We are living in digital age where everything is digital. Day by day more people are using internet. Some uses internet for business some for fun and there are tons of reasons that why I am using internet ? As online users are increasing, online privacy is also creating an issue. Many individuals like black hat hackers, spammers are stealing users information to manipulate them. Increasing frauds especially in online world has create an big concerned for officials. Normal internet users don’t know much about their rights while surfing internet. Increasing standards of cyber crimes has create an new evolution called Cyber Forensics.
Digital Forensic researcher of international institute of cyber security says cyber crimes is taking new heights day by day. Therefore we should consider learning about cyber forensics.
Cyber Crime Solution : Cyber Forensics
What are Cyber Forensic ? Cyber Forensics is a process collecting & analyzing information and presenting that information to enforcement law. Cyber forensics mainly deals with to analyze data collected from crime scene. The main goal of cyber forensics is to make a proper investigation while keeping a document that what exactly happened on a computing device.
Why Cyber Forensics is Important ? Cyber forensics creates an important role in computer science field. Law enforcement agencies uses IT/Cyber Security professionals to gain serious evidence in their investigations. Devices like hard disk, pendrives, memory cards and any other storage devices are used to collect the evidence which is used in solving cyber incidents .
Cyber Forensics Investigation Consists of :-
<-Preserving & Acquiring Data-Authenticating Data-Analyzing Data-Reporting Data->
- Cyber forensics consists of four main steps : Cyber forensics consists of four main phases :
- Preserving & Acquiring Data : The first step involves gather data from seize devices & creating a bit by bit copy of the hard drive data.
- Authenticating Data : This step involves to check whether acquired data is the exact copy of the contents of the hard drive. For checking sha1/md5 values are matched.
- Analyzing Data : This is most important phase which includes examination and analyze all the gathered data using forensic techniques /tools.
- Reporting Data : This is where all the gather information in third phase is presented to the law enforcement agencies.
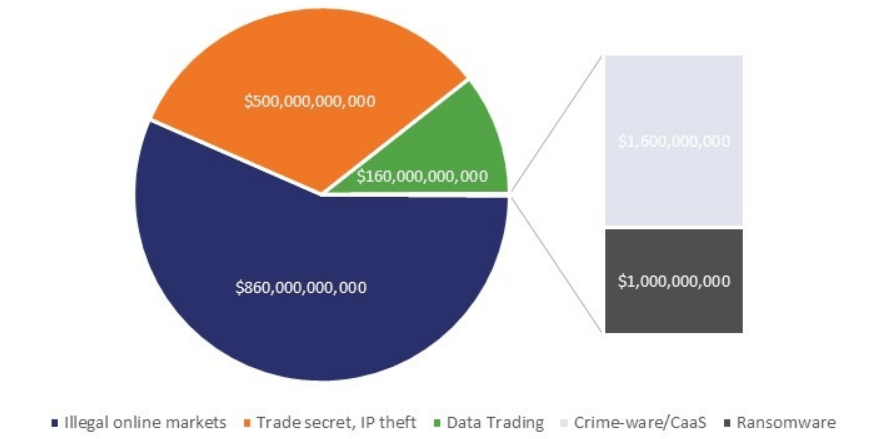
Current Cyber Crime Statistics :-
The current cyber crime statistics shows that what attacks are used in cyber crime.
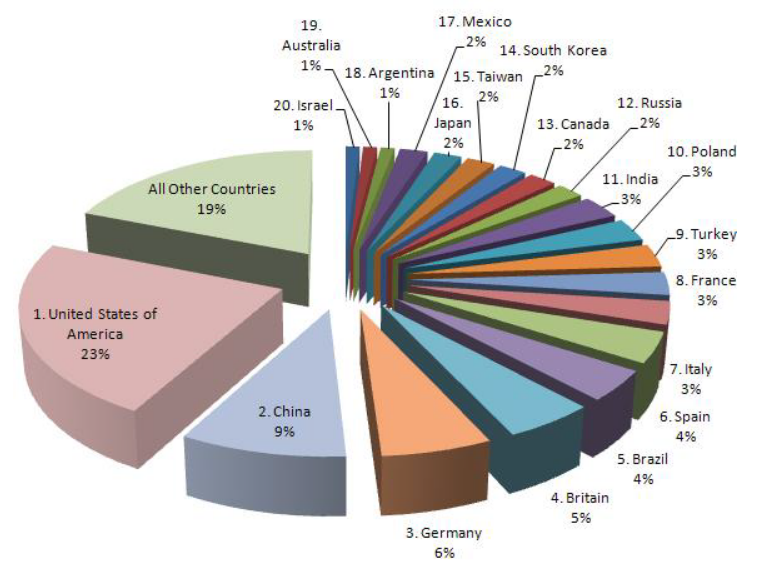
Cyber Crime in Top 20 Countries :-
Here we shows top 20 countries which are involved in cyber crime. Most of the cyber crime are evolved country like USA.
