Use
You should use this with docker. According to digital forensics specialists from the International Institute of Cyber Security, all you have to do is send this command:
$ mkdir /tmp/webmap
$ docker run -d \
–name webmap \
-h webmap \
-p 8000:8000 \
-v /tmp/webmap:/opt/xml \
rev3rse/webmap
$ # now you can run Nmap and save the XML Report on /tmp/webmap
$ nmap -sT -A -T4 -oX /tmp/webmap/myscan.xml 192.168.1.0/24
Now point your browser to https://localhost:8000
Quick and easy
$ curl -sL https://bit.ly/webmapsetup | bash
Upgrading from the previous version
$ # stop running webmap container
$ docker stop webmap
$ # remove webmap container
$ docker rm webmap
$ # pull new image from dockerhub
$ docker pull rev3rse/webmap
$ # run WebMap
$ curl -sL https://bit.ly/webmapsetup | bash
Run without docker
This project is designed to run in a Docker container. In the opinion of cybersecurity specialists and digital forensics, it is not a good idea to run this in a custom installation of Django, but if you need it, you can find all the construction steps within the Dockerfile.
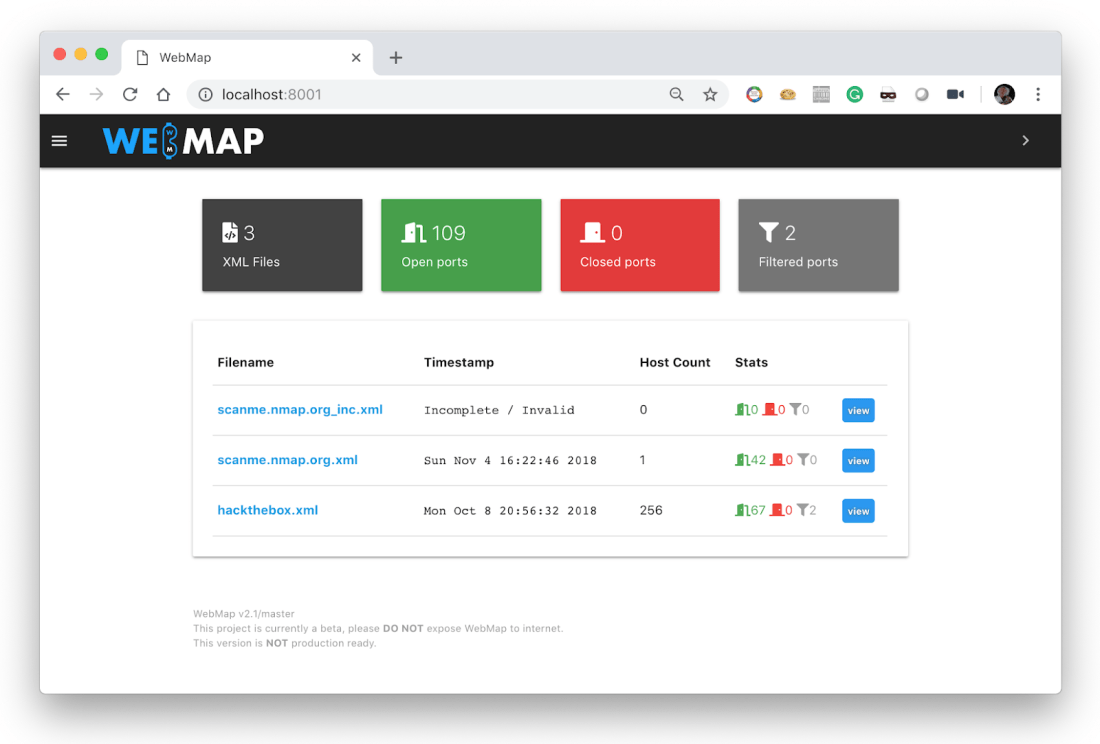
Features
- Importing and analyzing Nmap XML files
- Statistics and graphs of uncovered services, ports, operating systems, etc.
