in total.
HOW DOES THESE APPS INFECT THE ANDROID MOBILE?
Once a user have installed these apps and launched them in their mobile. Some of the basic errors occur after launching of the apps. For example- It shows the error of that INSTALLED APPLICATIN IS INCOMPATIBLE WITH YOUR PHONE, IT SHOWS ERROR RETRIEVING INFORMATION FROM THE SERVER(RH01),net::ERR_FILE_NOT_FOUND FILE NOT FOUND. The above error sometimes act as an malware which get installed in their backbone. These malwares are encrypted in backend code which user have written in each functionality. This payloads are created with meterpreter using reverse_tcp handlers. Now days it’s easy to make an infected app. Sometimes these infected works on Google Play store. In the below screen shot we can see the code of an app. In mobile banking apps the first phase is to check the malware’s activity by using an encoded payload, using base64 and makes it encrypted using hardcoded key.
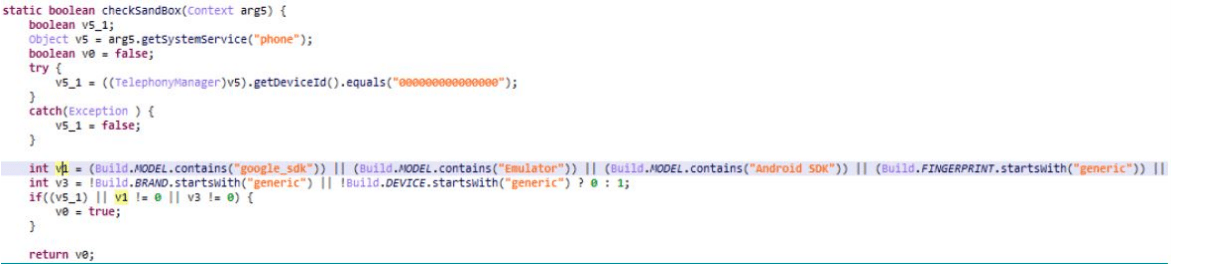
The initial stage of malware is to check presence of emulator or a sandbox using dropper. If that check fails then it easily drops a payload and here the payload which contains banking malware starts, what it is tend to be. Some of the apps which I have analyzed contains one or more encrypted payloads.
The infected payload which have started to infect the banking app installed on victim device, it starts intercepting, and send SMS messages, and download install additional apps of hacker’s choice. If a device is compromised any app can be installed that can impersonate the malware. After comprising the device any app can get infected with the malware when they are launched, by making an amiss situation and giving victim little chance.
SO WHAT’S THE SOLUTION?
Don’t trust any app easily always do check when installing from the Google play store check the rating of the app before installing. Go through comment section what others are saying about the app. Don’t use any third party store to install any app. Those apps might be infected. Check you smartphone settings. Go to Application manager/App manager if found any app suspicious simply uninstall them. Always pay attention while installing any app that what permission app is asking. You are advised to check your bank account for any unknown transactions. And do regularly change your Net banking passwords to stay safe.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.