INTRODUCTION:- In this digital era, our information is more public than private. The massive growth of internet users is increasing day by day. What we think we simply search it on the internet. Here privacy becomes a big concern for every internet user, according to ethical hacking courses. There are many genuine reasons why an internet user should stay anonymous. Reasons ranging for new companies growth to hiding personal information while surfing the internet.
Ethical hacking researcher of International Institute of Cyber security says that internet is insecure place for everyone. While surfing the internet everyone should stay anonymous and always use anonymous services.
That’s where anonymous services are used. There are many web applications who protect internet user privacy while surfing, explain ethical hacking experts.
Anonymity Comes in Two Essential Parts:-
- Browser – This is everyone’s primary source from where an user enters the internet. Browser always track user activities on internet. It is hard to configure the browser manually for not to reveal user information.
- Networking Components – There are many network devices that are used while surfing the internet. What you search on the internet the request is directly send to ISP (Internet Service Provider). Means that ISP can easily watch every internet user all the time and records it.
Anonymouus Services:-
- P2P Services – P2P is a decentralized network that transfers data from peer to peer (users to users). This network has no server. It can be secure because no one is watching but can be potentially insecure as anyone can log information about data transfers through.
- Proxies:- Proxies act as a gateway between an user and the internet. It’s an intermediary separating end-point users from websites they visit. Proxy provide various level of security to the internet user, but finding proper working proxies becomes hard. As not all proxies are anonymous, some are insecure.
- VPN (Virtual Private Network) – A VPN connection creates an secure tunnel between two computers so they can communicate securely. It is essiential to use VPN in public networks. It can be insecure as remote server could log information about the data that you send and receive.
HOW TO BE ANONYMOUS ON INTERNET:
Here are some listed products which can be used to stay anonymous while surfing.
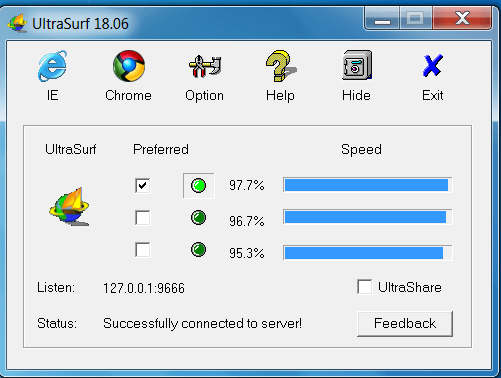
ULTRASURF:-
- Ultrasurf VPN is most popular VPN to stay anonymous.
- This VPN is very lightweight no installation is required, you have to simply download zip file.
- This VPN is free to use.
- This VPN connects a user to the USA servers to stay anonymous
- Unzip that file and directly run the VPN. The ultrasurf VPN looks like:-
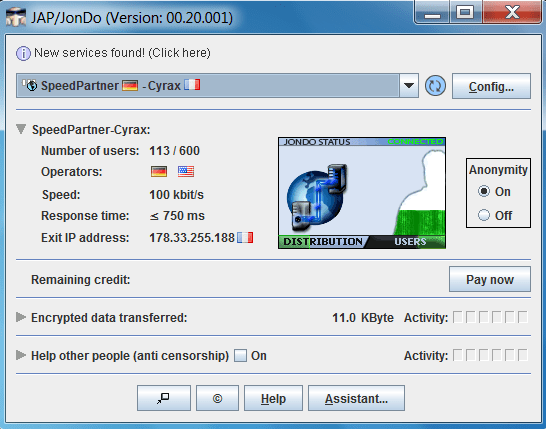
JONDO:-
- Jon Do is the another VPN written in Java. This VPN provides to stay anonymous.
- Simply download Jon do VPN and install and connect to external servers. This VPN has limited servers.
- You can also purchase the premium version to get more listed external servers.
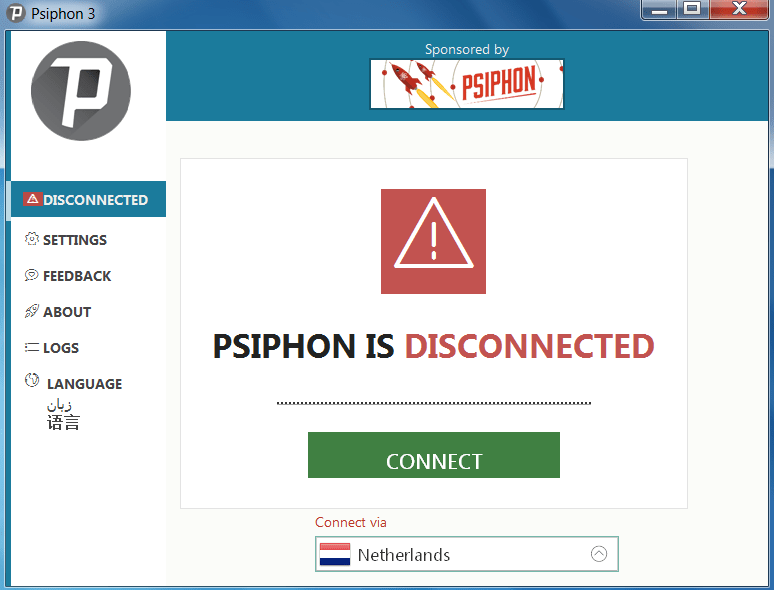
PSIPHON:-
- PSIPHON VPN used to provide internet users with open access to online content.
