
The firm has already released update patches for several SMEs products
The Cisco technology firm recently launched update patches to address two critical vulnerabilities present in RV320 and RV325 routers, products widely used in small businesses. According to network security specialists, the first of these failures (CVE-2019-1653) could be exploited by remote attackers to access confidential information, while the second (CVE-2019-1652) is a command-injection flaw.
The real problem for Cisco is that some hackers have been attacking the RV320 and RV325 routers using new exploits. After public disclosure of the initial exploit concept test, hackers began searching for vulnerable devices on the Internet to try to compromise them.
Both vulnerabilities are found in the web management interface of the compromised routers, reported network security specialists from the International Institute of Cyber Security. By chaining the two flaws, a hacker can take control of these devices, attackers exploit vulnerabilities to obtain privileged passwords and execute arbitrary commands.
Specialists in a cybersecurity firm were responsible for reporting these flaws to Cisco, the code tests for exploitation were revealed to the public a few days after the company launched the update patches. Experts published the proof-of-concept for command-injection vulnerabilities, information disclosures, and data leakage.
When using Shodan to look for some of the compromised routers models, it is possible to find tens of thousands of these devices running online.
Troy Mursch, a network security specialist, performed his own scanning for vulnerable systems, discovering about 9.6k online exposed routers (6 247 Cisco RV320 routers and 3 410 Cisco RV325 routers).
Mursch described on a map the geographic distribution of the compromised routers, proving that most of these devices are found in the United States.
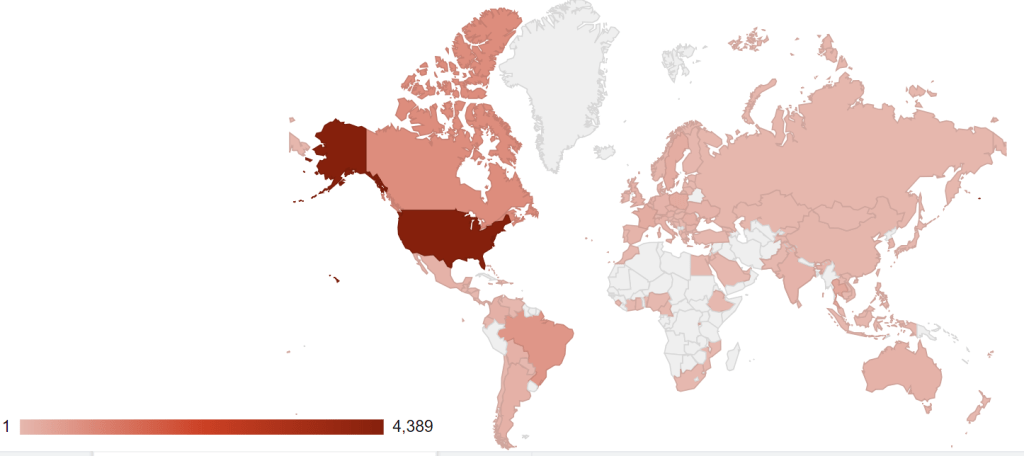
“Although the research we did will be published shortly, the IP addresses of the Cisco routers affected by these failures will not be revealed, as it is sensitive information,” said Troy Mursch on his blog.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











