While doing penetration testing there are many ways to gather information. There are many tools which are used in scanning, reconnaissance for knowing the loophole. Tools of Kali Linux which are used to gather information are used mostly to know IP address, MAC address of the target. Some tools do help in gathering the location of the target with the help of latitude & longitude of the person. But today we are talking about exiftool which is used to extract information from an image. Today all of us use smartphones and we all click photos using our smartphone camera. This camera do capture lot of information than photo as commented by ethical hacking researcher of International Institute of cyber Security. Exiftool is tool designed in perl to extract information from the image.
Exiftool :-
Exiftool is an open source tool used to extract data from audio, images & video. The whole tool is written in perl. Exiftool is developed platform independent runs on Windows, Mac, Linux. Exiftool comes in both interfaces Command-line & Graphical interface. The tool is mainly popular to extract GPS coordinates of the image.
- Exiftool is tested on Kali Linux 2018.4.
- Open terminal type wget https://sno.phy.queensu.ca/~phil/exiftool/Image-ExifTool-11.29.tar.gz
root@kali:/home/iicybersecurity/Downloads# wget https://sno.phy.queensu.ca/~phil/exiftool/Image-ExifTool-11.29.tar.gz
--2019-03-05 23:47:25-- https://sno.phy.queensu.ca/~phil/exiftool/Image-ExifTool-11.29.tar.gz
Resolving sno.phy.queensu.ca (sno.phy.queensu.ca)… 130.15.24.27
Connecting to sno.phy.queensu.ca (sno.phy.queensu.ca)|130.15.24.27|:443… connected.
HTTP request sent, awaiting response… 200 OK
Length: 4503877 (4.3M) [application/x-gzip]
Saving to: ‘Image-ExifTool-11.29.tar.gz’
Image-ExifTool-11.29.tar.gz 100%[===========================================================>] 4.29M 53.1KB/s in 2m 4s
2019-03-05 23:49:31 (35.4 KB/s) - ‘Image-ExifTool-11.29.tar.gz’ saved [4503877/4503877]
- Type ls
- Now type tar -xvzf Image-ExifTool-11.29.tar.gz
root@kali:/home/iicybersecurity/Downloads# ls
Image-ExifTool-11.29.tar.gz
root@kali:/home/iicybersecurity/Downloads# tar -xvzf Image-ExifTool-11.29.tar.gz
Image-ExifTool-11.29/
Image-ExifTool-11.29/arg_files/
Image-ExifTool-11.29/Changes
Image-ExifTool-11.29/config_files/
Image-ExifTool-11.29/exiftool
Image-ExifTool-11.29/fmt_files/
Image-ExifTool-11.29/html/
Image-ExifTool-11.29/lib/
Image-ExifTool-11.29/Makefile.PL
Image-ExifTool-11.29/MANIFEST
Image-ExifTool-11.29/META.json
Image-ExifTool-11.29/META.yml
Image-ExifTool-11.29/perl-Image-ExifTool.spec
Image-ExifTool-11.29/README
Image-ExifTool-11.29/t/
Image-ExifTool-11.29/t/AFCP.t
Image-ExifTool-11.29/t/AFCP_2.out
Image-ExifTool-11.29/t/AFCP_3.out
Image-ExifTool-11.29/t/AIFF.t
Image-ExifTool-11.29/t/AIFF_2.out
Image-ExifTool-11.29/t/APE.t
Image-ExifTool-11.29/t/APE_2.out
Image-ExifTool-11.29/t/APE_3.out
Image-ExifTool-11.29/t/Apple.t
Image-ExifTool-11.29/t/Apple_2.out