- Simply download the exe and directly open the exe. No need to install the any of the software.
- This VPN is free to use.
- Psiphon gives many options to connect with different countries like – Netherlands, Russia, USA , United Kingdom etc.
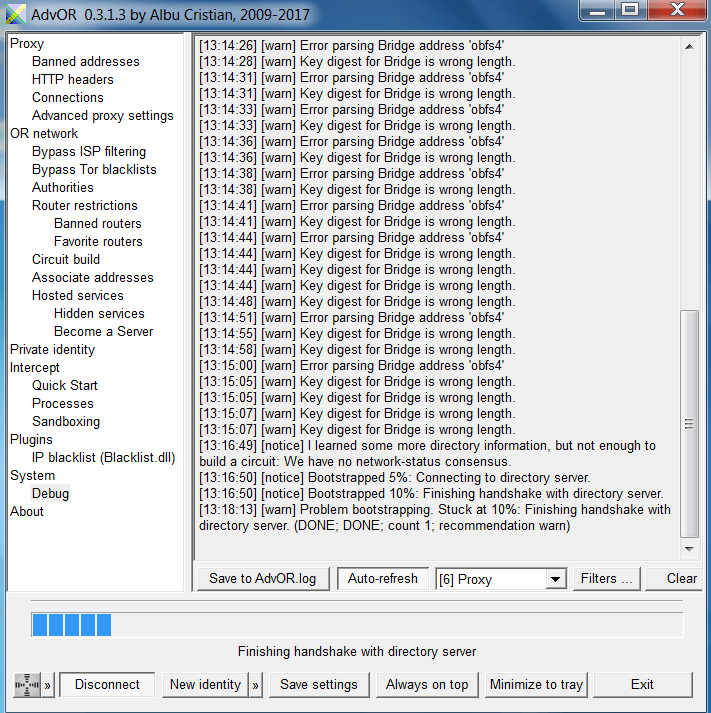
ADVANCE ONION ROUTER:-
- Advance onion router is build to force a program to use tor connection.
- This VPN can be customize with lots of features. For using the advance onion router.
- This VPN is very lightweight easy to use. No need to install the software simply run directly.
- For using the advance onion router setup the tor bridges inside the advance onion router.
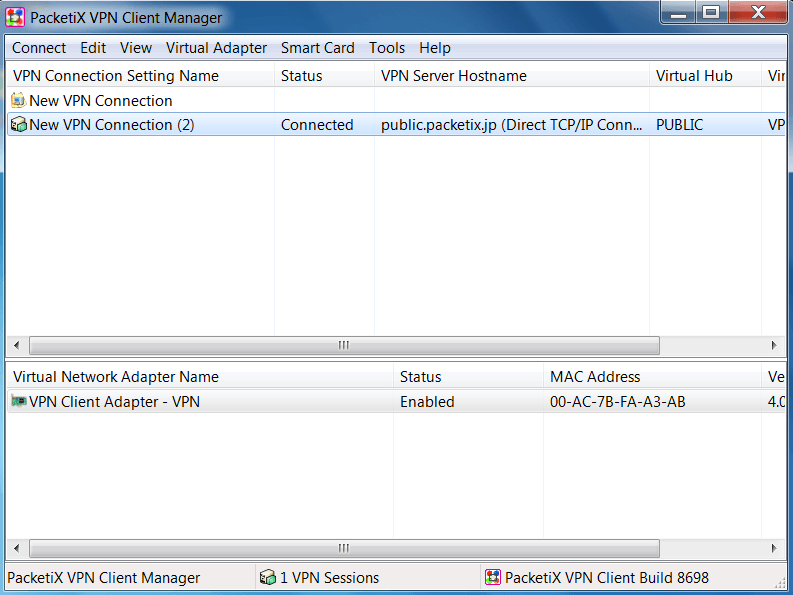
PACKETIX.NET:-
- PacketiX.net is the free VPN service offered by SoftEthen Corp.
- The GUI is very simple and easy to use. Simply configure the new connection.
