Windows is the most common operating system. There are many organizations who prefer windows OS. Windows is also most targeted operating system by hackers, as per ethical hacking researcher of international institute of cyber security. We will show a method through which you can check all the details or view an history of windows operating system. We will use Dfirtriage (Digital Forensic Acquisition Tool) for windows based incident response.
Dfirtriage is designed to give incident response to victim operating system. The tool comprises of small bunch of tools which is written in python. Depending on the usage, investigator can run each tool or can run single command which will execute all small tools automatically.
- For testing we will use Windows 10 (1809) 64 Bit. Download from : https://github.com/travisfoley/dfirtriage
- Unzip dfirtriage.zip
- or drop dfirtriage.exe on the target and execute with admin rights. This step is also explained as you will scroll down.
- Below you can see different list of tools. Dfirtriage will work only in Windows OS. This tool needs to run in compromised Windows OS.
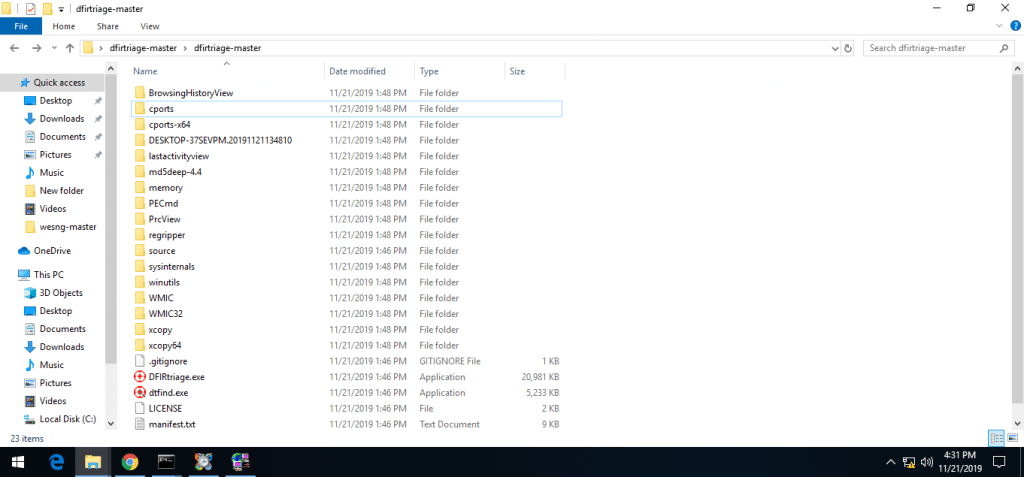
- Above list of tools which are used while investigating target windows operating system.
- Starting with web browser history. The first executable shows the all installed browsers history. Open BrowserHistoryView folder & open browserhistoryview.exe as admin.