Image-ExifTool-11.29/t/ASF.t
Image-ExifTool-11.29/t/ASF_2.out
- Type ls
- Type chmod u+x Makefile.PL
root@kali:/home/iicybersecurity/Downloads/Image-ExifTool-11.29# ls
arg_files Changes exiftool html Makefile MANIFEST META.yml MYMETA.yml pm_to_blib t
blib config_files fmt_files lib Makefile.PL META.json MYMETA.json perl-Image-ExifTool.spec README
root@kali:/home/iicybersecurity/Downloads/Image-ExifTool-11.29# chmod u+x Makefile.PL
- Type perl Makefile.PL
root@kali:/home/iicybersecurity/Downloads/Image-ExifTool-11.29# perl Makefile.PL
Checking if your kit is complete…
Looks good
Generating a Unix-style Makefile
Writing Makefile for Image::ExifTool
Writing MYMETA.yml and MYMETA.json
- Type make test
root@kali:/home/iicybersecurity/Downloads/Image-ExifTool-11.29# make test
cp lib/File/RandomAccess.pm blib/lib/File/RandomAccess.pm
cp lib/File/RandomAccess.pod blib/lib/File/RandomAccess.pod
cp lib/Image/ExifTool/AFCP.pm blib/lib/Image/ExifTool/AFCP.pm
cp lib/Image/ExifTool/Charset/Hebrew.pm blib/lib/Image/ExifTool/Charset/Hebrew.pm
cp lib/Image/ExifTool.pod blib/lib/Image/ExifTool.pod
cp lib/Image/ExifTool/Charset/DOSLatinUS.pm blib/lib/Image/ExifTool/Charset/DOSLatinUS.pm
cp lib/Image/ExifTool/BMP.pm blib/lib/Image/ExifTool/BMP.pm
cp lib/Image/ExifTool/Charset.pm blib/lib/Image/ExifTool/Charset.pm
cp lib/Image/ExifTool/Audible.pm blib/lib/Image/ExifTool/Audible.pm
cp lib/Image/ExifTool/Charset/Latin.pm blib/lib/Image/ExifTool/Charset/Latin.pm
cp lib/Image/ExifTool/Charset/MacChineseCN.pm blib/lib/Image/ExifTool/Charset/MacChineseCN.pm
cp lib/Image/ExifTool/BPG.pm blib/lib/Image/ExifTool/BPG.pm
cp lib/Image/ExifTool/Charset/MacArabic.pm blib/lib/Image/ExifTool/Charset/MacArabic.pm
cp lib/Image/ExifTool/BuildTagLookup.pm blib/lib/Image/ExifTool/BuildTagLookup.pm
cp lib/Image/ExifTool/AES.pm blib/lib/Image/ExifTool/AES.pm
cp lib/Image/ExifTool/Casio.pm blib/lib/Image/ExifTool/Casio.pm
- Type sudo make install
root@kali:/home/iicybersecurity/Downloads/Image-ExifTool-11.29# sudo make install
Manifying 1 pod document
Manifying 34 pod documents
Manifying 33 pod documents
Manifying 33 pod documents
Manifying 32 pod documents
Manifying 32 pod documents
Manifying 14 pod documents
Installing /usr/local/share/perl/5.26.2/Image/ExifTool.pm
Installing /usr/local/share/perl/5.26.2/Image/ExifTool.pod
Installing /usr/local/share/perl/5.26.2/Image/ExifTool/MIEUnits.pod
Installing /usr/local/share/perl/5.26.2/Image/ExifTool/PanasonicRaw.pm
Installing /usr/local/share/perl/5.26.2/Image/ExifTool/MIFF.pm
Installing /usr/local/share/perl/5.26.2/Image/ExifTool/Scalado.pm
- Type exiftool <image with supported format>
- Type exiftool IMG_20190306_115257.jpg
- For checking supported formats go to : https://www.sno.phy.queensu.ca/~phil/exiftool/TagNames/index.html
root@kali:/home/iicybersecurity/Downloads/Image-ExifTool-11.29# exiftool IMG_20190306_115257.jpg
ExifTool Version Number : 11.29
File Name : IMG_20190306_115257.jpg
Directory : .
