Vulnerability testing specialists have revealed the discovery of a new vulnerability in Apache Tomcat. When using Authentication with Apache Tomcat, between versions 9.0.0.M1 to 9.0.29, 8.5.0 to 8.5.49 and 7.0.0 to 7.0.98, a narrow window is presented where a threat actor could deploy a session fix attack.
At first the researchers considered this window too narrow to function as an exploit in practice, however, it was decided to report this scenario as a security flaw, tracked as CVE-2019-17563.
In the vulnerability testing expert report, the conjunction of various circumstances allows a race condition to be presented in Tomcat, allowing for session fixing and potentially allowing hackers to perform a local attack to access a user’s session with administrator privileges.
For more details, security firm support five experts have prepared a chart where administrators can see if their products or versions have already been evaluated for this flaw. To determine whether your version is vulnerable, in addition to whether components are affected by the vulnerability, and to learn about the versions, point versions, or patches that address the vulnerability, see the following table:
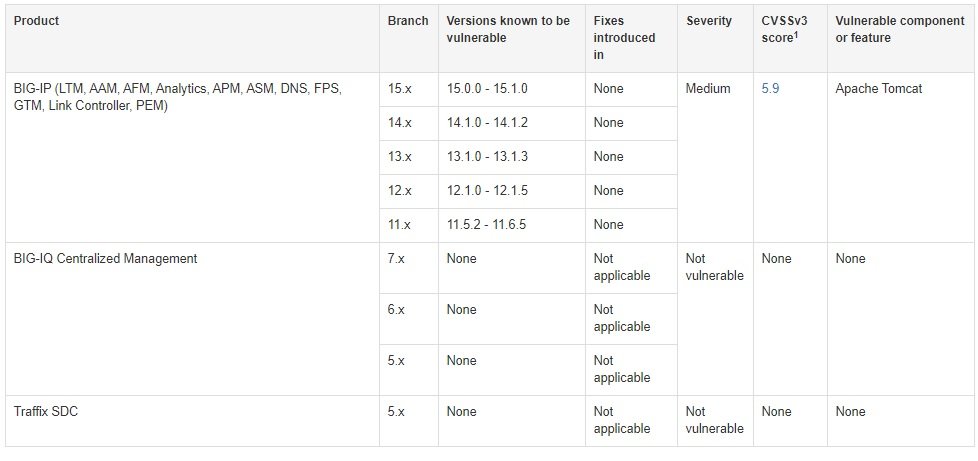
In the event that you run an affected version, vulnerability testing specialists at the International Institute of Cyber Security (IICS) recommend correcting the failure by upgrading to one of the versions that have the solutions. If the table shows only a version earlier than the one you are currently running, or a vulnerable version is not mentioned, there is no update at this time.
For more information about recently found security flaws, exploits, cyberattacks and malware analysis, you can visit the official website of the International Institute of Cyber Security (IICS), besides the official communication platforms of tech companies currently dealing with information security incidents.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











