About a week ago, two reports of vulnerabilities affecting the Virtual Private Network (VPN) Secure Socket Layer (SSL) systems of Fortinet appeared. According to the experts who revealed these flaws, a hacker group has begun exploiting these vulnerabilities in FortiGate and Pulse Connect Secure SSL VPNs.
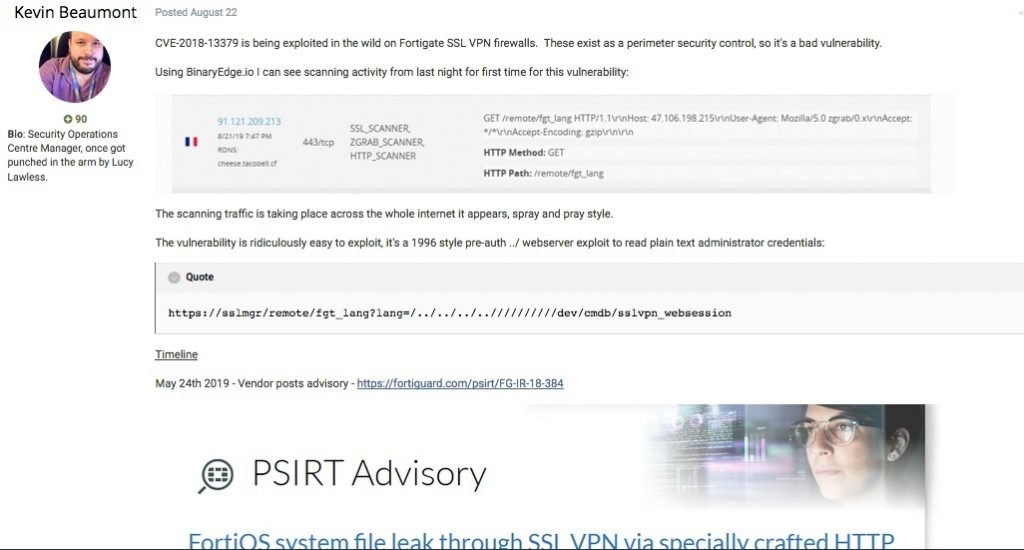
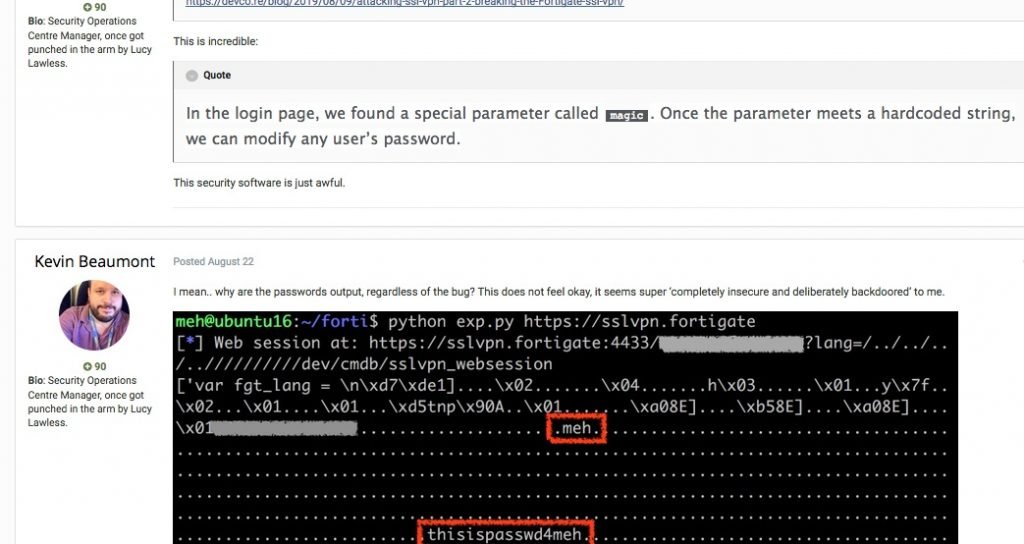
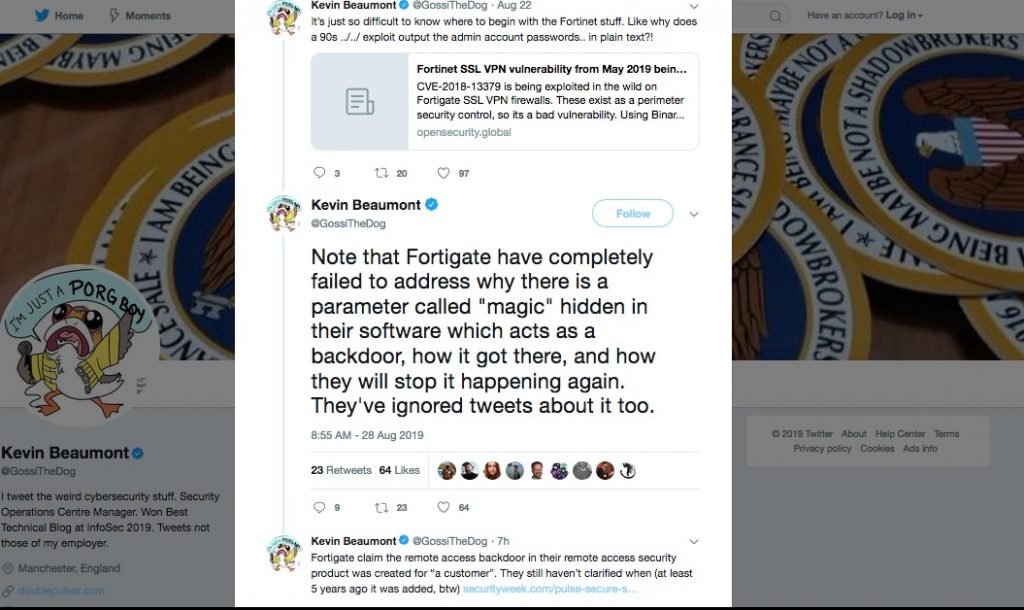
Fortinet’s engineers implemented a very bad method of authentication in operating system on its firewall. This allows an unauthenticated attacker to modify the password of SSL VPN portal. It seems it was intentionally done as it has been done very poorly. They had implemented a special parameter called “magic” which allowed the change of password. This seems like a back door which cold have been done by the company intentionally or some hackers like in the case of IMPERVA another company which said hackers were having backdoors in their systems since 2017.
There is an exploit available for exploiting this vulnerability in github. You can see the details of exploit in the screen and forums where experts are talking about this backdoor.
Vulnerabilities in FortiGate SSL VPN
Experts Orange Tsai and Meh Chang, from DEVCORE researchersteam, published the second part of their research on security flaws in SSL VPNs; the first part of the investigation focused on the CVE-2019-1579 vulnerability, a critical security flaw prior to authentication.
The research presents 5 security vulnerabilities during a vulnerability assessment, which are shown below, along with the score assigned to each by the Common Vulnerabiltiy Scoring System (CVSS):
- CVE-2018-13379: It is an arbitrary file read vulnerability with a score of 9.1/10 on the CVSS scale
- CVE-2018-13380: Cross-Site Script vulnerability (XSS) with a score of 6.1/10