File Size : 3.9 MB
File Modification Date/Time : 2019:03:06 01:27:39-05:00
File Access Date/Time : 2019:03:06 01:27:39-05:00
File Inode Change Date/Time : 2019:03:06 01:27:39-05:00
File Permissions : rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
Exif Byte Order : Big-endian (Motorola, MM)
Modify Date : 2019:03:06 11:52:57
GPS Time Stamp : 06:22:57
GPS Altitude Ref : Unknown (2)
GPS Date Stamp : 2019:03:06
Camera Model Name : Redmi Note 4
Y Cb Cr Positioning : Centered
Resolution Unit : inches
Y Resolution : 72
Software : mido-user 7.0 NRD90M V10.2.3.0.NCFMIXM release-keys
Color Space : sRGB
F Number : 2.0
Create Date : 2019:03:06 11:52:57
Focal Length : 3.6 mm
Aperture Value : 2.0
Exposure Mode : Auto
Sub Sec Time Digitized : 851637
Exif Image Height : 2340
Focal Length In 35mm Format : 21 mm
Scene Capture Type : Standard
Scene Type : Directly photographed
Sub Sec Time Original : 851637
Exposure Program : Not Defined
White Balance : Auto
Exif Image Width : 4160
Sub Sec Time : 851637
Shutter Speed Value : 1/40
Metering Mode : Center-weighted average
Date/Time Original : 2019:03:06 11:52:57
Components Configuration : Y, Cb, Cr, -
Exif Version : 0220
Flash : Off, Did not fire
Interoperability Index : R98 - DCF basic file (sRGB)
Interoperability Version : 0100
Brightness Value : 0
ISO : 125
Sensing Method : One-chip color area
Flashpix Version : 0100
Exposure Time : 1/40
X Resolution : 72
Make : Xiaomi
Thumbnail Length : 6954
Thumbnail Offset : 964
Compression : JPEG (old-style)
Image Width : 4160
Image Height : 2340
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Aperture : 2.0
GPS Date/Time : 2019:03:06 06:22:57Z
Image Size : 4160x2340
Megapixels : 9.7
Scale Factor To 35 mm Equivalent: 5.9
Shutter Speed : 1/40
Create Date : 2019:03:06 11:52:57.851637
Date/Time Original : 2019:03:06 11:52:57.851637
Modify Date : 2019:03:06 11:52:57.851637
Thumbnail Image : (Binary data 6954 bytes, use -b option to extract)
Circle Of Confusion : 0.005 mm
Field Of View : 81.2 deg
Focal Length : 3.6 mm (35 mm equivalent: 21.0 mm)
Hyperfocal Distance : 1.25 m
Light Value : 7.0
- After executing above query, exiftool has extracted lot of information from the photo which can be used in further hacking attacks.
- Exiftool has extracted device information from which the photo was clicked. Other information of image details which are commonly found in any device. Mainly exiftool extract all settings of the camera which are used while capturing photo.
Extracting GPS Coordinates with Exiftool :-
- Type exiftool <image with supported format>
- Type exiftool IMG_20190306_120407.jpg
root@kali:/home/iicybersecurity/Downloads/Image-ExifTool-11.29# exiftool IMG_20190306_120407.jpg
ExifTool Version Number : 11.29
File Name : IMG_20190306_120407.jpg
Directory : .
File Size : 3.2 MB
File Modification Date/Time : 2019:03:06 01:38:09-05:00
File Access Date/Time : 2019:03:06 01:38:09-05:00
File Inode Change Date/Time : 2019:03:06 01:38:09-05:00
File Permissions : rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
Exif Byte Order : Little-endian (Intel, II)
Exposure Time : 1/50
F Number : 1.9
Exposure Program : Program AE
ISO : 365
Exif Version : 0220
Date/Time Original : 2019:03:06 12:04:07
Create Date : 2019:03:06 12:04:07
Components Configuration : Y, Cb, Cr, -
Shutter Speed Value : 1/50
Aperture Value : 1.9
Brightness Value : 0.63
Exposure Compensation : 0
Max Aperture Value : 1.9
Subject Distance : 0.463 m
Metering Mode : Center-weighted average
Flash : Off, Did not fire
Focal Length : 3.9 mm
Warning : [minor] Unrecognized MakerNotes
Sub Sec Time : 800841
Sub Sec Time Original : 800841
Sub Sec Time Digitized : 800841
Flashpix Version : 0100
Color Space : sRGB
Exif Image Width : 4032
Exif Image Height : 3024
Interoperability Index : R98 - DCF basic file (sRGB)
Interoperability Version : 0100
Sensing Method : One-chip color area
Scene Type : Directly photographed
Custom Rendered : Custom
Exposure Mode : Auto
White Balance : Auto
Digital Zoom Ratio : 0
Focal Length In 35mm Format : 24 mm
Scene Capture Type : Standard
Contrast : Normal
Saturation : Normal
Sharpness : Normal
Subject Distance Range : Macro
GPS Version ID : 2.2.0.0
GPS Latitude Ref : North
GPS Longitude Ref : East
GPS Altitude Ref : Below Sea Level
GPS Time Stamp : 06:34:01
GPS Dilution Of Precision : 16.804
GPS Processing Method : fused
GPS Date Stamp : 2019:03:06
Make : Xiaomi
Camera Model Name : Poco F1
Orientation : Horizontal (normal)
X Resolution : 72
Y Resolution : 72
Resolution Unit : inches
Software : HDR+ 1.0.220943774z
Modify Date : 2019:03:06 12:04:07
Y Cb Cr Positioning : Centered
Compression : JPEG (old-style)
Thumbnail Offset : 24239
Thumbnail Length : 7014
JFIF Version : 1.02
Profile CMM Type :
Profile Version : 4.0.0
Profile Class : Display Device Profile
Color Space Data : RGB
Profile Connection Space : XYZ
Profile Date Time : 2016:12:08 09:38:28
Profile File Signature : acsp
Primary Platform : Unknown ()
CMM Flags : Not Embedded, Independent
Device Manufacturer : Google
Device Model :
Device Attributes : Reflective, Glossy, Positive, Color
Rendering Intent : Perceptual
Connection Space Illuminant : 0.9642 1 0.82491
Profile Creator : Google
Profile ID : 75e1a6b13c34376310c8ab660632a28a
Profile Description : sRGB IEC61966-2.1
Profile Copyright : Copyright (c) 2016 Google Inc.