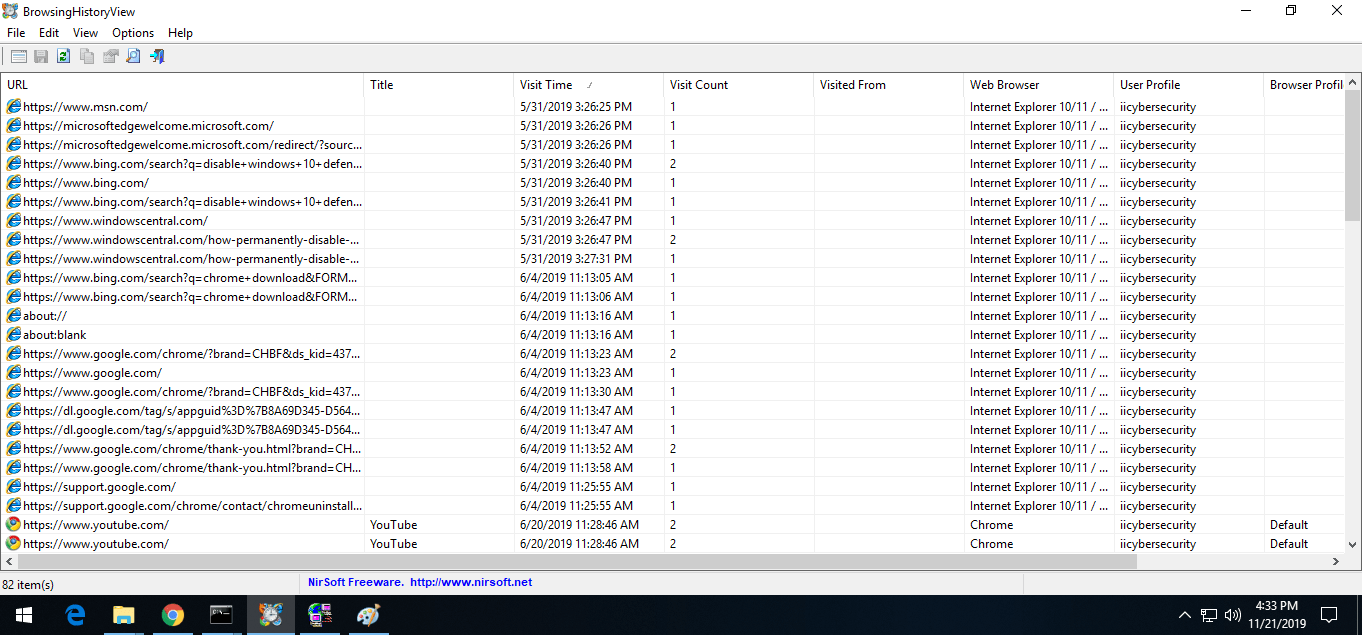
- Above shows the Opened webpages in Internet Explorer & chrome history. It shows all the webpages which are opened in web browser. If the history is deleted it will still show all recent history of web pages.
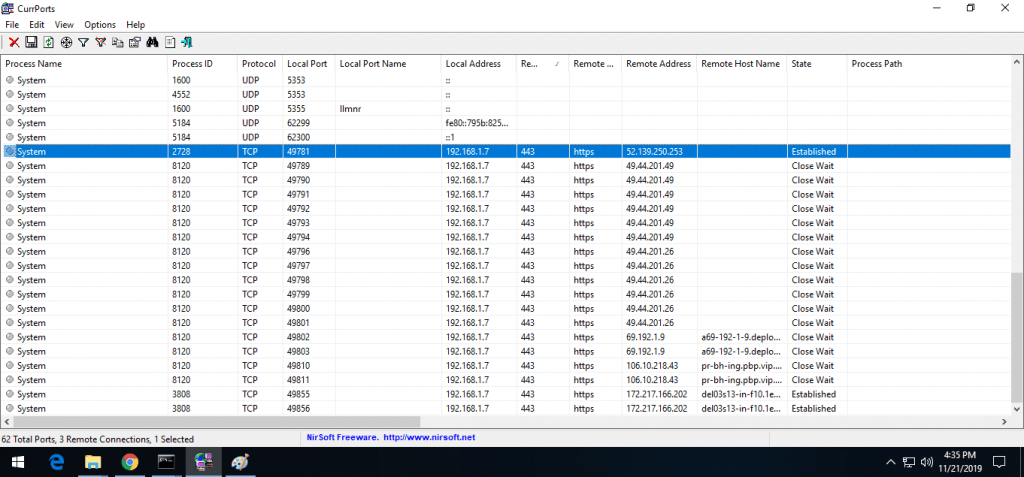
- Another helps to find which IP address are connected with the remote system. Below you can see all the connected IP addresses with their respective protocols.