- This VPN is run as an academic experiment by the university of Tasukuba in Japan.
- This VPN encrypts all your internet activity. The server location is Japan. Although they keep logs whoever uses this VPN and they are open about it.
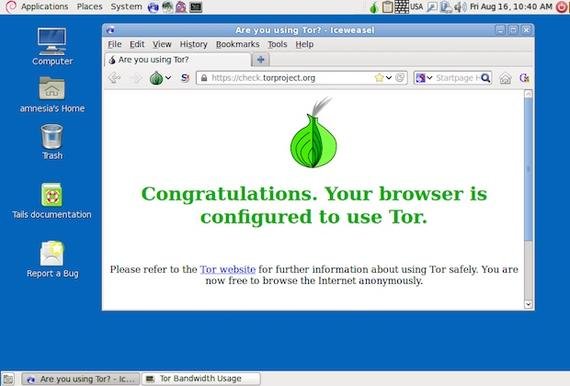
TAILS:-
- Tails is an debian linux based OS that is used to surf internet anonymously. This OS can be downloaded as an ISO file and then make bootable disk for using.
- Tails will automatically configure your internet connection. The GUI is very easy to use. You can surf internet anonymously.
- This OS boots live on ram and erased when shut down.
- In Tails all the traffic is routed through TOR.
- If you want to remove your evidence after work, simply us this.
HOW TO SEND ANONYMOUS EMAILS:-
There are many anonymous email services which are used to send mails. This service is mostly used by the pentesters.
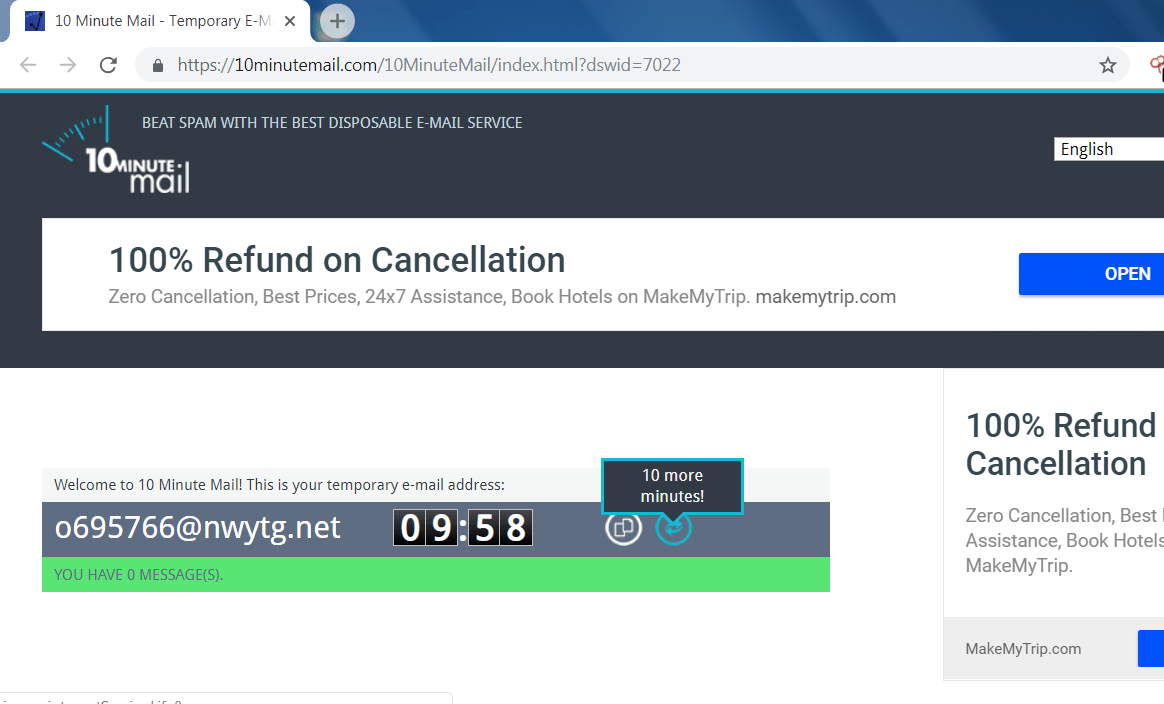
10MINUTEMAIL:-
- 10minutemail is used for singups and activation where you do want to put your original email id. 10minutemail cannot be used in sending an emails.
- This mail service is highly anonymous as it uses mail id is destroyed after 10 minutes.
- If you want to use the same mail, simply click on the 10 more minutes button.