- CVE-2018-13381: Pre-authentication heap overflow vulnerability with 7.5 score on CVSS
- CVE-2018-13382: It’s an inappropriate authorization flaw with a score of 7.5/10
- CVE-2018-13383: Post-authentication heap overflow vulnerability with 6.5/10 score
Apparently, hackers exploit the CVE-2018-13379 flaw, an arbitrary file read vulnerability prior to authentication in the way FortiOS requests a system language file. Experts mentioned that by exploiting this vulnerability, hackers can read the content of “sslvpn_websession”, a file containing a username and the corresponding password are formatted on the compromised system.
In their report, experts add that it is even possible to combine this flaw with CVE-2018-13383 (post-authentication heap overflow) in FortiGate WebVPN. This flaw could be triggered when the attacker instructs the SSL VPN to proxy to a web server under its control, which hosts an exploit file.
On the other hand, the CVE-2018-13382 vulnerability, dubbed by researchers as “magic backdoor”, takes advantage of a special parameter called “magic”, used by hackers as a secret key to reset a password without the need for other forms of authentication.
Hackers began searching for vulnerable endpoints on the Pulse Connect Secure VPN server after the release of a proof-of-concept for the CVE-2019-11510 arbitrary file disclosure flaw. Similar to CVE-2018-13379, this vulnerability is used by hackers to find exposed systems to recover unencrypted usernames and passwords.
If successfully authenticated, hackers can use the CVE-2019-11539 (command injection in the administrator’s web interface) vulnerability to access restricted environments.
As a precautionary measure, customers running vulnerable versions of FortiGate are encouraged to upgrade to the latest versions as soon as possible.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