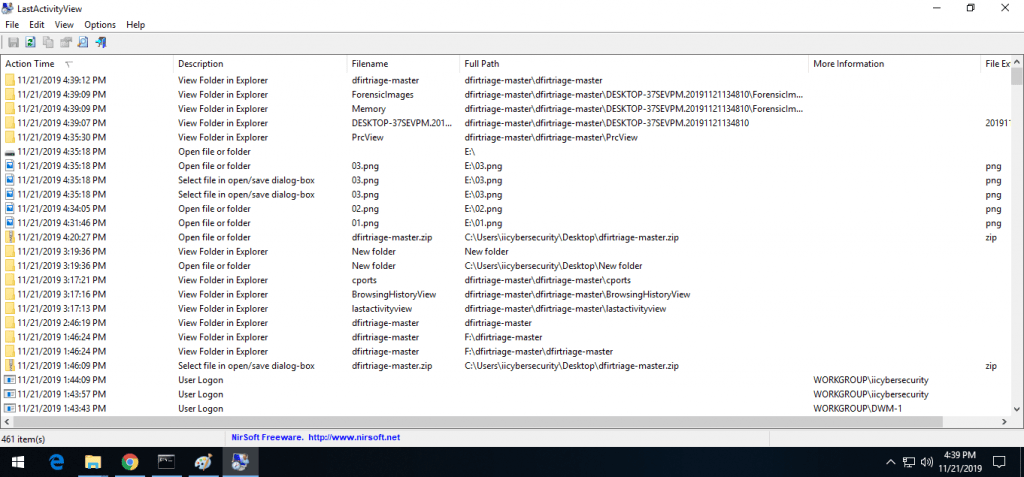
- LastActivityView helps to find all the files which lastly opened with their location. It also shows the which users are associated with files or folders.
- Sysinternals shows the auto run programs or softwares in Windows OS. You will all the programs which are set autostart. autorunsc.exe also includes the windows internal programs which are most often hidden in startup of task manager.
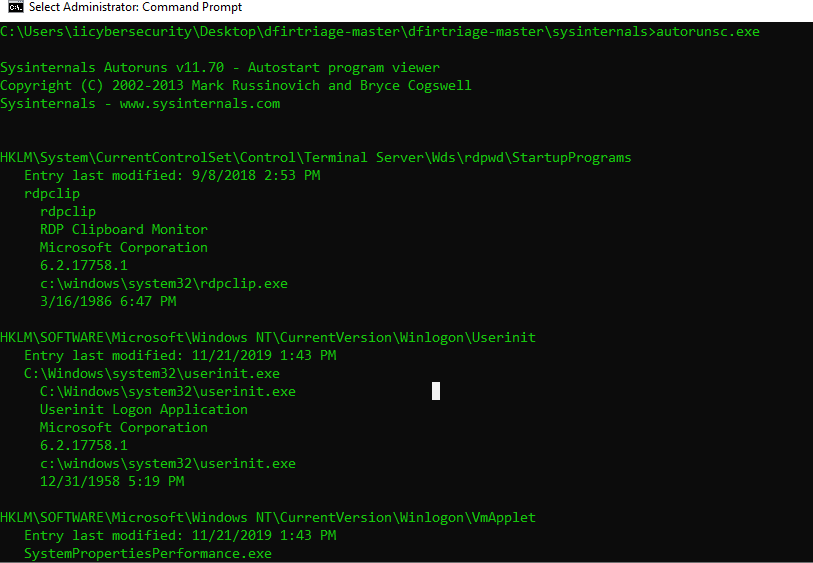
- pslist shows the running programs. pslist shows all the hidden programs with CPU time & its elapsed time. It works just like task manager but only difference it shows hidden ongoing programs which are not visible in task manager.
- There are many malware which are designed to work in background without showing in task manager.
