Web application security specialists report the emergence of a new ransomware variant infecting devices with Android operating system. The malware, known as Android/Filecoder.C, was distributed via multiple hacking forums and it has been reported that attackers are able to access the victims’ contact list to send malicious links embedded in SMS messages.
The specialists of the security firm ESET were in charge of detecting this ransomware attacks in the wild a couple of weeks ago. In their report, the experts added: “The potential impact of this attack is limited due to some campaign execution flaws and deficient implementation of the encryption”.
According to web application security specialists, hackers distribute this malware variant in two different ways: via hacking forums and via SMS messages. Hackers have even been detected to post and share links for downloading this ransomware on forums visited by software developers, such as Reddit or XDA.
In an attempt to attract victims more easily, malicious campaign operators post QR codes related to pornographic sites or technology issues on multiple forums that, once scanned, redirect users to download sites of malicious apps like Sex Simulator. Hackers can also hide shortened URLs and post them in the comment sections of these platforms. As if that weren’t enough, when the ransomware is received via SMS, it proceeds to scan the victim’s contacts list to send the link to other users and spread the infection.
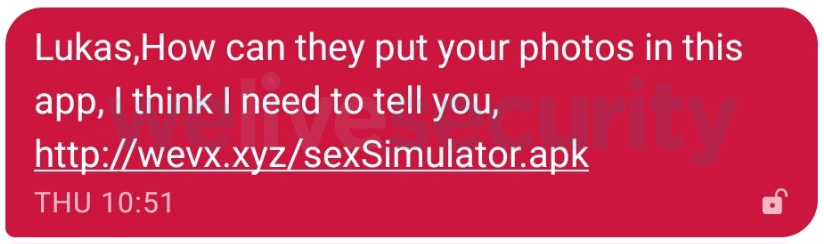
When the victims interact with the link in the SMS, the malicious file is downloaded and forces the victim to install another application that functions as a command and control server.
After the link is sent to the victim’s contacts, the encryption process begins. Despite how dangerous this campaign appears to be, web application security experts point out that the compromised files could be recovered thanks to some flaws in the ransomware encryption process; it is even possible that this ransomware will not be able to delete the encrypted information if the deadline for the victim to pay the ransom expires (about 3 days).
At the end of the encryption process the extension of the compromised files changes to .seven and the user is shown the message demanding the ransom. Experts add that, unlike other variants, this malware does not lock the screen of the device, and it does not compromise the integrity of certain files, including:
- Files with .cache, .tmp, .zip, .rar, .jpg and .png extensions
- Files that are less than 150kb or more than 50MB
The International Institute of Cyber Security (IICS) web application security experts ensure that it is possible to remove encryption without paying the ransom; for this, it is required to change the encryption algorithm to a decryption algorithm. To accomplish such task, users only need the malware user ID and the ransomware APK.
Ransomware infections on Android OS devices began to sprout a couple of years ago. The first prominent case, known as Lokibot ransomware, infected thousands of smartphone users and managed to get more than $1.5M USD worldwide.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











