The US Computer Emergency Readiness Team (US-CERT) has just released a security alert related to the presence of at least two critical vulnerabilities in the programmable logic controllers (PLC) of technology company Siemens. According to the vulnerability testing report, exploiting these flaws would allow remote threat actors to deploy denial of service (DoS) attacks, among other tasks, by abusing Port 161/UDP. The report was prepared by Artem Zinenko from security firm Kaspersky.
SOURCE: US-CERT
The first of the reported flaws, tracked as CVE-2015-5621, is an error in SNMP message handling that would allow a remote hacker to generate a DoS condition and even execute arbitrary code using a specially crafted package, which must be sent to Port 161/UDP (SNMP). The vulnerability has received a score of 7.5/10 on the Common Vulnerability Scoring System (CVSS) scale.
On the other hand, the second vulnerability testing report is a NULL pointer exception error within the SMNP handling code; exploiting this flaw would allow an authenticated remote threat actor to generate a DoS condition by sending a specially crafted package to Port 161/UDP (SNMP). The flaw, tracked as CVE-2018-18065, received a score of 6.5/10 on the CVSS scale.
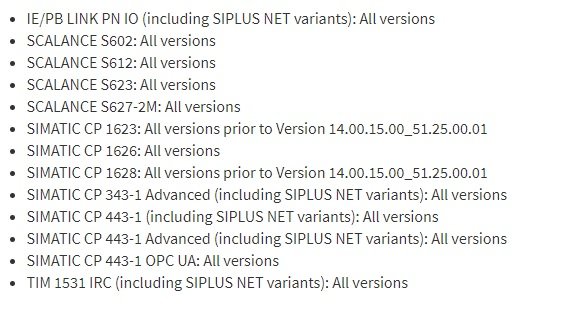
The affected products are used in various industrial branches, such as the chemical, food, health, transport and wastewater management industries throughout the world. In response to reports, the German company released a set of updates for the affected products, so administrators of these solutions are recommended to upgrade to the latest available versions. If the affected systems were unable to update promptly, Siemens‘ vulnerability testing team prepared some functional workarounds:
- Disable SNMP, in case the affected product allows it. SNMP disabling completely mitigates exploiting risks
- Protect network access to Port 161/UDP on affected devices
- Apply the concept of cellular protection and implement in-depth defense
- Use VPN to protect network communication
The International Institute of Cyber Security (IICS) suggests administrators protect network access with relevant solutions, as well as being aware of security recommendations issued by the manufacturer, as these vulnerabilities appear steadily.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