- Inspect a single host by clicking on its IP address
- Attach tags to a host
- Insert notes to a specific host
- Generate a PDF report with graphics, details, tags and notes
- Look for vulnerabilities and exploits based on the CPE compiled by Nmap
Variations on v2.1
- Better use of Django template
- Corrected Nmap XML analysis problems
- Exploits and vulnerabilities collection issues fixed
- A new network view was added
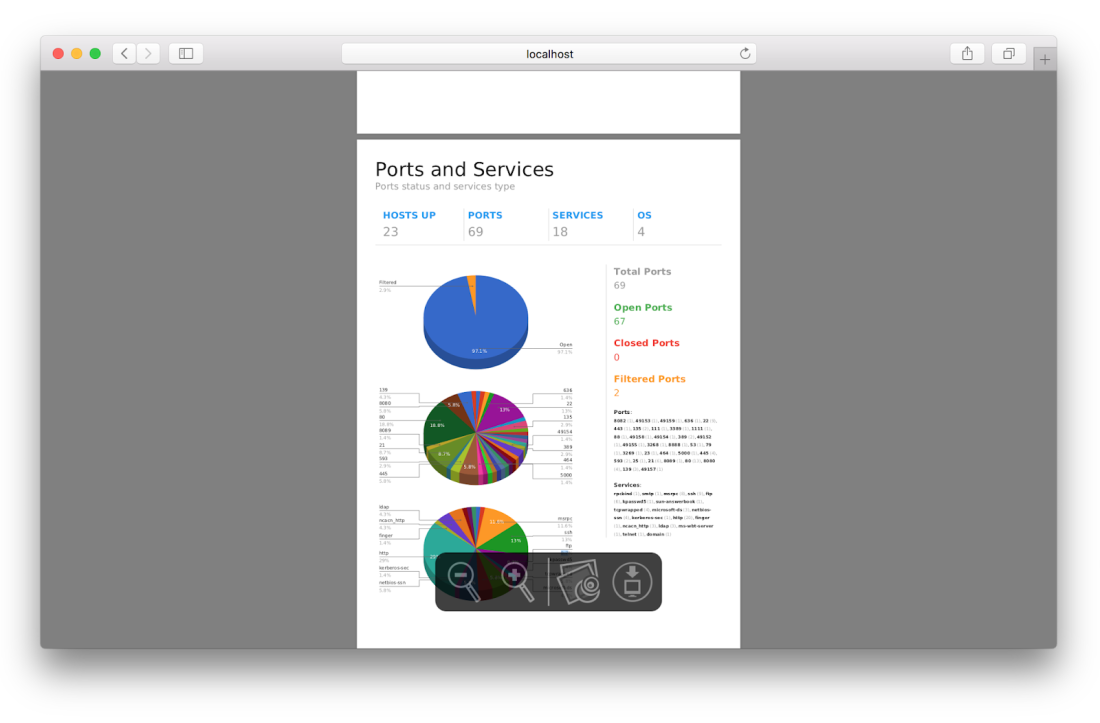
PDF report generation
XML filenames
When the PDF version of the Nmap XML report is created, the XML file name is used as the document title on the first page. According to experts in digital forensics, WebMap will replace some parts of the filename in the following way:
‘_’ will be replaced by a space
‘.xml’ will be deleted
Example: ACME_LTD..xml
PDF title: ACME Ltd.
Vulnerabilities and exploits
Thanks to Circl.lu’s incredible API services, WEBMAP can search for vulnerabilities and exploits for each CPE compiled by Nmap. Not all CPE are verified through the circl.lu API.
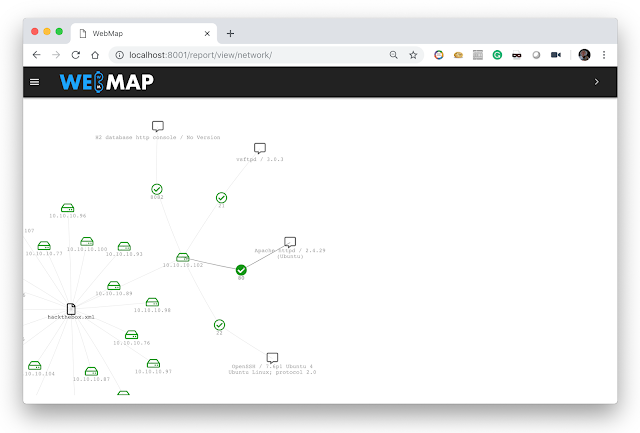
Network view
Security issues
This application is not intended for its Internet exposure. Developers recommend the user to use only their local host or, in case you cannot, be careful to filter who can access WebMap with a firewall rule or something like that. Exposing this application on the Internet could lead not only to a XSS condition, but also to a leak of confidential information about scanning your port. Please be smart when using WebMap.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.