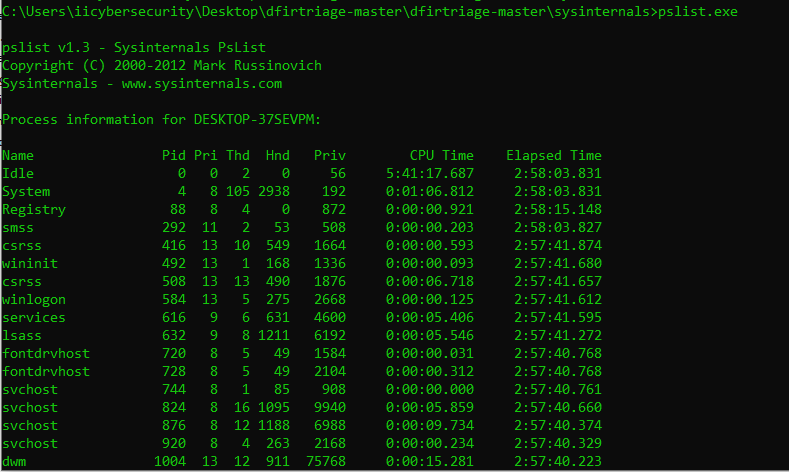
- PsLoggedon.exe shows the logged users on Windows OS. If different users are logged in. It will show all the user.
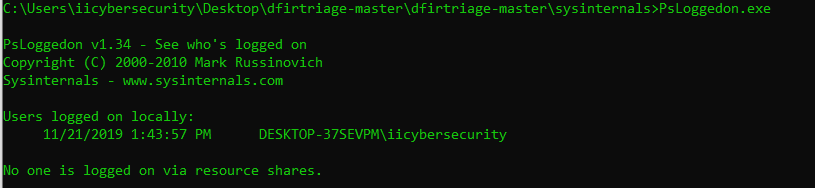
- psfile.exe shows the remote users which are connected to Windows OS. Currently it shows no other sessions is establish.
- PsInfo.exe shows hardware details on which Windows OS is running. Below it shows Windows uptime, kernel version, with its product type.
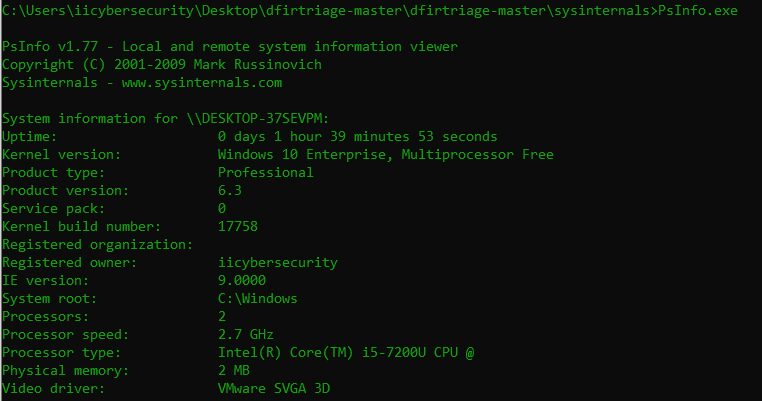
- It also shows the kernel version with registered name. PsInfo.exe also shows the processor speed & company of the processor.
- psloglist.exe shows system logs which are found in computer management. psloglist.exe shows the all events which are running in Windows.