Windows Operating System & Cyber Forensics :-
Windows is the most popular operating system. Most of you are generally aware how to use this operating system. Windows is most usable because of its simplicity, more reliable, more easy to use, more fast but when comes to security. Windows operating system lacks many features in terms of security which can give access to black hat hackers /spammers to steal important information. These lack of features increases day to day increase in cyber crime. Most of the average windows users are unaware that newly upgraded windows is leaving tracks of their activity. It is very essential for windows users to know that confidential information stored in windows can be used to restore history of any particular user.
Why Windows Lacks Security :-
Windows uses most of old written code. These codes are way to old that their decryptors/ manipulators are available online easily that any script kiddie/ or anyone can use to break into windows operating system. Some of its artifacts codes are written in initial days of Microsoft and still they are not updated. Windows artifacts are the objects which holds information to the activities that are performed by the windows user. The type of information and location contains in artifact differ from one operating system to another. Windows artifacts are contains sensitive information which are analyzed very carefully at the time of forensics analysis.
Windows Registries :-
Windows registry is the most important source for analyzing any windows computer. These registries holds initial configuration for windows and all the installed applications. Registry holds windows system configuration for different windows applications. The registry not only keep configurations for the windows & other applications but also keep a track to enhance windows user experience.
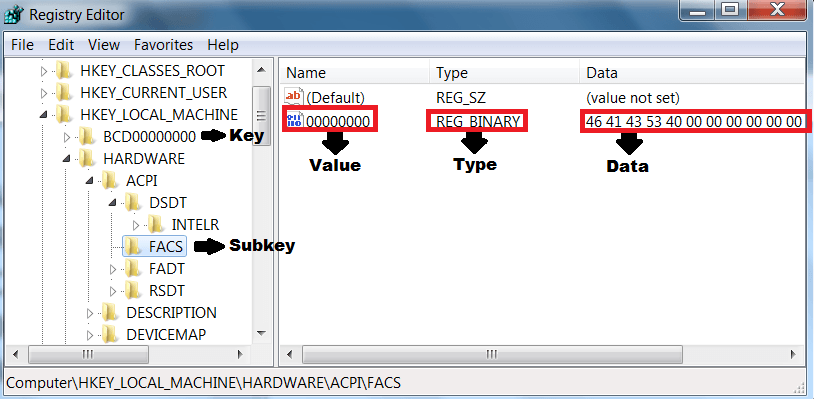
These registries are used by forensic investigators to analyze them. There are various tools which are used to analyze such registries. Some open source tools that allows investigators to analyze windows registries.