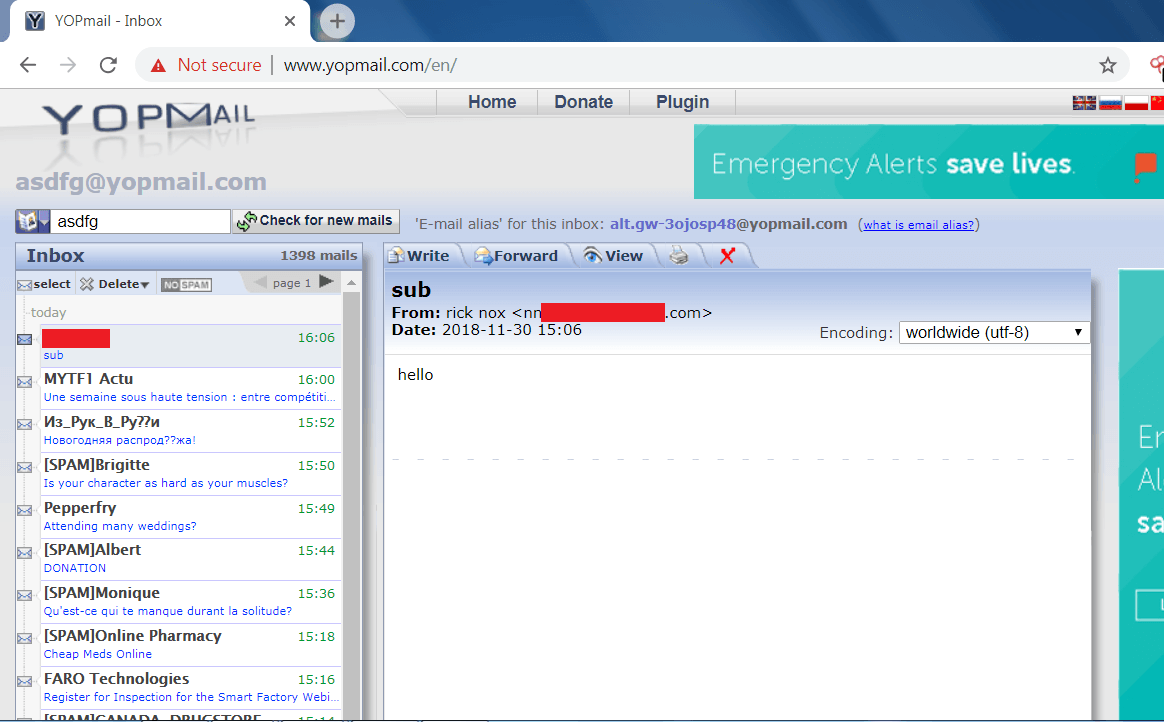
YOPMAIL:-
- Yopmail is the disposable mail service. It is used for activation on other sites where you don’t want to enter your original email ID.
- Be cautious before using this mail service as all mailboxes are public.
- In yopmail, the account last for 8 days. You can only send emails to other yopmail users.
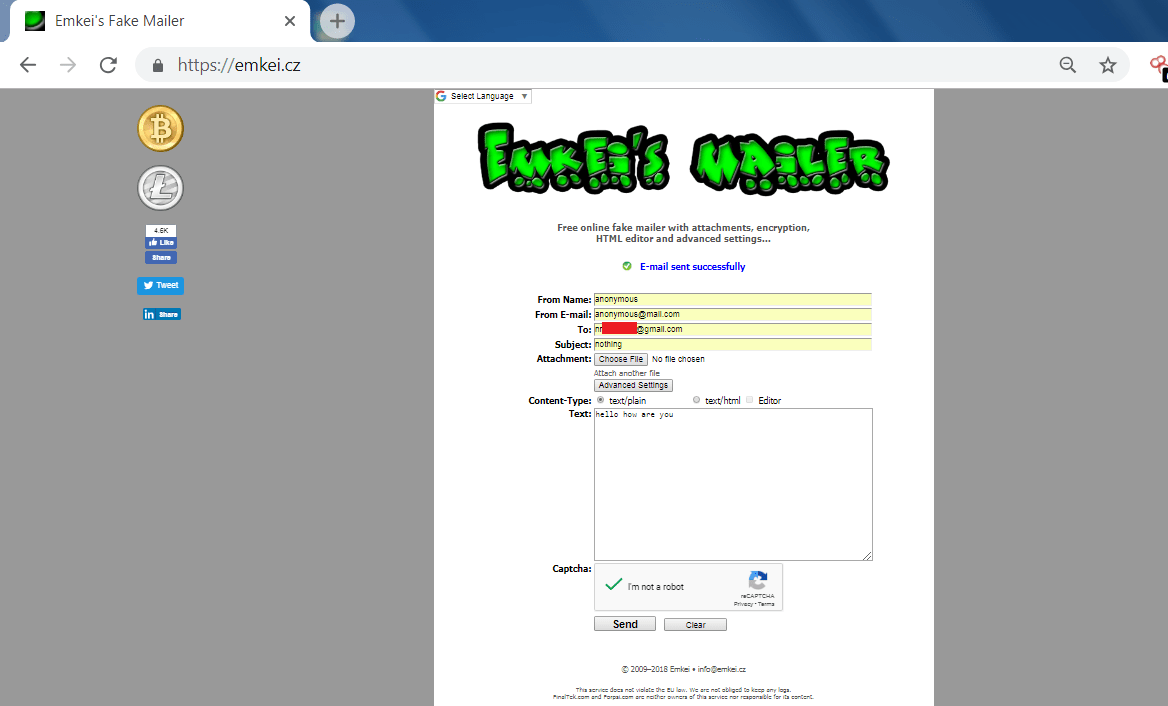
EMKIE’S FAKE MAILER:-
- Emkie’s Fake mailer is used to send the mails to any mail id.
