Network pentesting which helps pentesters/ network administrators to finds vulnerability in a particular system. Network pentesting is done to secure the network. It helps to test local network and helps to find network vulnerabilities. According to ethical hacking researcher of international institute of cyber security, if the attacker enters any one system of local network of any organization, attacker can use further methods to penetrate the Local Network.
Network Pentesting Methodology
As explained above network pentesting should be done consistently to secure corporate networks. Below you can see network pentesting methodology.
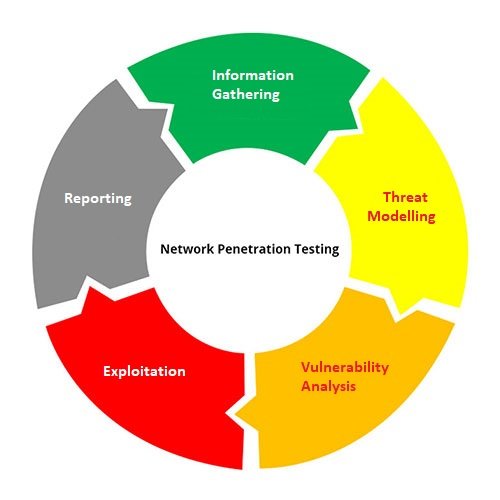
- Information Gathering – This phase consists of service enumeration. Here open ports & services are scanned. Mostly ports are scanned to find any vulnerabilities. In scanning phase discovered hosts are prime source for finding un-patched security. Most companies uses wifi based printers which are most common threats for attacking. In this phase pentesters tries to find as much information as possible. This is the most important phase where collected information is used to find vulnerabilities. Netass2 is helpful finding open ports & services, also help in discovered hosts.
- Threat Modeling – Here automate scanners are used. In this phase collected information from above phase is used. Threat Modeling identify assets & divide into threat categories. These might consists of password hashes, un-patched security updates, using outdated firewall policies which helps attacker to enter into network using MITM methods.
- Vulnerability Analysis – This phase involves analysis of founded vulnerabilities. This phase includes of various security tools & manual testing. In this phase many vulnerabilities has to analyzed. Plan of attacking is designed here.
- Exploitation – This phase involves actual attacking on founded vulnerabilities. Exploitation includes intense attacking on the vulnerabilities.
- Reporting – This phase reports all the founded vulnerabilities with a proper reporting format. This phase needs to be written & verified properly. As it includes all the details of vulnerabilities & shows the value of our services.
Netass2 (Network Assessment Assistance Framework) is used to scan local network in Information gathering phase. Netass2 uses nmap & zenmap modules for scanning given hosts.
- For testing we will use Kali Linux 2018.2 amd64. Open terminal type git clone https://github.com/zerobyte-id/NetAss2.git
- Type cd NetAss2
- Type ls
- Type chmod 755 install.bash netass2.bash
- Type ./netass2.bash
root@kali:/home/iicybersecurity/Downloads/NetAss2# ./netass2.bash
------------------------------------------
| NAME : Network Assessment Assistance |
| ALIAS : NetAss2 |
| TYPE : VA Framework |
| VERS : 0.1-RC |
| LICEN : GPL v3 |
| LINK : github.com/zerobyte-id/NetAss2 |
------------------------------------------- Enter project name – project02
Enter a project name: project02
--------------------------------------------------
__ _ _ ____
/\ \ \___| |_ / \ ___ ___|___ \
/ \/ / _ \ __|/ O \/ __/ __| __) |
/ /\ / __/ |_/ _ \__ \__ \/ __/
\_\ \/ \___|\__\_/ \_/___/___/_____\
Network Assessment Assistance
[1]. HOST DISCOVERY
[2]. PORT SCAN ON SINGLE HOST
[3]. MASSIVE PORT SCAN VIA DISCOVERED HOSTS
[4]. MASSIVE PORT SCAN VIA LIST ON FILE
[5]. SINGLE PORT QUICK SCAN VIA NETWORK BLOCK
[6]. MULTIPLE PORT QUICK SCAN VIA NETWORK BLOCK
[!]. SHOW REPORTS
[0]. EXITINPUT: 1 ----------------[ HOST DISCOVERY ]---------------- NOTE: Your network block reminder 192.168.1.102/24 NOTE: Enter the network block that you want to scan NOTE: Example: 192.168.1.0/24
- Enter network subnet. For finding network subnet, run ipconfig and check the IP Address and Subnet Mask in the output. After getting the network subnet enter it as shown below.
