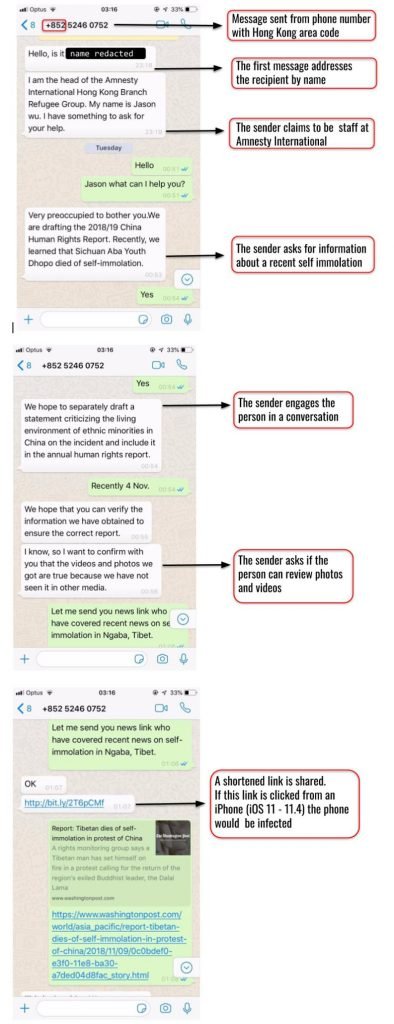
A Senior staff oficial group was contacted on Whatsapp from a unknown number. The caller claim to be Jason Mu, Head of Refugee group at Amesty International’s Hong Kong branch. He quickly introduced the self-immolation. And claimed to verify social media reports for using in upcoming Amnesty International report on human rights in China & for chinese govt. treatment on minorities..
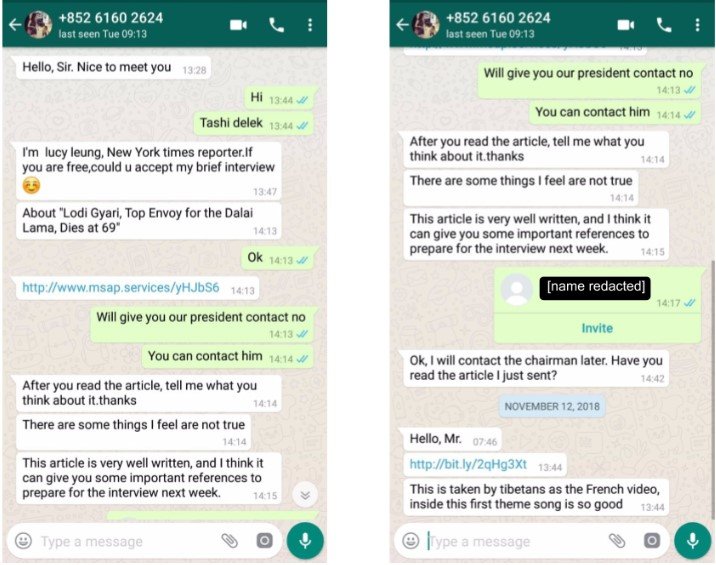
The caller Jason Wu sent links which he claimed to be related to the case on activist in Tibetan movement. Attacker claiming to be Jason Wu was not real & was having harmful thoughts. The links which were received containing exploits (malicious code which could take advantage of software vulnerabilities) for IOS. If the links were clicked on Iphone running 11.0-11.4 the Iphone will infect with spyware which could steal information from device & apps running. According to University of Toronto’s Citizen Lab reports that campaign is first documented case of One-Click Mobile Exploits against Tibetans.
Spyware tries to infect high profile Tibetan community including members of The Private office of his Holliness the Dalai Lama, The Central Tibetan Administration, The Tibetan Parliament & Tibetan human rights groups. Attacker also targets Android users & tries to use QAuth Application to gain access to Gmail Accounts. Over the course of campaign. Citizens has collected One IOS exploit & Eight Android exploits. 12 Attempts were send to the IOS users with links. According to reports 15 attempt were made to infect mobile phones between NOV 11-14.
ANDROID IOS Exploits 1 8 Targets 12 3
As per ethical hacking researcher of international institute of cyber security the targets were receiving malicious links in individually in WhatsApp from seven unknown numbers claiming as journalists. From staff at International advocacy organisations to Tibetan human rights groups & tourist to India. Attacker were actively engaging in conversation & persistently attempted to infect their targets. Attackers were using Hong Kong country code (+852) linked with URL shortners such as bit.ly to hide actual link.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.