Some OF Windows Popular Artifacts :-

These windows artifacts are used to analyze windows user to recreate its account history. As these common forms of windows that are used regularly by any windows user. Windows Artifacts like :-
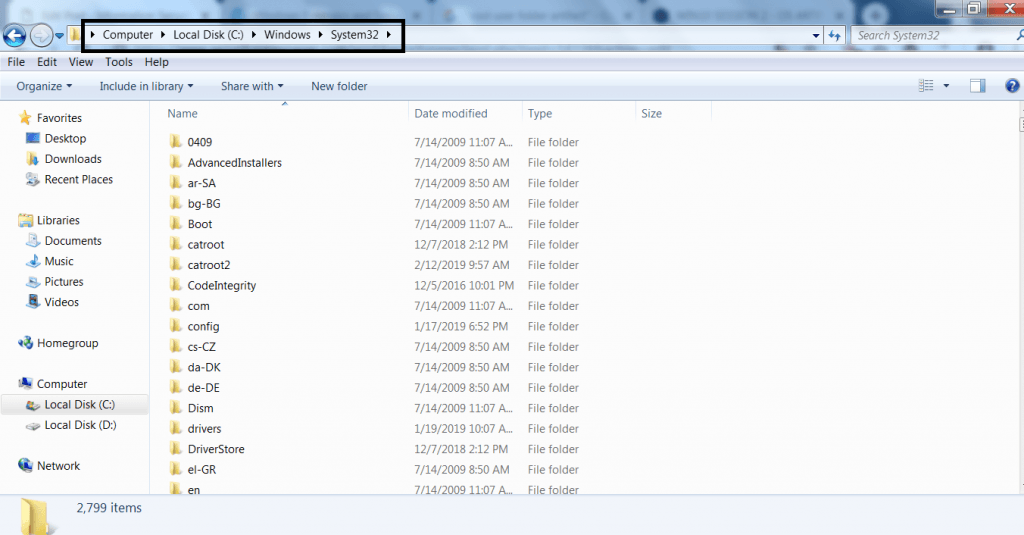
- Root User Folder Artifacts : Root User gives you the complete admin privileges. Root has right to modify, delete files in operating system. Besides root gives many rights. But these rights cannot be taken or changed for the root. For accessing root go to My computer from desktop or computer from start menu. And go to Local C:\Windows\System32
- Desktop Artifacts : All the files of a windows user are stored in desktop folder. These files are created by the user or by the programs that are installed by the user. For accessing desktop Local C:\Users\Username
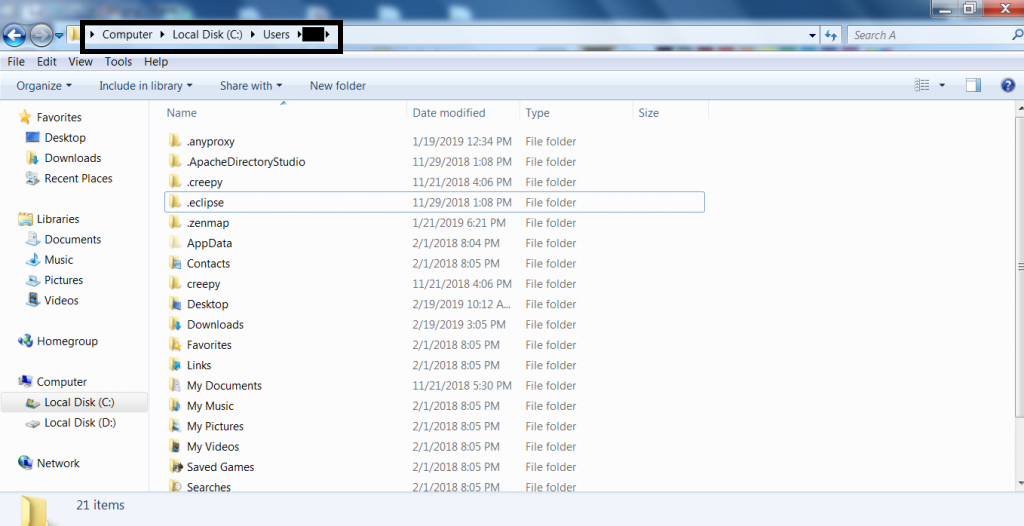
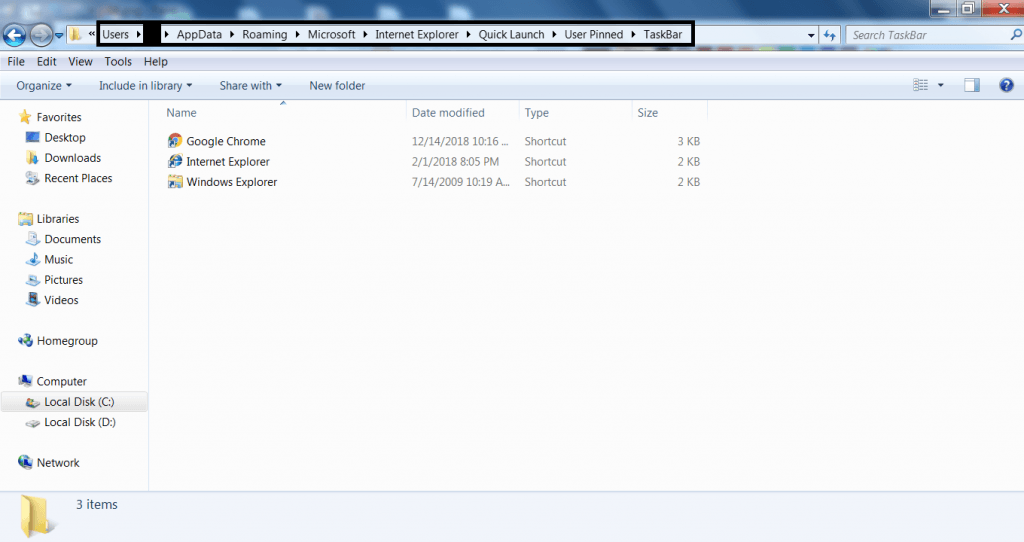
- Jump List Files/ Pinned Files : Jump list files can be accessed as these files contains record of last visited or recently opened program. The location can be accessed : Local C:\Users\username\AppData\Roaming\Microsoft\InternetExplorer\QuickLaunch\UserPinned\TaskBar
Top Open Source Windows Forensics Tools :-
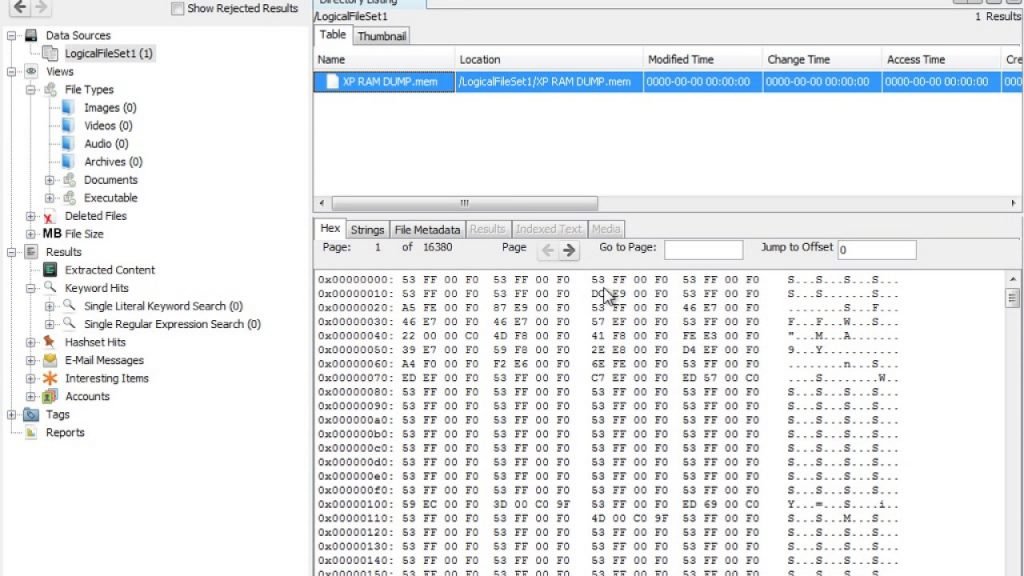
- Autopsy is an GUI based forensic tool used to analyze hard disks & smart phones. Download tool from : https://www.sleuthkit.org/autopsy/
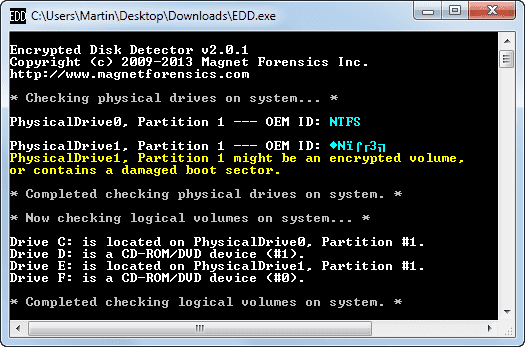