- You can send mail anonymously. Here you can generate your own mail id. And you can send any file also.
- In below, as you can see we have send mail to check emkei’s mailer.
- After sending the mail to the gmail user. Now we will analyze the header of the received mail.
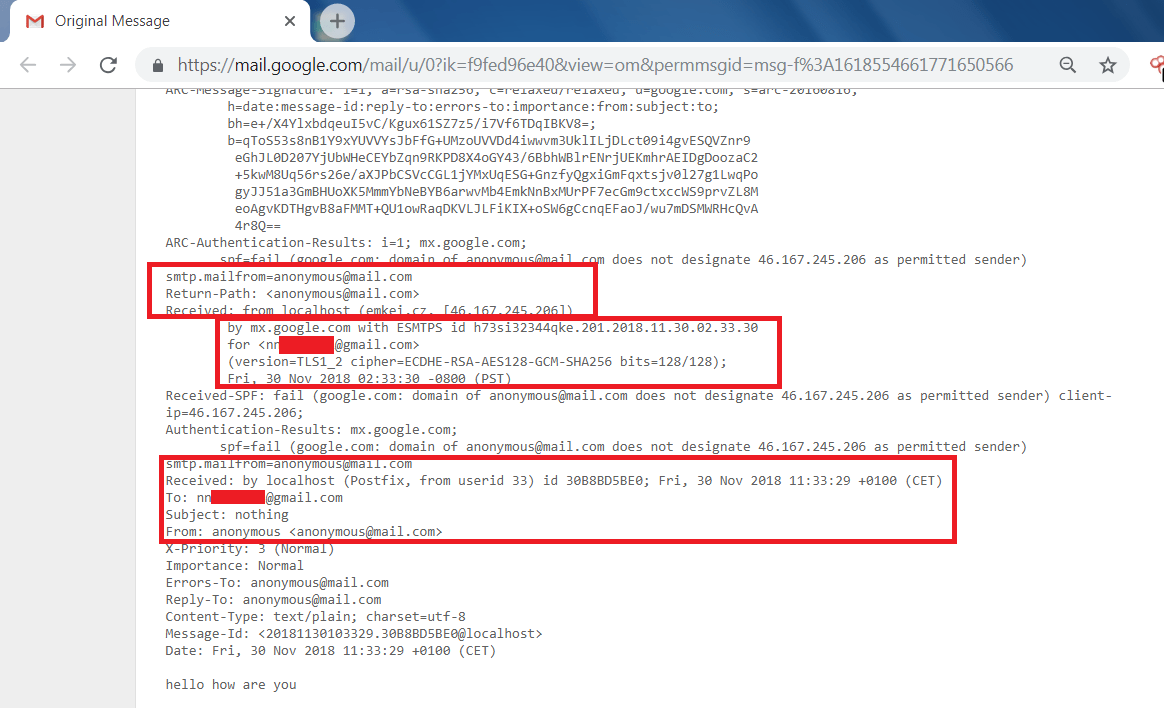
- In the above screen shot, Here are the details of the mail which has been received from the emkei’s fake mailer.
- In email header, Here is the name, date and IP address of the fake mailer.
vuvuzela
- Vuvuzela is a private messaging service by MIT
- It is a private chat application which hides user details on who you chatting with whom.