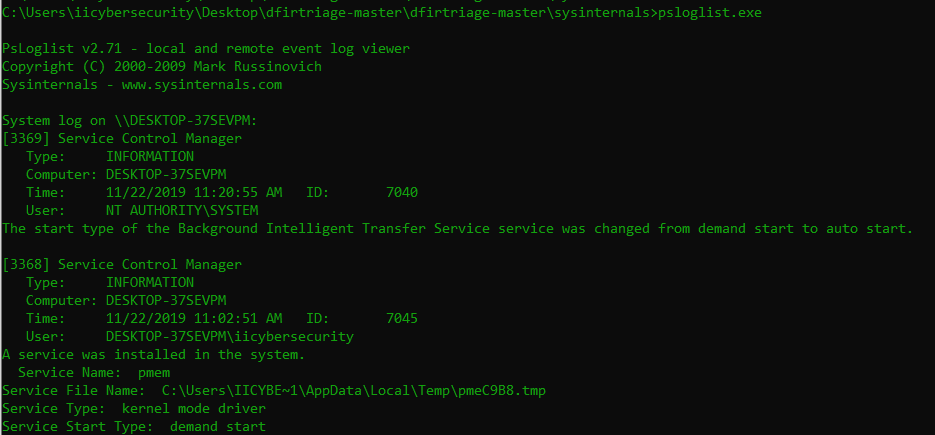
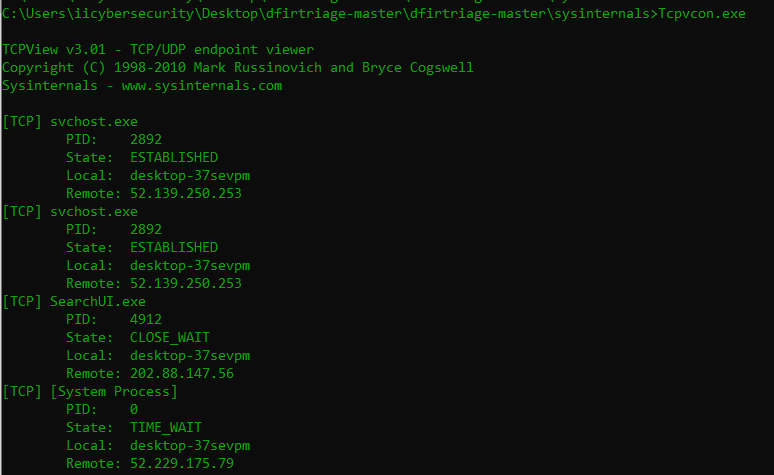
- Tcpvcon.exe shows the connected IP address with their network protocols and process name. Below shows the remote connected IP addresses with respective process name.
- Whoami.exe a very basic utility shows the user name with hostname.
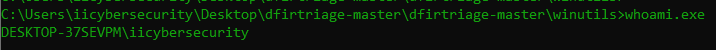
- Above we have shown the Forensics utilities & tools which are part of dfirtriage. All these tools are also part of Digital Forensics course offered by International Institute of Cyber Security.
- You can also use Dfirtriage directly at once. But it takes time to create an output.
- Earlier we have started dfirtriage.exe for getting complete output. It will save all output in text file.
- For starting dfirtriage. Open CMD as administrator. Go to location & type dfirtriage.exe
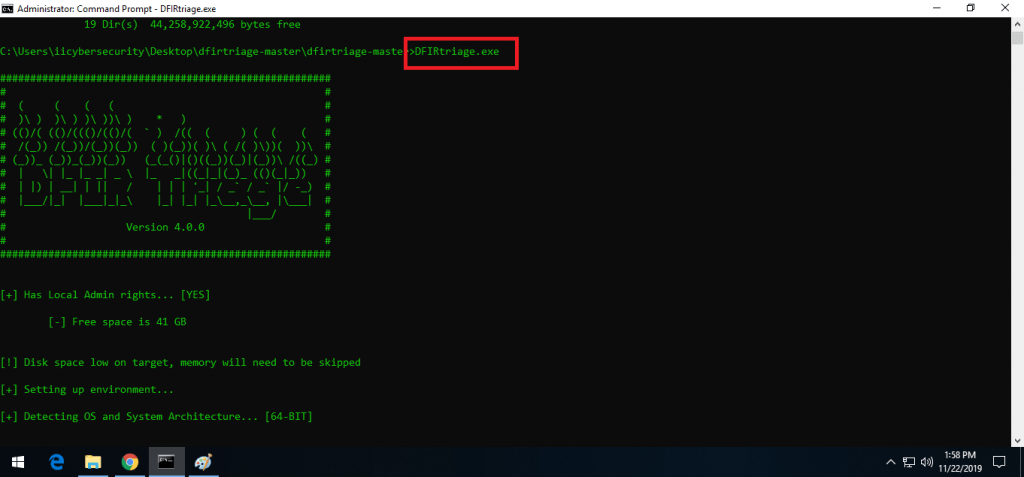
- Below shows dfirtriage has started forensic report using all the utilities & tools. You can also use all utilities or tools separately which are explained above.