Media White Point : 0.95045 1 1.08905
Media Black Point : 0 0 0
Red Matrix Column : 0.43604 0.22249 0.01392
Green Matrix Column : 0.38512 0.7169 0.09706
Blue Matrix Column : 0.14305 0.06061 0.71391
Red Tone Reproduction Curve : (Binary data 32 bytes, use -b option to extract)
Chromatic Adaptation : 1.04788 0.02292 -0.05019 0.02959 0.99048 -0.01704 -0.00922 0.01508 0.75168
Blue Tone Reproduction Curve : (Binary data 32 bytes, use -b option to extract)
Green Tone Reproduction Curve : (Binary data 32 bytes, use -b option to extract)
Image Width : 4032
Image Height : 3024
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Aperture : 1.9
GPS Altitude : 0 m Above Sea Level
GPS Date/Time : 2019:03:06 06:34:01Z
GPS Latitude : 28 deg 36' 42.90" N
GPS Longitude : 77 deg 3' 37.10" E
GPS Position : 28 deg 18' 42.63" N, 34 deg 0'
Image Size : 4032x3024
Megapixels : 12.2
Scale Factor To 35 mm Equivalent: 6.1
Shutter Speed : 1/50
Create Date : 2019:03:06 12:04:07.800841
Date/Time Original : 2019:03:06 12:04:07.800841
Modify Date : 2019:03:06 12:04:07.800841
Thumbnail Image : (Binary data 7014 bytes, use -b option to extract)
Circle Of Confusion : 0.005 mm
Depth Of Field : 0.28 m (0.36 - 0.64 m)
Field Of View : 73.7 deg
Focal Length : 3.9 mm (35 mm equivalent: 24.0 mm)
Hyperfocal Distance : 1.66 m
Light Value : 5.6
- Above query has extracted information like camera settings which are used while capturing image. Moreover exiftool has gathered the device name.
- The most important aspect exiftool has gathered GPS coordinates which can be used to track down the target. The above information can be used in further hacking activities.
- The GPS coordinates can be used to open current location of the target. For opening GPS coordinates you can use Google Maps. Go to : https://www.google.com/maps & type GPS Longitude & Latitude.
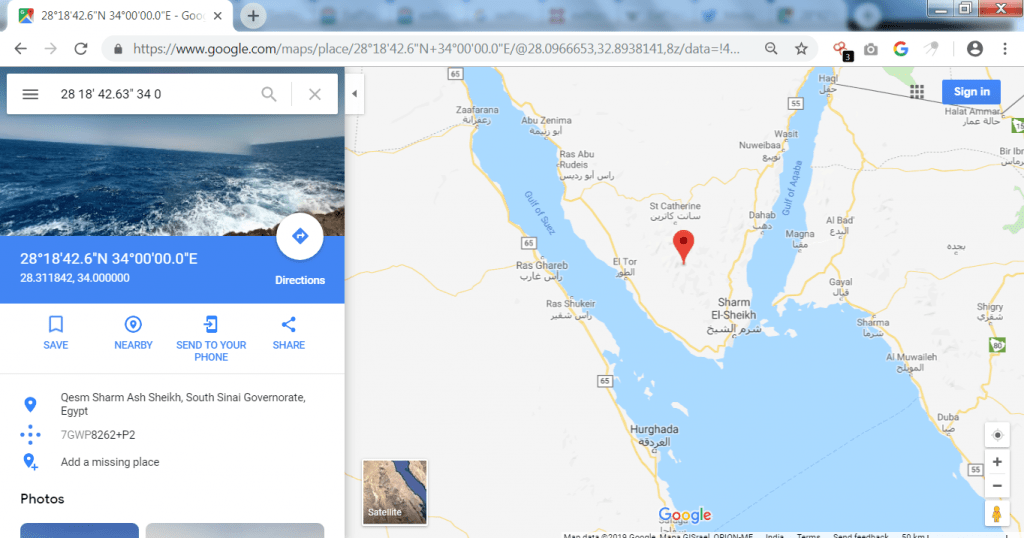
- As you can see above screenshot shows the exact location of the target. For gathering location save location must be enabled.