- Encrypted Disk Detector is used to check encrypted physical drives. The tool supports PGP, Bitlocker, Safeboot encrypted volumes & TrueCrypt Download tool from : https://www.magnetforensics.com/free-tool-encrypted-disk-detector/
- Wireshark is an network analyzer and capture tool used to see what traffic is going in your network. The tool comes useful in network incident. Download tool from : https://www.wireshark.org/
- Magnet RAM Capture is used to analyze physical memory of a computer. Download tool from : https://www.magnetforensics.com/free-tool-magnet-ram-capture/
- Network Miner is used in passive network sniffer/ capture to detect operating system ports, sessions. hostnames etc. Download tool from : https://www.netresec.com/?page=NetworkMiner
- NMAP is one of the most popular tool used to check open ports of the target. using this you can find vulnerability of any target to hack. Download tool from : https://nmap.org/
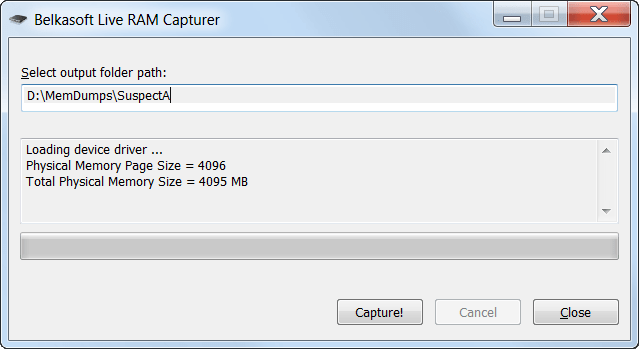
- RAM Capture is a free tool use to extract entire content of volatile memory. Download tool from : https://belkasoft.com/ram-capturer
- Forensic Investigator is an splunk toolkit used in based64 conversion, HEX conversion, virustotal, metascan lookups and many features which are used in forensics. Download tool from : https://splunkbase.splunk.com/app/2895/

- FAW (Forensics Acquistion Of Websites) is to acquire web pages images, HTML, source code of the web page and can integrate with wireshark. Download tool from : https://www.fawproject.com/

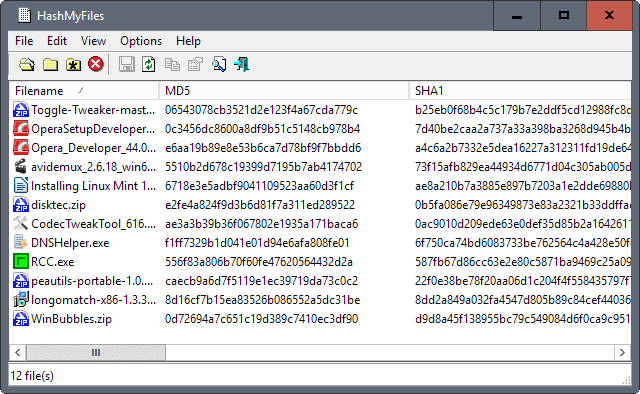