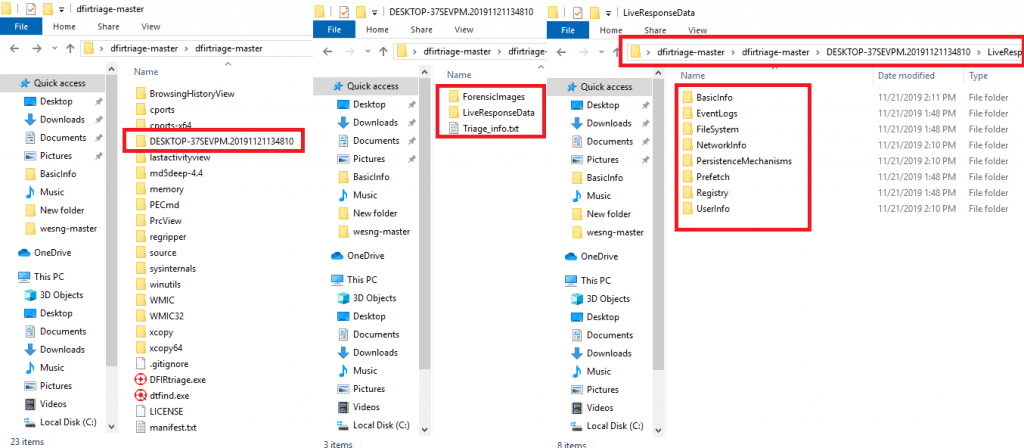
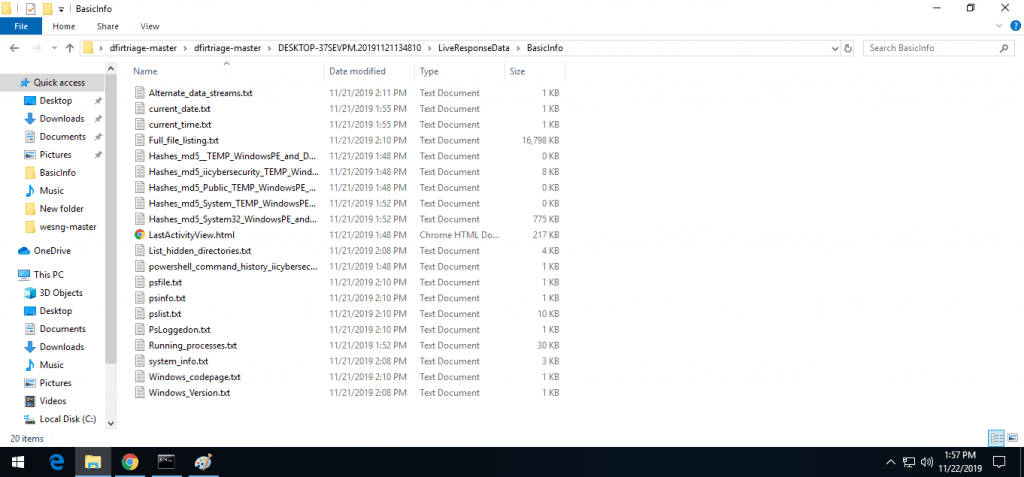
- Some reports which are generated by dfirtriage. All the output are same but are saved in text form.
- Dfirtriage can be used in threat response. Thus helpful in creating various windows forensic report related to memory or web browser history.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