- Note : Most of the users always kept their location turn on.
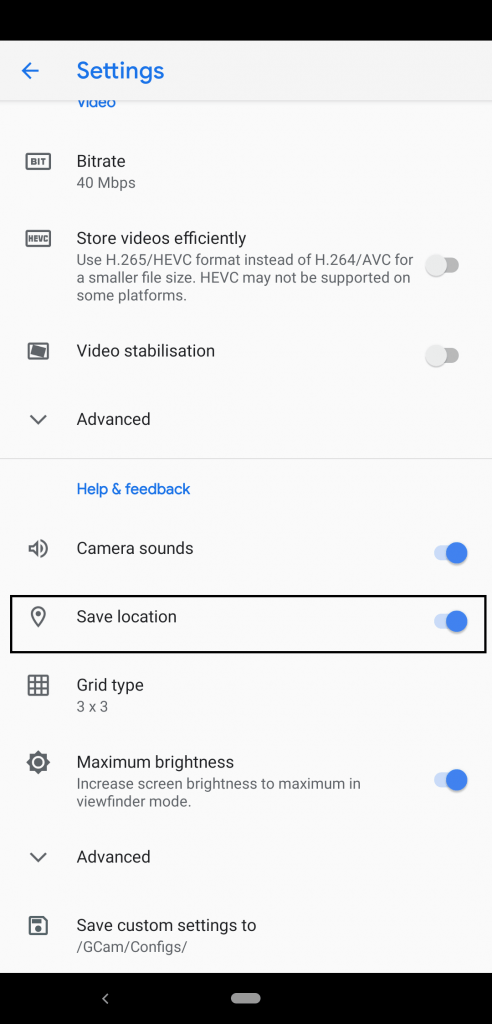
Extracting Information From Social Networking :-
- Here we have used Instagram the main platform for sharing your photos. Everyone uses instagram but not everyone is aware what information can be used to attack their targets.
- We have used photos to scan with exiftool. When one photo is scanned some information which found are very minimal.
root@kali:/home/iicybersecurity/Downloads/Image-ExifTool-11.29# exiftool dk.jpg
ExifTool Version Number : 11.29
File Name : dk2.jpg
Directory : .
File Size : 115 kB
File Modification Date/Time : 2019:03:06 02:57:29-05:00
File Access Date/Time : 2019:03:06 02:57:29-05:00
File Inode Change Date/Time : 2019:03:06 02:57:29-05:00
File Permissions : rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
Current IPTC Digest : d340ec7460476feba68368a861de18bb
Special Instructions : FBMD23000969010000125b00005a750000a68f000031db00005f23010047320100e6a001001ac00100b8cc0100
Image Width : 1080
Image Height : 1350
Encoding Process : Progressive DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 1080x1350
Megapixels : 1.5
- The above information does not show any fingerprint which can be used in further analysis. Because whenever we upload photos on the social networking or on another sites, as per the ethical hacking researcher of International Institute of Cyber Security the metadata of photo get stripped. To demonstrate we tried to extract information nothing was found except some common information.
Extract Information of Recorded Video From Smartphone :-
- For extracting information from the video we have recorded video from the smartphone & now we will extract information using exiftool.
- Type exiftool <image with supported format>.
- Type exiftool VID_20190306_173151.mp4
root@kali:/home/iicybersecurity/Downloads/Image-ExifTool-11.29# exiftool VID_20190306_173151.mp4
ExifTool Version Number : 11.29
File Name : VID_20190306_173151.mp4
Directory : .