- HashMyFiles is used to calculate MD5 and SHA1 hashes. It works on all the latest websites. Download tool from : https://www.nirsoft.net/utils/hash_my_files.html
- USB Write Blocker is used to verify USB contents without leaving any fingerprint. Download tool from : https://legility.com/
- Crowd Response is used to gather system information for incident response. Download tool from : https://www.crowdstrike.com/resources/community-tools/
- NFI Defraser is used to find multimedia files in the data streams. Download tool from : https://sourceforge.net/projects/defraser/
- ExifTool tool is used to read, write and edit meta information for a number of files. Download tool from : https://www.sno.phy.queensu.ca/~phil/exiftool/
- Toolsley comprises of multiple tools like file identifier, hash & validate, binary inspector etc which helps in forensic investigations. Download tool from : https://www.toolsley.com/
- SIFT (SANS forensic toolkit) is a suite of forensic tools & very popular among forensic teams. The toolkit comprises of many tools which are used in cyber incidents. Download tool from : https://digital-forensics.sans.org/community/downloads/#overview

- DumpZilla is used to extract all data from firefox. Download tool from : https://www.dumpzilla.org/
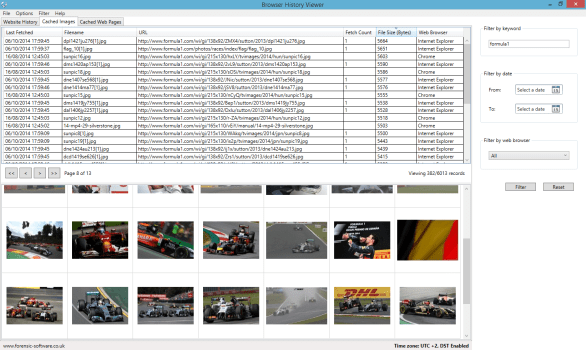
- Browser History is used to find history from browsers like firefox, chrome, IE, edge history on OS. Download tool from : https://www.nirsoft.net/utils/browsing_history_view.html

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