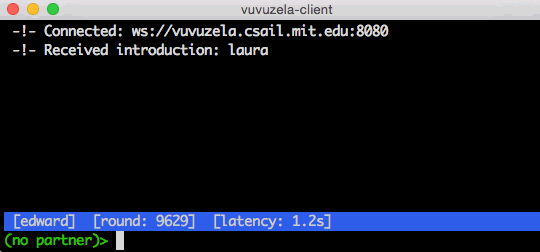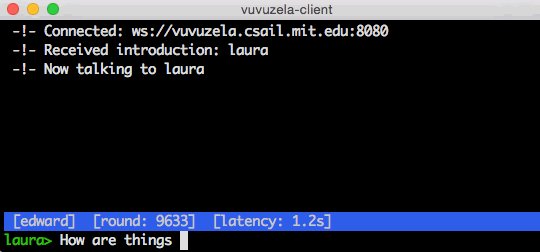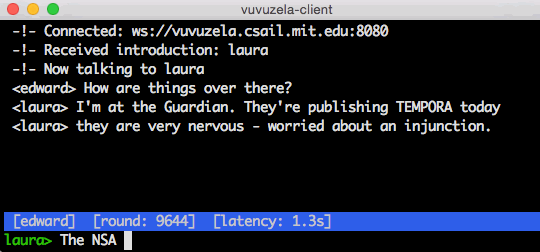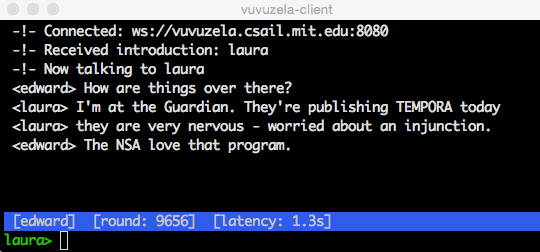
ANONYMOUS SEARCH ENGINES:-
There are many search engines such as – google which is the most common to search anything on the internet. But when comes to privacy, google lacks because google logs each and everything what user is searching using his search engine.
- There are many search engines like Duckduckgo which is powerful. This search engine does not keep any logs. You can use this search engine very easily. simply go to web browser and enter duckduckgo.com

- There are some another search engine startpage. This webpage is combined with google search results. The search engine is very easy to use it does not log any information. For those who are use to Google search engine and prefer not to expose their identitiy can use startpage.
HOW TO CHECK YOUR ANONYMITY:-
These websites tell you what information web browsers and the websites gathers, demonstrate ethical hacking professionals.
JONDONYM:-
- JonDoNym is the website which tells when any user visits the website. What website can obtain. There are tons of websites which try to gathers information about the user.
- JonDoNym provide many features like signatures, cookies, IP Whois, tab history, plugins and many information which directly violates user privacy.
- In the below screen shot, you will see the what information website has gathers.
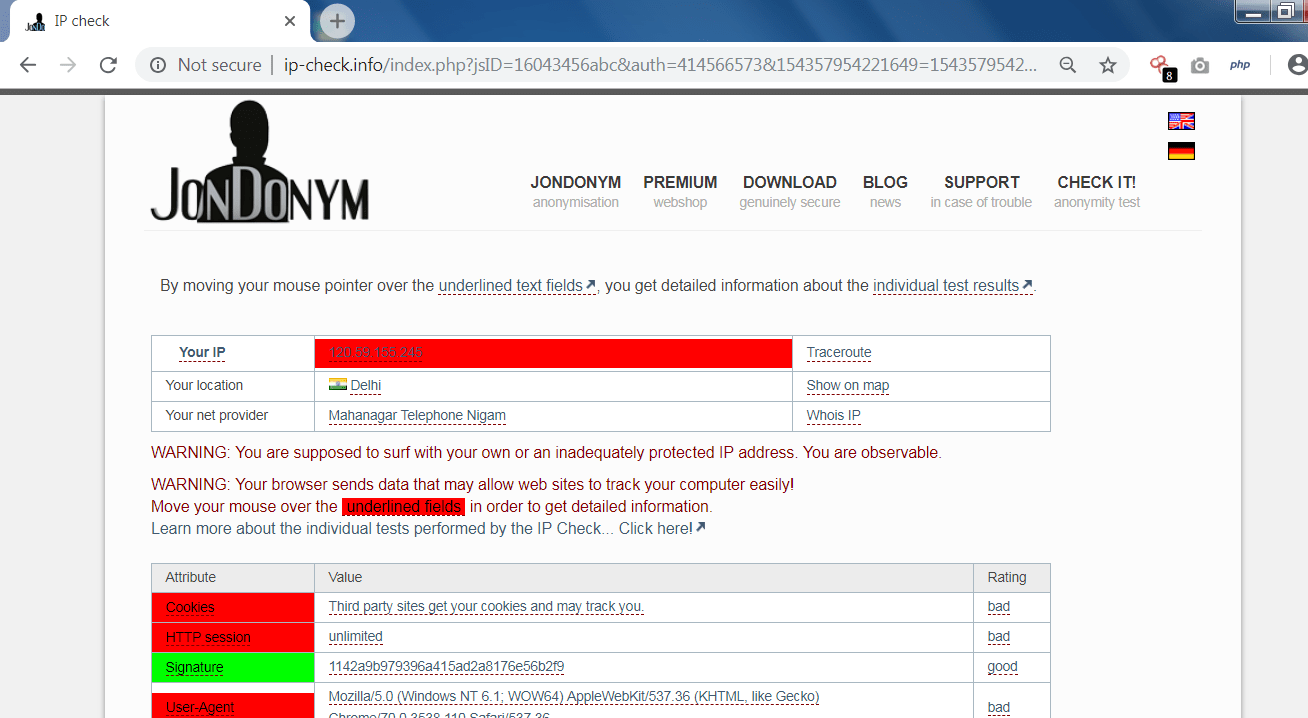
- In the above screen shot, website has gather IP , Local ISP, location, traceroute.