File Size : 10 MB
File Modification Date/Time : 2019:03:06 07:06:16-05:00
File Access Date/Time : 2019:03:06 07:05:00-05:00
File Inode Change Date/Time : 2019:03:06 07:06:16-05:00
File Permissions : rw-r--r--
File Type : MP4
File Type Extension : mp4
MIME Type : video/mp4
Major Brand : MP4 v2 [ISO 14496-14]
Minor Version : 0.0.0
Compatible Brands : isom, mp42
Movie Header Version : 0
Create Date : 2019:03:06 12:01:56
Modify Date : 2019:03:06 12:01:56
Time Scale : 1000
Duration : 3.99 s
Preferred Rate : 1
Preferred Volume : 100.00%
Preview Time : 0 s
Preview Duration : 0 s
Poster Time : 0 s
Selection Time : 0 s
Selection Duration : 0 s
Current Time : 0 s
Next Track ID : 3
GPS Coordinates : 28 deg 18' 42.63" N, 34 deg 0' 36.96" E
Com Android Version : 9
Com Android Manufacturer : XIAOMI
Com Android Model : POCO F1
Com Android Video Temporal layers count: (Binary data 4 bytes, use -b option to extract)
Com Android Capture Fps : 60
Track Header Version : 0
Track Create Date : 2019:03:06 12:01:56
Track Modify Date : 2019:03:06 12:01:56
Track ID : 1
Track Duration : 3.99 s
Track Layer : 0
Track Volume : 0.00%
Image Width : 1920
Image Height : 1080
Graphics Mode : srcCopy
Op Color : 0 0 0
Compressor ID : avc1
Source Image Width : 1920
Source Image Height : 1080
X Resolution : 72
Y Resolution : 72
Bit Depth : 24
Pixel Aspect Ratio : 65536:65536
Color Representation : nclx 1 1 1
Video Frame Rate : 59.954
Matrix Structure : 1 0 0 0 1 0 0 0 1
Media Header Version : 0
Media Create Date : 2019:03:06 12:01:56
Media Modify Date : 2019:03:06 12:01:56
Media Time Scale : 48000
Media Duration : 3.97 s
Handler Type : Audio Track
Handler Description : SoundHandle
Balance : 0
Audio Format : mp4a
Audio Channels : 2
Audio Bits Per Sample : 16
Audio Sample Rate : 48000
Movie Data Size : 9734044
Movie Data Offset : 810850
Avg Bitrate : 19.5 Mbps
GPS Latitude : 28 deg 36' 42.90" N
GPS Longitude : 77 deg 3' 37.10" E
Image Size : 1920x1080
Megapixels : 2.1
Rotation : 90
GPS Position : 28 deg 18' 42.63" N, 34 deg 0'
- Above query has extracted information like camera settings which are used while capturing image. Moreover exiftool has gathered the device name.
- The most important aspect exiftool has gathered GPS coordinates which can be used to track down the target. The above information can be used in further hacking activities.
- The GPS coordinates can be used to open current location of the target. For opening GPS coordinates you can use Google Maps. Go to : https://www.google.com/maps & type GPS Longitude & Latitude.
Extracting Information With Imago :-
- The tool is tested on Kali Linux 2018.4
- For cloning tool type git clone https://github.com/redaelli/imago-forensics.git
- cd imago-forensics
- Type pip install -r requirements.txt
- Type cd imago
- Type python imago.py –help
root@kali:/home/iicybersecurity/Downloads/imago-forensics/imago# python imago.py --help
#
imago.py
Digital evidences from images!
Made with <3 by Matteo Redaelli
Twitter: @solventred
#
usage: imago.py [-h] -i INPUT [-x] [-g] [-e] [-n] [-d {md5,sha256,sha512,all}]
[-p {ahash,phash,dhash,whash,all}] [-o OUTPUT] [-s]
[-t {jpeg,tiff}]
optional arguments:
-h, --help show this help message and exit
-i INPUT, --input INPUT
Input directory path
-x, --exif Extract exif metadata
-g, --gps Extract, parse and convert to coordinates, GPS exif
metadata from images (if any)It works only with JPEG.
-e, --ela Extract, Error Level Analysis image,It works only with
JPEG. BETA
-n, --nude Detect Nudity, It works only with JPEG, BETA
-d {md5,sha256,sha512,all}, --digest {md5,sha256,sha512,all}
Calculate perceptual image hashing
-p {ahash,phash,dhash,whash,all}, --percentualhash {ahash,phash,dhash,whash,all}
Calculate hash digest
-o OUTPUT, --output OUTPUT
Output directory path
-s, --sqli Keep SQLite file after the computation
-t {jpeg,tiff}, --type {jpeg,tiff}
Select the image, this flag can be JPEG or TIFF, if
this argument it is not provided, imago will process
all the image types(i.e. JPEG, TIFF)
- Type python imago.py -i /home/iicybersecurity/Downloads/imago-forensics/ -o /home/iicybersecurity/Downloads/imago-forensics/imago -x -s -t jpeg -d all
- You can download any image for doing image forensics. We have downloaded random images to show you.
root@kali:/home/iicybersecurity/Downloads/imago-forensics/imago# python imago.py -i /home/iicybersecurity/Downloads/imago-forensics/ -o /home/iicybersecurity/Downloads/imago-forensics/imago -x -s -t jpeg -d all
#
imago.py
Digital evidences from images!