- Type 192.168.1.1/24
--------------------------------------------------
__ _ _ ____
/\ \ \___| |_ / \ ___ ___|___ \
/ \/ / _ \ __|/ O \/ __/ __| __) |
/ /\ / __/ |_/ _ \__ \__ \/ __/
\_\ \/ \___|\__\_/ \_/___/___/_____\
Network Assessment Assistance
[1]. HOST DISCOVERY
[2]. PORT SCAN ON SINGLE HOST
[3]. MASSIVE PORT SCAN VIA DISCOVERED HOSTS
[4]. MASSIVE PORT SCAN VIA LIST ON FILE
[5]. SINGLE PORT QUICK SCAN VIA NETWORK BLOCK
[6]. MULTIPLE PORT QUICK SCAN VIA NETWORK BLOCK
[!]. SHOW REPORTS
[0]. EXIT
INPUT: 1
----------------[ HOST DISCOVERY ]----------------
NOTE: Your network block reminder
+ 192.168.1.102/24
NOTE: Enter the network block that you want to scan
NOTE: Example: 192.168.1.0/24INPUT: 192.168.1.1/24
INFO: Nmap run...
INFO: Discovering host...
Host
------------
192.168.1.1
192.168.1.12
192.168.1.102
192.168.1.103
--------------------------------------------------- Above shows the available hosts on network. For finding open ports. Type 2
--------------------------------------------------
__ _ _ ____
/\ \ \___| |_ / \ ___ ___|___ \
/ \/ / _ \ __|/ O \/ __/ __| __) |
/ /\ / __/ |_/ _ \__ \__ \/ __/
\_\ \/ \___|\__\_/ \_/___/___/_____\
Network Assessment Assistance
[1]. HOST DISCOVERY
[2]. PORT SCAN ON SINGLE HOST
[3]. MASSIVE PORT SCAN VIA DISCOVERED HOSTS
[4]. MASSIVE PORT SCAN VIA LIST ON FILE
[5]. SINGLE PORT QUICK SCAN VIA NETWORK BLOCK
[6]. MULTIPLE PORT QUICK SCAN VIA NETWORK BLOCK
[!]. SHOW REPORTS
[0]. EXIT
INPUT: 2 -----------[ PORT SCAN ON SINGLE HOST ]----------- INFO: Discovered host 192.168.1.1 192.168.1.12 192.168.1.102 192.168.1.103 NOTE: Enter the specific host that you want to scan NOTE: Example: 192.168.1.100 INPUT: 192.168.1.103 INFO: Nmap run… INFO: Discovering port on 192.168.1.103… IP Addr Port Service Vendor ------- ---- ------- ------ 192.168.1.103 135/tcp msrpc Microsoft Windows RPC 192.168.1.103 139/tcp netbios-ssn Microsoft Windows netbios-ssn 192.168.1.103 445/tcp microsoft-ds? 192.168.1.103 902/tcp ssl/vmware-auth VMware Authentication Daemon 1.10 (Uses VNC, SOAP) 192.168.1.103 912/tcp vmware-auth VMware Authentication Daemon 1.0 (Uses VNC, SOAP) 192.168.1.103 1536/tcp msrpc Microsoft Windows RPC 192.168.1.103 1537/tcp msrpc Microsoft Windows RPC 192.168.1.103 1538/tcp msrpc Microsoft Windows RPC 192.168.1.103 1539/tcp msrpc Microsoft Windows RPC 192.168.1.103 1540/tcp msrpc Microsoft Windows RPC 192.168.1.103 1541/tcp msrpc Microsoft Windows RPC 192.168.1.103 1545/tcp msrpc Microsoft Windows RPC 192.168.1.103 1569/tcp msrpc Microsoft Windows RPC 192.168.1.103 3389/tcp ms-wbt-server Microsoft Terminal Services
- Above output shows open ports which shows target can be vulnerable to different windows vulnerabilities. Netass2 is used in network pentesting.
- Type 3
--------------------------------------------------
__ _ _ ____
/\ \ \___| |_ / \ ___ ___|___ \
/ \/ / _ \ __|/ O \/ __/ __| __) |
/ /\ / __/ |_/ _ \__ \__ \/ __/
\_\ \/ \___|\__\_/ \_/___/___/_____\
Network Assessment Assistance
[1]. HOST DISCOVERY
[2]. PORT SCAN ON SINGLE HOST
[3]. MASSIVE PORT SCAN VIA DISCOVERED HOSTS
[4]. MASSIVE PORT SCAN VIA LIST ON FILE
[5]. SINGLE PORT QUICK SCAN VIA NETWORK BLOCK
[6]. MULTIPLE PORT QUICK SCAN VIA NETWORK BLOCK
[!]. SHOW REPORTS
[0]. EXITINPUT: 3
----[ MASSIVE PORT SCAN VIA DISCOVERED HOSTS ]----
INFO: Nmap run...