- The above information can be used in other hacking activities.
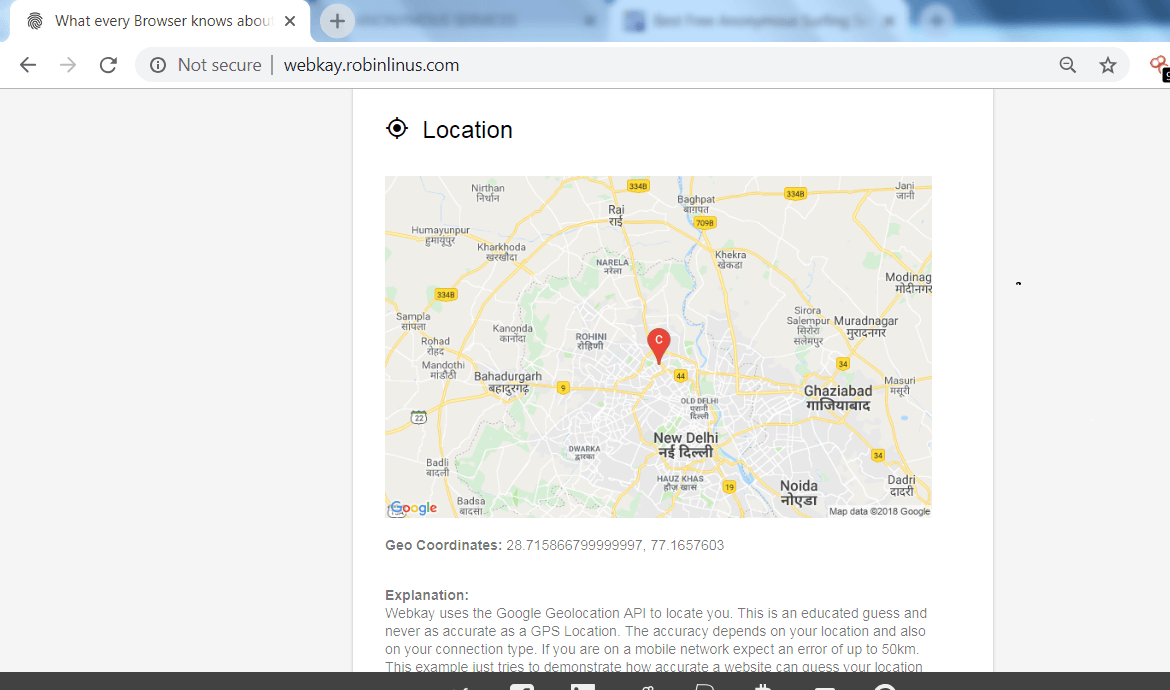
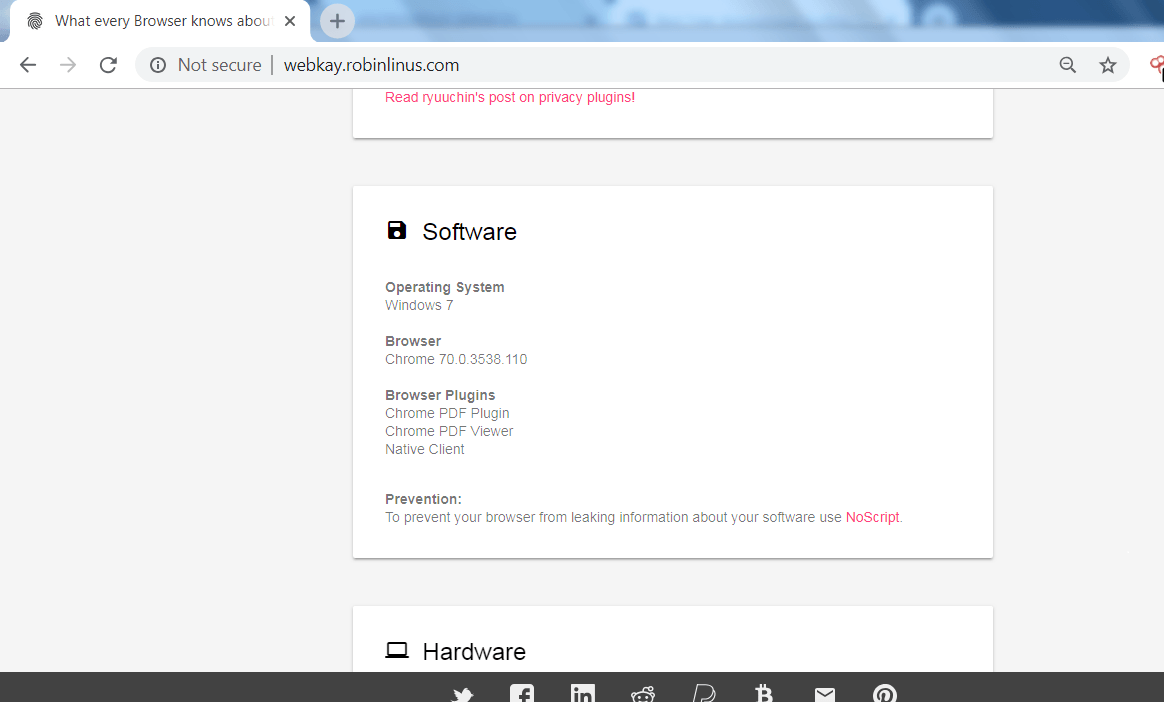
WEBKAY:-
- Webkay is the another site which tells that information like – Geo Coordinates, hardware and the software of the user computer.
===========================SNIP========================
============================SNIP======================
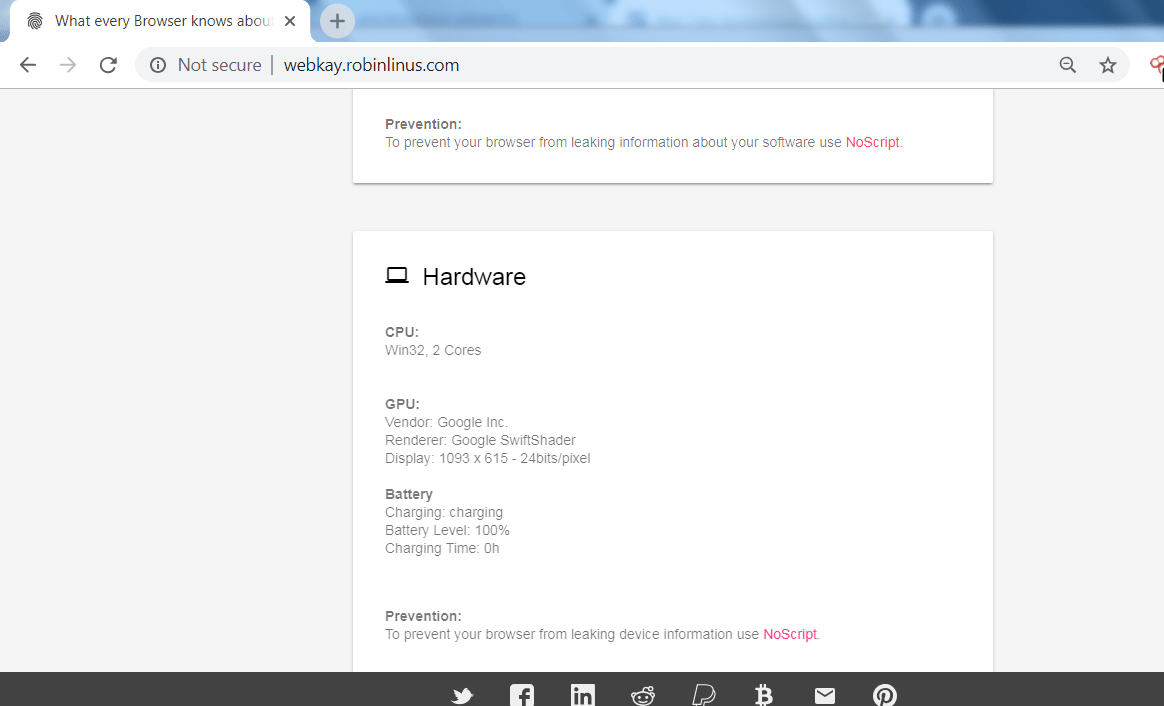
- In the above screen shot, the website has shown many of the data about the user’s browser like software on which user is surfing the internet, hardware specification. The above information can be used in other hacking activities.
International Institute of Cyber Security ethical hacking researchers always recommend penetration testers to be anonymous when doing black box penetration testing.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.