Made with <3 by Matteo Redaelli
Twitter: @solventred
#
Processing /home/iicybersecurity/Downloads/imago-forensics/girl2.jpeg
Extraction of basic information: /home/iicybersecurity/Downloads/imago-forensics/girl2.jpeg
Calculating md5 of: /home/iicybersecurity/Downloads/imago-forensics/girl2.jpeg
Calculating sha256 of: /home/iicybersecurity/Downloads/imago-forensics/girl2.jpeg
Calculating sha512 of: /home/iicybersecurity/Downloads/imago-forensics/girl2.jpeg
Extraction of EXIF data from: /home/iicybersecurity/Downloads/imago-forensics/girl2.jpeg
Processing of /home/iicybersecurity/Downloads/imago-forensics/girl2.jpeg completed!
Processing /home/iicybersecurity/Downloads/imago-forensics/imago.jpeg
Extraction of basic information: /home/iicybersecurity/Downloads/imago-forensics/imago.jpeg
Calculating md5 of: /home/iicybersecurity/Downloads/imago-forensics/imago.jpeg
Calculating sha256 of: /home/iicybersecurity/Downloads/imago-forensics/imago.jpeg
Calculating sha512 of: /home/iicybersecurity/Downloads/imago-forensics/imago.jpeg
Extraction of EXIF data from: /home/iicybersecurity/Downloads/imago-forensics/imago.jpeg
Processing of /home/iicybersecurity/Downloads/imago-forensics/imago.jpeg completed!
Processing /home/iicybersecurity/Downloads/imago-forensics/hindu.jpeg
Extraction of basic information: /home/iicybersecurity/Downloads/imago-forensics/hindu.jpeg
Calculating md5 of: /home/iicybersecurity/Downloads/imago-forensics/hindu.jpeg
Calculating sha256 of: /home/iicybersecurity/Downloads/imago-forensics/hindu.jpeg
Calculating sha512 of: /home/iicybersecurity/Downloads/imago-forensics/hindu.jpeg
Extraction of EXIF data from: /home/iicybersecurity/Downloads/imago-forensics/hindu.jpeg
Processing of /home/iicybersecurity/Downloads/imago-forensics/hindu.jpeg completed!
Processing /home/iicybersecurity/Downloads/imago-forensics/kevin.jpeg
Extraction of basic information: /home/iicybersecurity/Downloads/imago-forensics/kevin.jpeg
Calculating md5 of: /home/iicybersecurity/Downloads/imago-forensics/kevin.jpeg
Calculating sha256 of: /home/iicybersecurity/Downloads/imago-forensics/kevin.jpeg
Calculating sha512 of: /home/iicybersecurity/Downloads/imago-forensics/kevin.jpeg
Extraction of EXIF data from: /home/iicybersecurity/Downloads/imago-forensics/kevin.jpeg
Processing of /home/iicybersecurity/Downloads/imago-forensics/kevin.jpeg completed!
Processing /home/iicybersecurity/Downloads/imago-forensics/girl.jpeg
Extraction of basic information: /home/iicybersecurity/Downloads/imago-forensics/girl.jpeg
Calculating md5 of: /home/iicybersecurity/Downloads/imago-forensics/girl.jpeg
Calculating sha256 of: /home/iicybersecurity/Downloads/imago-forensics/girl.jpeg
Calculating sha512 of: /home/iicybersecurity/Downloads/imago-forensics/girl.jpeg
Extraction of EXIF data from: /home/iicybersecurity/Downloads/imago-forensics/girl.jpeg
Processing of /home/iicybersecurity/Downloads/imago-forensics/girl.jpeg completed!
Processing /home/iicybersecurity/Downloads/imago-forensics/hindu2.jpeg
Extraction of basic information: /home/iicybersecurity/Downloads/imago-forensics/hindu2.jpeg
Calculating md5 of: /home/iicybersecurity/Downloads/imago-forensics/hindu2.jpeg
Calculating sha256 of: /home/iicybersecurity/Downloads/imago-forensics/hindu2.jpeg
Calculating sha512 of: /home/iicybersecurity/Downloads/imago-forensics/hindu2.jpeg
Extraction of EXIF data from: /home/iicybersecurity/Downloads/imago-forensics/hindu2.jpeg
Processing of /home/iicybersecurity/Downloads/imago-forensics/hindu2.jpeg completed!
Processing /home/iicybersecurity/Downloads/imago-forensics/t
- After executing the above query, imago forensics has created two files which shows information of the image.