INFO: Discovering port on 192.168.1.1...
INFO: Nmap run...
INFO: Discovering port on 192.168.1.12...
INFO: Nmap run...
INFO: Discovering port on 192.168.1.102...
INFO: Nmap run...
INFO: Discovering port on 192.168.1.103...
IP Addr Port Service Vendor
------- ---- ------- ------
192.168.1.1 21/tcp ftp Netgear broadband router or ZyXel VoIP adapter ftpd 1.0
192.168.1.1 23/tcp telnet Netgear broadband router or ZyXel VoIP adapter telnetd
192.168.1.1 80/tcp upnp
192.168.1.1 7547/tcp upnp
192.168.1.12 135/tcp msrpc Microsoft Windows RPC
192.168.1.12 139/tcp netbios-ssn Microsoft Windows netbios-ssn
192.168.1.12 445/tcp microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
192.168.1.12 554/tcp rtsp?
192.168.1.12 2869/tcp http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
192.168.1.12 3389/tcp ms-wbt-server Microsoft Terminal Service
192.168.1.12 3389/tcp ms-wbt-server?
192.168.1.12 5357/tcp http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
192.168.1.12 10243/tcp http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
192.168.1.12 49152/tcp msrpc Microsoft Windows RPC
192.168.1.12 49153/tcp msrpc Microsoft Windows RPC
192.168.1.12 49154/tcp msrpc Microsoft Windows RPC
192.168.1.12 49155/tcp msrpc Microsoft Windows RPC
192.168.1.12 49156/tcp msrpc Microsoft Windows RPC
192.168.1.12 49157/tcp msrpc Microsoft Windows RPC
192.168.1.102 22/tcp ssh OpenSSH 7.6p1 Debian 4 (protocol 2.0)
192.168.1.103 135/tcp msrpc Microsoft Windows RPC
192.168.1.103 139/tcp netbios-ssn Microsoft Windows netbios-ssn
192.168.1.103 445/tcp microsoft-ds?
192.168.1.103 902/tcp ssl/vmware-auth VMware Authentication Daemon 1.10 (Uses VNC, SOAP)
192.168.1.103 912/tcp vmware-auth VMware Authentication Daemon 1.0 (Uses VNC, SOAP)
192.168.1.103 1536/tcp msrpc Microsoft Windows RPC
192.168.1.103 1537/tcp msrpc Microsoft Windows RPC
192.168.1.103 1538/tcp msrpc Microsoft Windows RPC
192.168.1.103 1539/tcp msrpc Microsoft Windows RPC
192.168.1.103 1540/tcp msrpc Microsoft Windows RPC
192.168.1.103 1541/tcp msrpc Microsoft Windows RPC
192.168.1.103 1545/tcp msrpc Microsoft Windows RPC
192.168.1.103 1569/tcp msrpc Microsoft Windows RPC
192.168.1.103 3389/tcp ms-wbt-server Microsoft Terminal Services
--------------------------------------------------- Above output shows open ports of all discovered hosts on local network. Network pentesting shows open ports & services which then can be used in another phases attacking.
Others Types of Network Level Attacks
Some network level attacks which occur in last year. There are many network level attacks. Day to day such cases of network attacks are coming. Such companies loss lot of money because of cyber attacks as commented by Ethical hacking expert of International Institute of Cyber Security.
- Browser Attacks – These types of network attacks are the most common. As explained above attacker tries to find vulnerabilities of running host on local network. They tries to breach the security through browser, most common utility is used to access internet.
- Brute Force Attacks – Such attacks uses larger size of keywords or dictionary is created by gathering information about the target. Installing malware sometimes takes time to attack an machine because in this attack. Victim has to click on the malware.
- DOS (Denial of Service Attacks) – Multiple packets are send to particular port to interrupt the ongoing service of running server or website. DOS attacks are very common & not many companies are able to recover their resources.
- Malware Attacks – Such attacks uses a piece of malware in the form of windows executable or other OS software, to create an reverse session of victim computer. Malware attacks are very serious as it gives all permission to attack for accessing victim computer.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