- .csv & metadata.db files are created using imago forensics.
root@kali:/home/iicybersecurity/Downloads/imago-forensics/imago# ls
extractor.py extractor.pyc hash.py helper.py helper.pyc imago.csv imago.py init.py main.py metadata.db
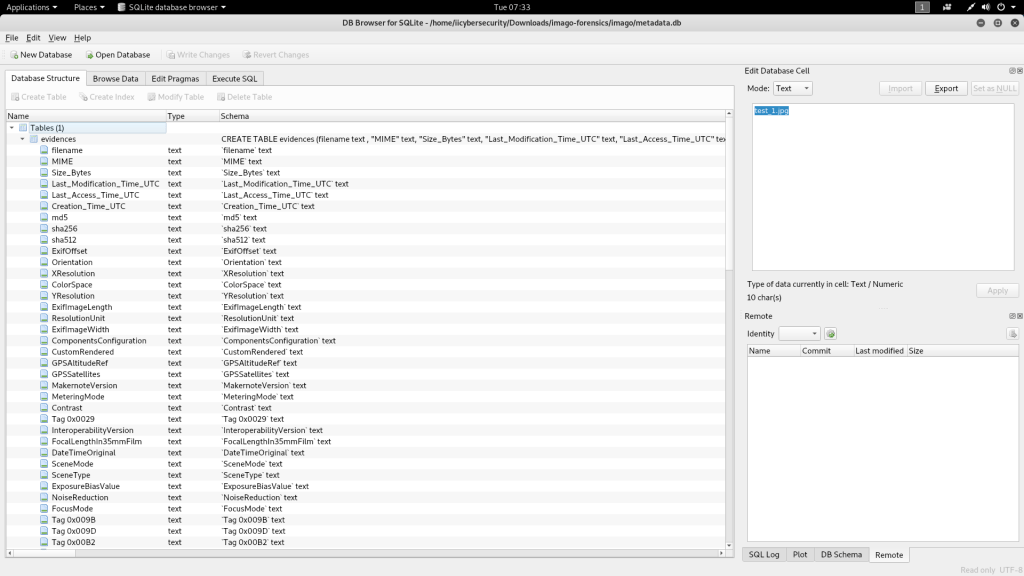
- You can open metadata.db in SQLite browser. For opening go to Kali Linux search & type sqlite
- Open the metadata.db by going to the imago-forensics locations. click on Open Database
- The above screenshot shows evidences which consists of data which consists of columns with extracted data. These data can be used in further hacking attacks.
- For viewing in tabular format click on Browser data.
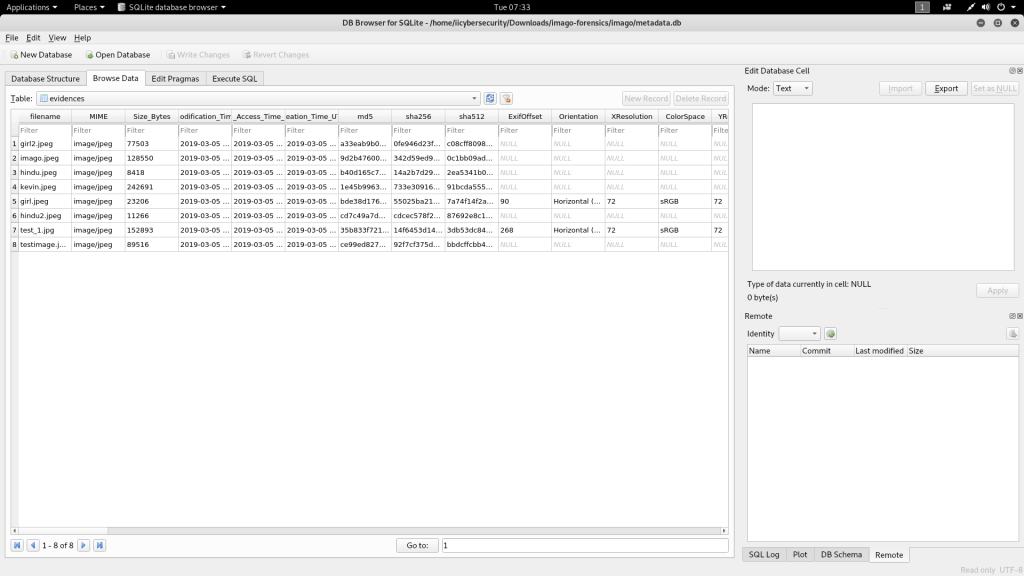
- Imago has extracted data which can be considered in initial phase of pentesting.
Ethical hacking researcher of international institute of cyber security says today every image consist of useful information which are used to design further attacks.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











